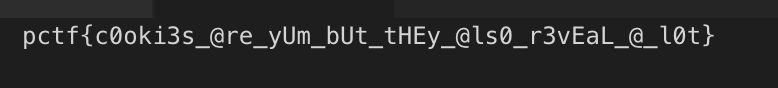
I had a crazy CTF week again which was not anticipated. I also happened to take part in Scale17x Ctfs Ctfs every where!. An amazing experience at the conference and I happened to be brain fried all Sunday evening…
-
I managed to take up a very few questions (just 2!) and will update the writeup. More coming soon as I solve….
-
Pragyan’s Ctf server was ver slow, it was nice they had the
: alternate server address that helped a lot!
Forensics
Welcome
- This was the first welcome challenge and a forensics one. (a bit harder than expected for the first challenge of the ctf)
-
Assumed to be an easy challenge as the name seemed to be the first challenge but challenging and nice stegano!
- Challenge
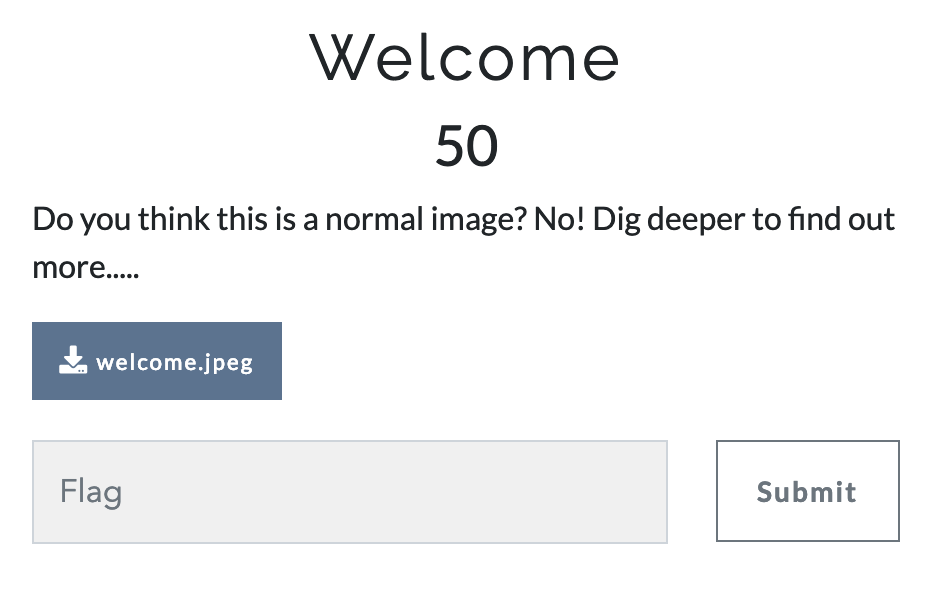
- Initial Forensics Recon - Start with
file, exiftool, imginfo, binwalkas usual
root@kali:~/Downloads# exiftool welcome.jpeg
ExifTool Version Number : 11.16
File Name : welcome.jpeg
Directory : .
File Size : 20 kB
File Modification Date/Time : 2019:03:08 05:29:53-08:00
File Access Date/Time : 2019:03:08 05:29:53-08:00
File Inode Change Date/Time : 2019:03:08 05:29:53-08:00
File Permissions : rw-r--r--
File Type : JPEG
File Type Extension : jpg
MIME Type : image/jpeg
JFIF Version : 1.01
Resolution Unit : inches
X Resolution : 72
Y Resolution : 72
Image Width : 271
Image Height : 186
Encoding Process : Progressive DCT, Huffman coding
Bits Per Sample : 8
Color Components : 3
Y Cb Cr Sub Sampling : YCbCr4:4:4 (1 1)
Image Size : 271x186
Megapixels : 0.050
root@kali:~/Downloads# binwalk welcome.jpeg
DECIMAL HEXADECIMAL DESCRIPTION
--------------------------------------------------------------------------------
0 0x0 JPEG image data, JFIF standard 1.01
10600 0x2968 Zip archive data, at least v2.0 to extract, uncompressed size: 9886, name: d.zip
20483 0x5003 End of Zip archive, footer length: 22
root@kali:~/Downloads/welcome# binwalk -e welcome.jpeg
DECIMAL HEXADECIMAL DESCRIPTION
--------------------------------------------------------------------------------
0 0x0 JPEG image data, JFIF standard 1.01
10600 0x2968 Zip archive data, at least v2.0 to extract, uncompressed size: 9886, name: d.zip
20483 0x5003 End of Zip archive, footer length: 22
root@kali:~/Downloads/welcome# ls
welcome.jpeg _welcome.jpeg.extracted
-
Binwalk threw us interesting files which we could work on. Digging further with extraction
root@kali:~/Downloads/welcome# cd _welcome.jpeg.extracted/ root@kali:~/Downloads/welcome/_welcome.jpeg.extracted# ls 2968.zip d.zip root@kali:~/Downloads/welcome/_welcome.jpeg.extracted# ls 2968.zip a.zip d.zip secret.bmp -
(like a russian doll puzzle) there is another zip which is password protected and a image file called as secret.
Secret.bmpis just a file with some data.root@kali:~/Downloads/welcome/_welcome.jpeg.extracted# cat secret.bmp ......<garbage>...... [8-7.=p54.b=dGhlIHBhc3N3b3JkIGlzOiBoMzExMF90aDNyMyE== _welcome.jpeg.extracted# python Python 2.7.15+ (default, Nov 28 2018, 16:27:22) [GCC 8.2.0] on linux2 Type "help", "copyright", "credits" or "license" for more information. >>> import base64 >>> base64.b64decode("dGhlIHBhc3N3b3JkIGlzOiBoMzExMF90aDNyMyE==") 'the password is: h3110_th3r3!' >>> [5]+ Stopped python -
Ok, We got the password and we extract the password protected zip file
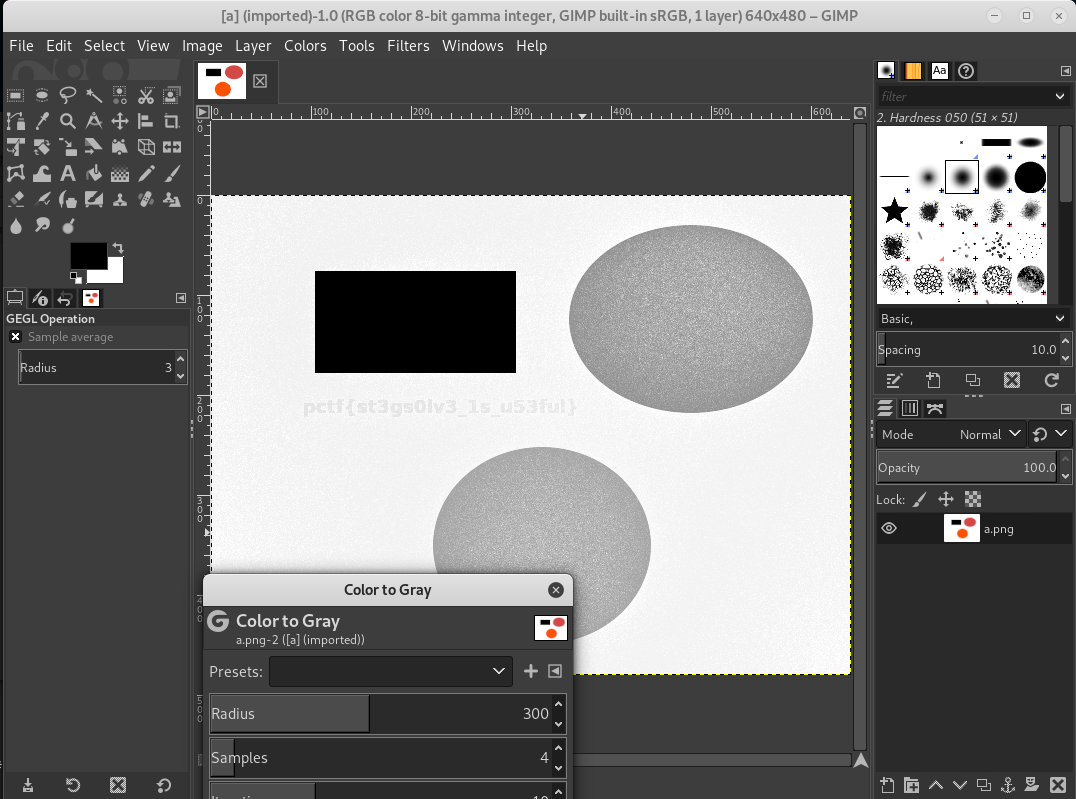
a.zip. We get another imagea.png, which contains no flag and just some figures. Recon again with the result image._welcome.jpeg.extracted# file a.png a.png: PNG image data, 640 x 480, 8-bit/color RGBA, non-interlaced root@kali:~/Downloads/welcome/_welcome.jpeg.extracted# pngcheck a.png OK: a.png (640x480, 32-bit RGB+alpha, non-interlaced, 99.2%). root@kali:~/Downloads/welcome/_welcome.jpeg.extracted# exiftool a.png ExifTool Version Number : 11.16 File Name : a.png Directory : . File Size : 10 kB File Modification Date/Time : 2018:12:30 03:12:53-08:00 File Access Date/Time : 2019:03:08 05:34:35-08:00 File Inode Change Date/Time : 2019:03:08 05:34:30-08:00 File Permissions : rw-r--r-- File Type : PNG File Type Extension : png MIME Type : image/png Image Width : 640 Image Height : 480 Bit Depth : 8 Color Type : RGB with Alpha Compression : Deflate/Inflate Filter : Adaptive Interlace : Noninterlaced Background Color : 0 0 0 Pixels Per Unit X : 2835 Pixels Per Unit Y : 2835 Pixel Units : meters Modify Date : 2018:12:30 11:12:53 Comment : Image Size : 640x480 Megapixels : 0.307 root@kali:~/Downloads/welcome/_welcome.jpeg.extracted# binwalk a.png DECIMAL HEXADECIMAL DESCRIPTION -------------------------------------------------------------------------------- 0 0x0 PNG image, 640 x 480, 8-bit/color RGBA, non-interlaced _welcome.jpeg.extracted# img_stat a.png IMAGE FILE INFORMATION -------------------------------------------- Image Type: raw Size in bytes: 10317 Sector size: 512 -
There seems to be nothing hidden, the flag should be visibly hidden? Tried different techniques with
Stesolve, xxs, change palatte, stegsolve, gimp. -
Using GIMP with gray scale filter gave out the flag.

Web
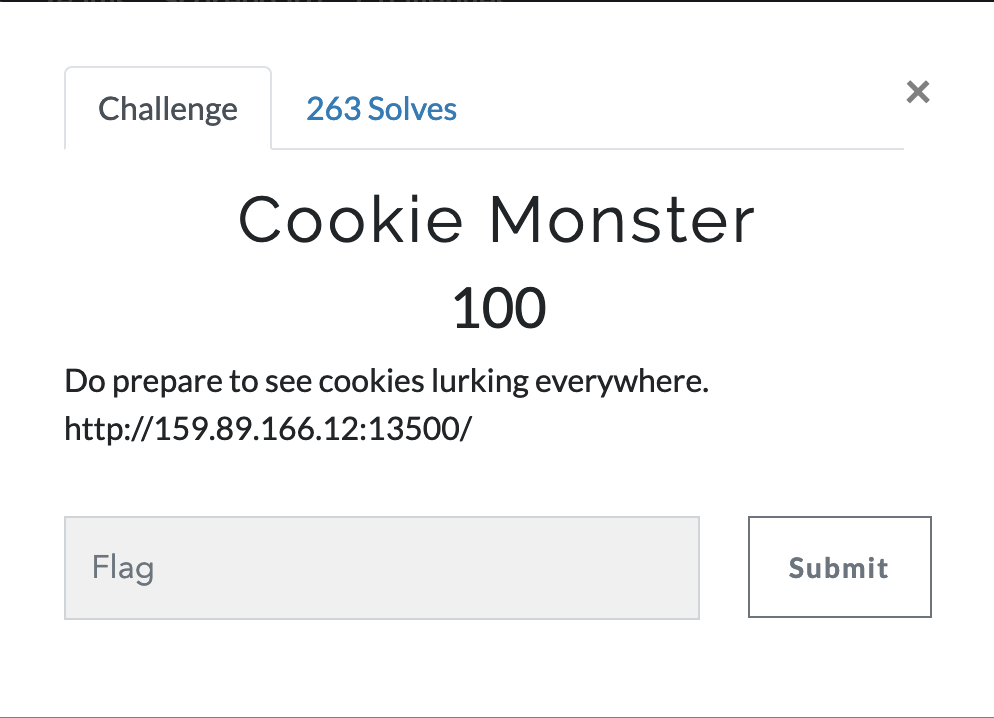
Cookie Monster
- Challenge
- The web app is a static page with nothing amusing in the source code, we receive a cookie for the page.
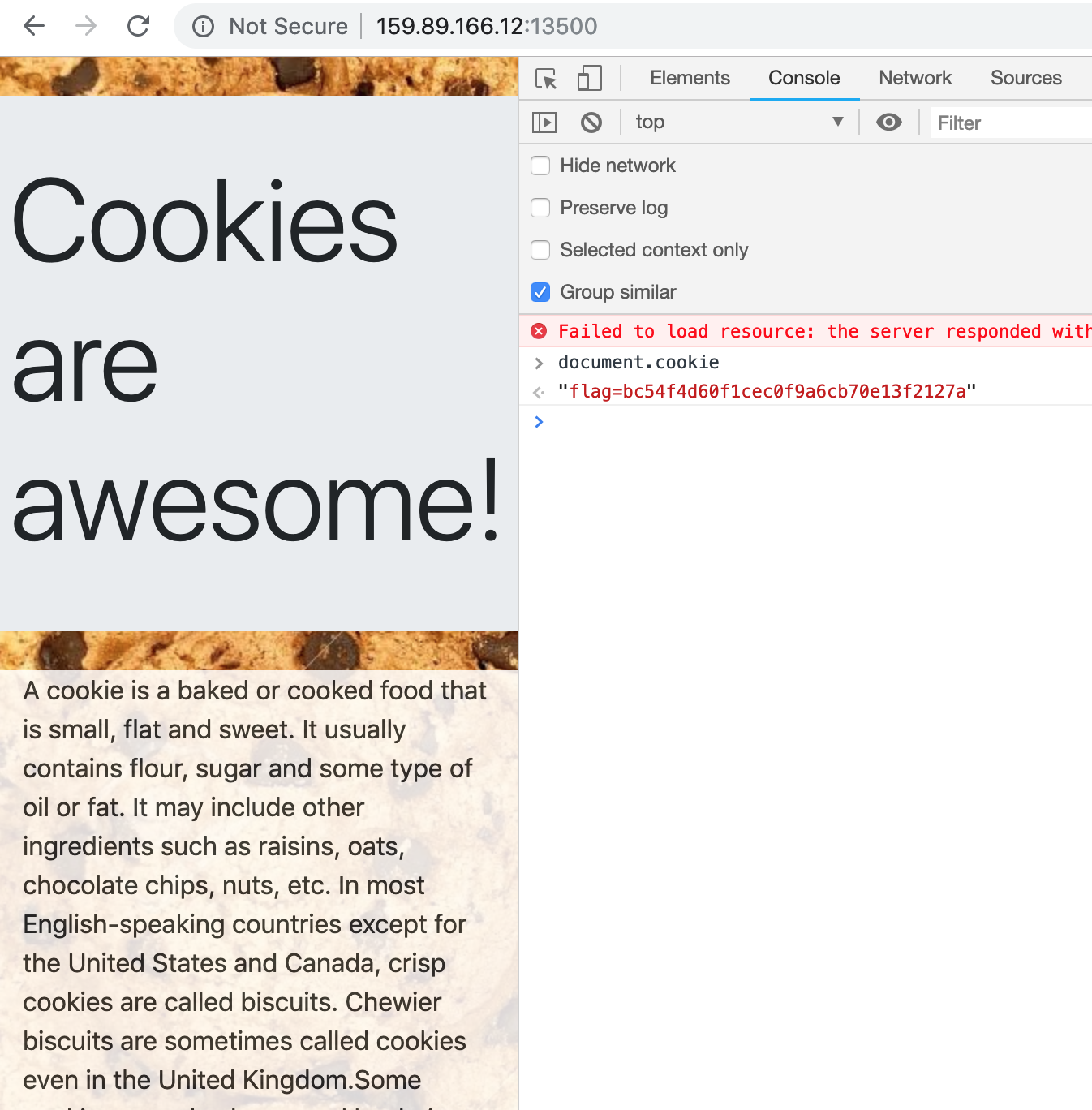
- After playing for sometime, we can see that once the cookie is set subsequent request with the previously set cookie returns us new cookie.
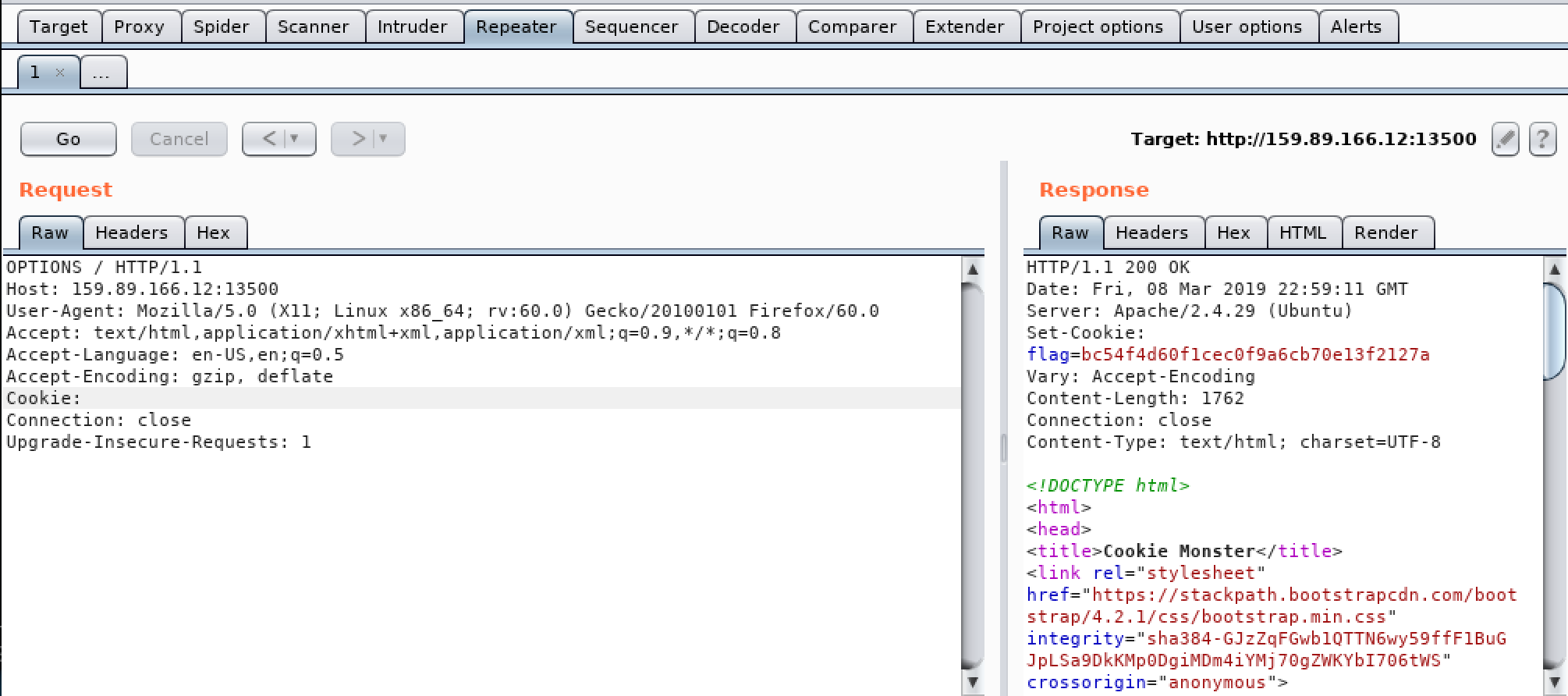
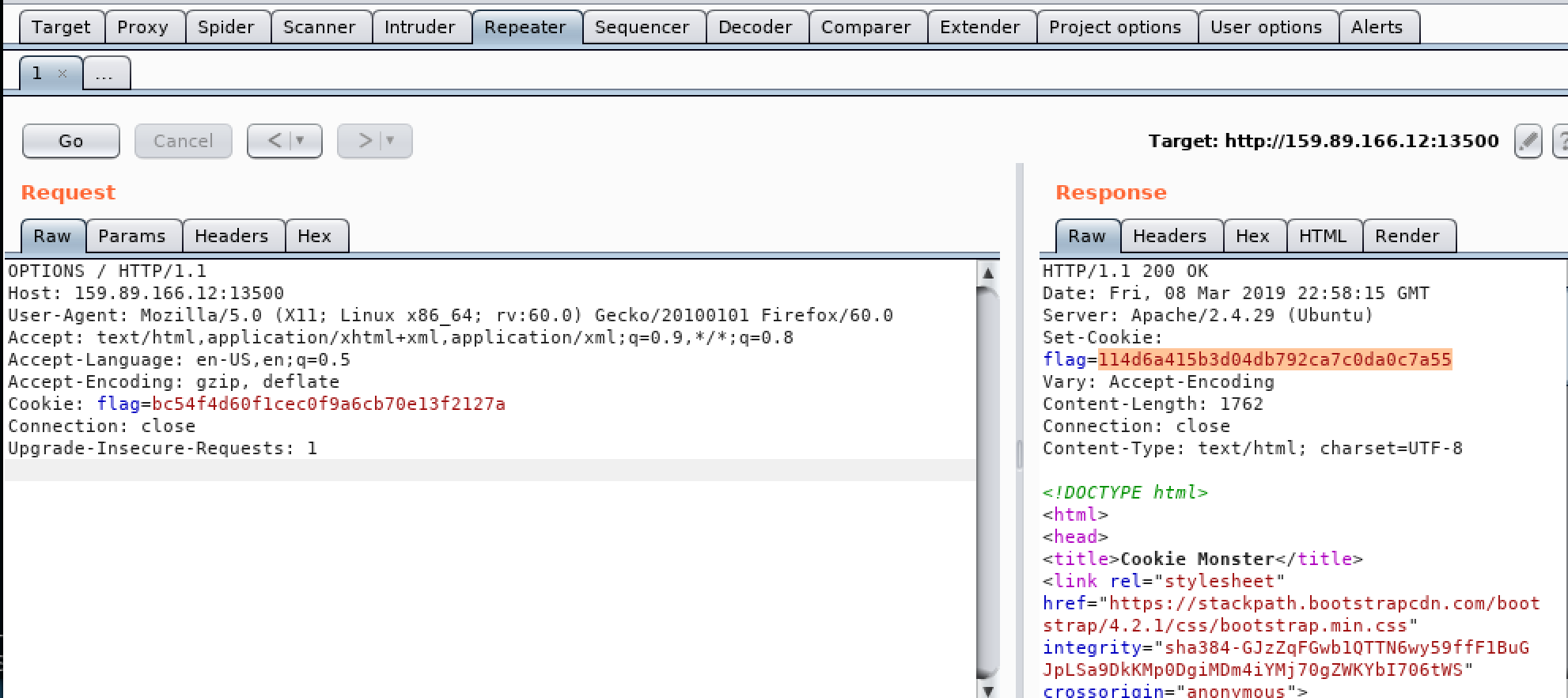
- The trick was, the cookie changes everytime we set the previous cookie we got and make the request
- Examining the cookie value for any encoded string, we find that it is an
MD5 hash - Using hash identifier to ensure the hash type
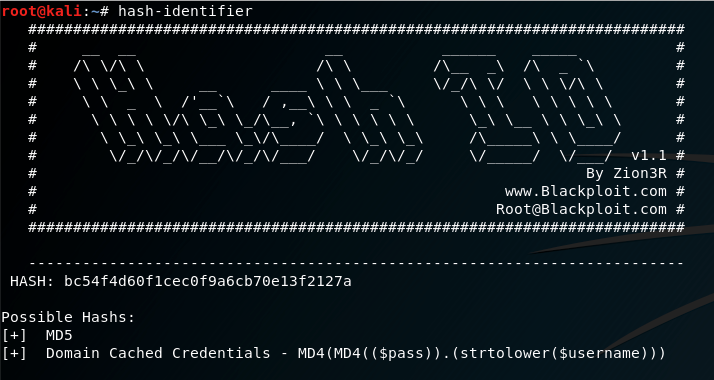
- Cracking the first 2 hashes we find that it is pc and tf ==>
pctf. Using hashkiller online
bc54f4d60f1cec0f9a6cb70e13f2127a pc
114d6a415b3d04db792ca7c0da0c7a55 tf
- Write Script to obtain all the unique hashes crack.py and output below
# Curl Command to send a request with a cookie and receive the new cookie
# * Identified the cookie to be a md5 hash
# * Initial 2 hashes were pc, tf so we have to crack all the hashes to obtain the flag...
"""
curl -i -s -k -X $'OPTIONS' \
-H $'Host: 159.89.166.12:13500' -H $'User-Agent: Mozilla/5.0 (X11; Linux x86_64; rv:60.0) Gecko/20100101 Firefox/60.0' -H $'Accept: text/html,application/xhtml+xml,application/xml;q=0.9,*/*;q=0.8' -H $'Accept-Language: en-US,en;q=0.5' -H $'Accept-Encoding: gzip, deflate' -H $'Cookie: flag=440c5c247c708c6e46783e47e3986889' -H $'Connection: close' -H $'Upgrade-Insecure-Requests: 1' \
-b $'flag=440c5c247c708c6e46783e47e3986889' \
$'http://159.89.166.12:13500/'
"""
# Ref for handling cookies: https://stackoverflow.com/questions/5606083/how-to-set-and-retrieve-cookie-in-http-header-in-python
from urllib import request
cookies = []
response = request.urlopen("http://159.89.166.12:13500")
cookie = response.getheader("Set-Cookie")
while cookie not in cookies:
print(cookie.split("=")[-1])
cookies.append(cookie)
req = request.Request("http://159.89.166.12:13500", headers={"Cookie": cookie})
response = request.urlopen(req)
cookie = response.getheader("Set-Cookie")
- Hashcrackers using hash killer
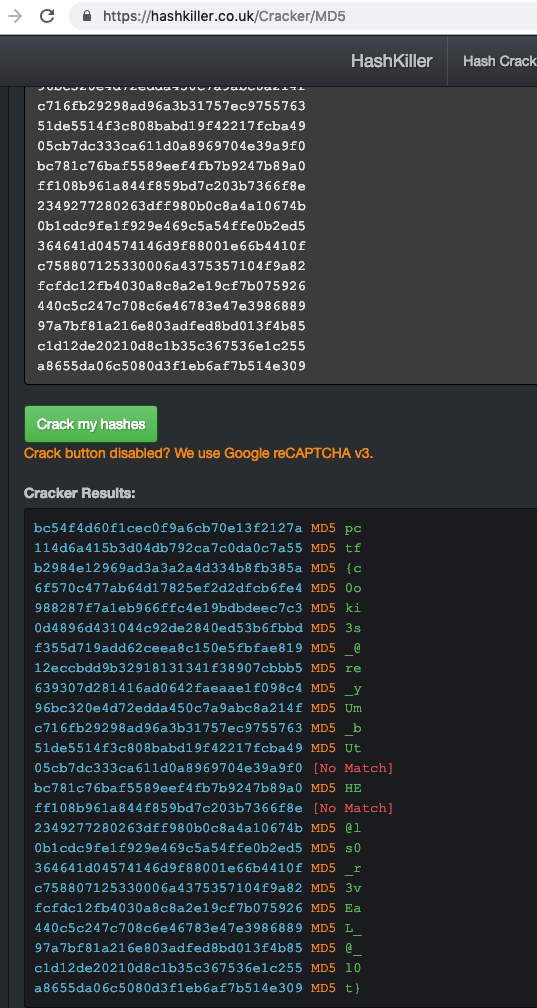
- Crack the hashes, hashlib with rockyou cracked some but online hash cracker hashkiller nailed most of it.
-
For the unmatched hashes,(2), guessed the flag.
- Flag