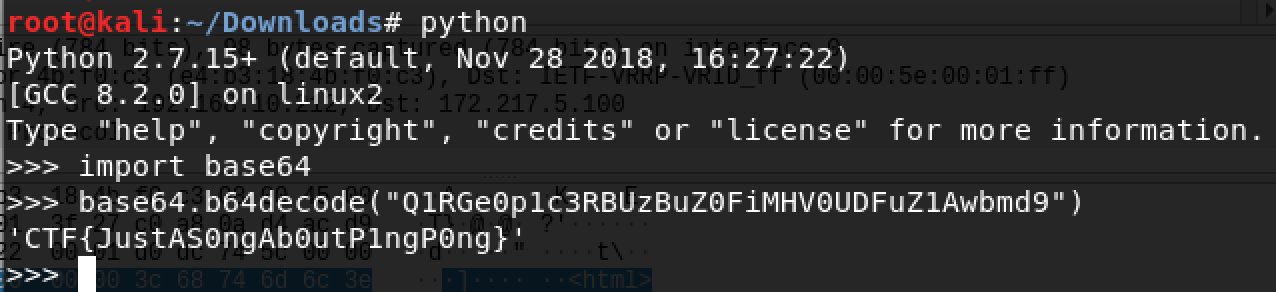
- This Ctf clashed with TAMU, I was not able to take a number of challenges. I will update some solved already and solve + update some soon (after the ctf.)
Trivia
- Challenge
- Flag:
passport
- This was a good reference to check out some authentication videos..
* https://www.pri.org/stories/2017-12-13/my-voice-my-passport-verify-me
* https://www.youtube.com/watch?v=tkNx80RUtEc
* https://www.annedougherty.com/my-voice-is-my-passport-verify-me-the-webs-password-and-userid-creation-problem/
Table Tennis
- Challenge
- Analysis
- Packet capture shows TLS, DNS and ICMP prominently. We cannot do much with TLS other than looking at the handshake and certs. Investigating the DNS and ICMP.
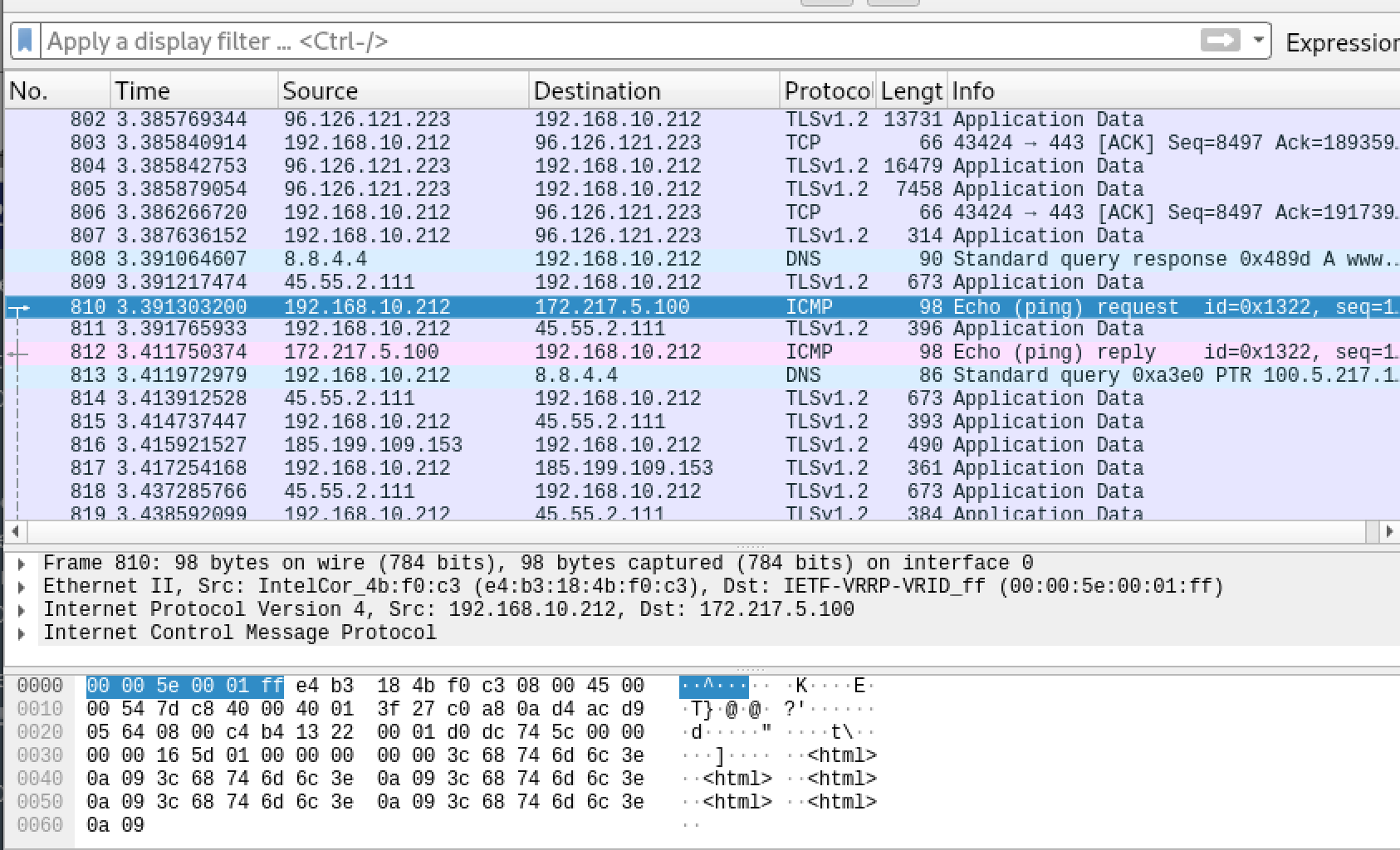
- Here we can see a number of ICMP packets exchanged which should be the covert information exchanged
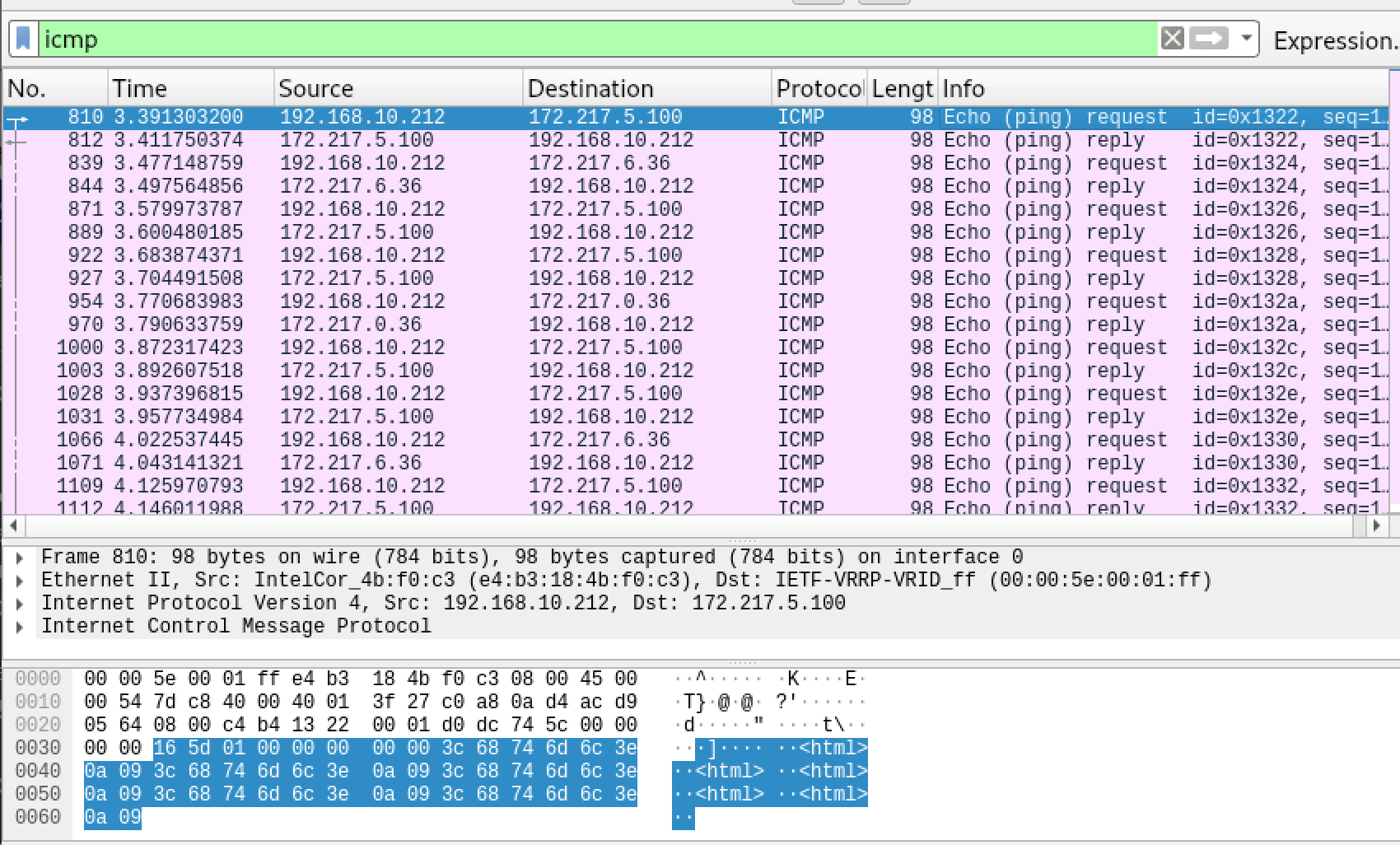
- Read ICMP packets and dump the content (extra payload of ICMP)
from scapy.all import *
capture_read = rdpcap("out.pcapng")
for packet in capture_read:
if ICMP in packet:
data = str(packet[Raw]).encode("hex")
print data[-16:].decode("hex"),
- An html page is exchanged as evident by headers and tags, each line of the content is repeated number of times evident from the output. Extract the tags to reconstruct the html or read through the html (knowing about the repetition) to obtain the unique string which might be the flag. (Here it is base64 encoded string)
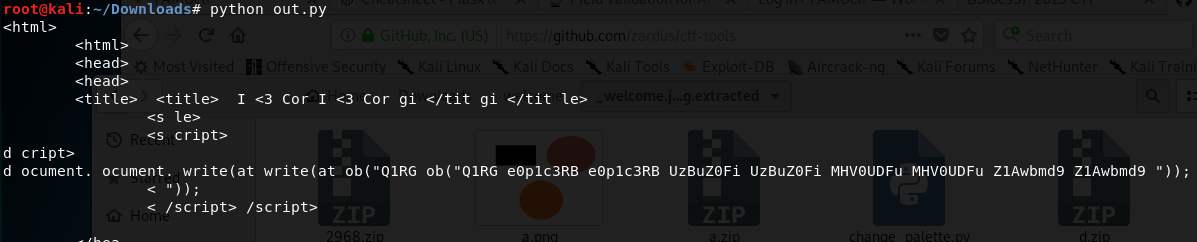
- Flag